The exposure of the five major paths of personal information leakage is really unexpected
The occurrence of a series of cases, from Xu Yuyu, a prospective college student in Shandong Province, to a professor in Tsinghua University who was cheated, has made online fraud once again become the focus of public opinion. Various media have reported a series of fraud cases that have occurred in various places. However, media reports are just the tip of the iceberg. Similar things happen every day. The lucky people may only lose some money, while the unlucky people are cheated and split up and their families are broken. Behind these cases is the increasingly rampant disclosure of personal information. In the era of mobile Internet, how should we protect our personal information?
How much do you know about personal information leakage?
Once you enter the network, it is as deep as the sea. Since then, privacy is a passer-by. According to the data released by the China Internet Association, 63.4% of Internet users' call records, online shopping records and other information were leaked; 78.2% of netizens' personal identity information, including name, home address, ID card number and work unit, was disclosed. In terms of individual cases, there are numerous, involving third-party ticket booking systems, well-known hotels, education systems, express companies, taxi hailing software, email mailboxes, and so on. Many hundreds of millions of user information has been leaked, and at least tens of thousands.
Good has cause, evil has effect. The large-scale leakage of personal information has led to an increasing loss of residents' wealth. It is estimated that in 2015, 688 million netizens in China lost 91.5 billion yuan (133 yuan per capita) due to spam messages, fraudulent information and personal information leakage. The bloody data has caused many people of insight to worry about the future: if such information leakage events continue, will 1.3 billion Chinese people "run naked"?
Five ways of personal information disclosure
Tracing back to the source, why does personal information fall into the hands of criminals, and who is leaking our personal information? Suning Financial Research Institute found that there are five main paths for personal information leakage: first, human factors, namely, the company and institutional employees who have mastered the information actively resell the information; Second, the computer was infected with Trojan virus and other malicious software, resulting in personal information being stolen; Third, lawbreakers use website vulnerabilities to invade and steal the database that stores information; Fourth, the user connects free WIFI or scans two-dimensional code at will and is stolen by criminals; Fifthly, the password is simple. "One set of passwords goes global", which greatly facilitates the criminals to "hit the database". Here is a brief explanation:
Enterprise "insider" resells information. In the era of mobile internet and big data, more and more institutions actively collect citizens' personal information and form their own increasingly large databases, such as e-commerce websites, express companies, real estate intermediaries, etc. However, due to the lax internal management system, enterprise "insiders" frequently appear. Some employees are lured by interests and take risks to resell customers' personal information, which really reflects the saying "day and night are the best way to prevent domestic thieves".
Trojans steal information. Among all means of committing crimes, mobile phone trojan SMS has become a common fraud method for criminals. They disguise themselves as school teachers, classmates, and even junior students, and send trojan messages to mobile phone users around them through fake base stations. As soon as users click the SMS link, various online banking accounts, passwords, and SMS verification codes will be stolen by trojans and forwarded to criminals. See the following figure for the specific process:
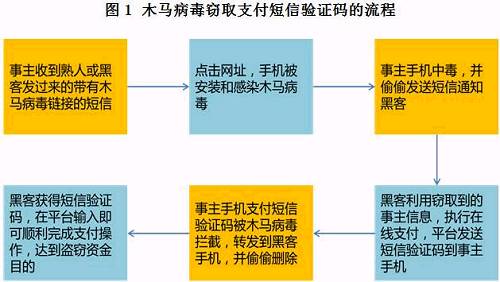
In addition, phishing websites are also a common means for criminals to steal user information. The domain name and page of a phishing website are very similar to those of a normal website. Lawbreakers usually imitate the official website of a bank or telecom operator to induce users to enter personal information on the phishing website.
Steal information by taking advantage of website vulnerabilities. The major websites have been used by criminals due to network loopholes, resulting in the leakage of a large number of users' personal information. Data shows that in 2015, 360's "Sky mending" platform (China's largest vulnerability broadcasting platform) included 1410 vulnerabilities that may cause personal information leakage on websites, involving 1282 websites, and the amount of personal information that may be leaked reached 5.53 billion, which was more than double the 2.36 billion in 2014. If the total number of Chinese netizens is 650 million, this means that in 2015, on average, each Chinese netizen was leaked at least 8 pieces of personal information. More worrisome is that the attitude of these websites to vulnerability repair is not positive, and the overall repair rate is only 8.0%
Free WiFi and QR code are hidden "black hands". "The withered vine, the old tree, the crow, the air-conditioned WiFi watermelon, and the Ge You sofa of the same style will make me lie down there at sunset." This paragraph shows the indispensability of mobile phone and WiFi combination in people's life. Because of this, free WiFi has become a disaster area for privacy leakage. Data shows that Tencent mobile phone butler users have more than 200 million WiFi connections every day, of which about 600000 are connected to risky WiFi every day. Once connected to WiFi fraud, your online banking, payment account, password and other information may be stolen by criminals without your knowledge. Please refer to the following figure for the basic path.
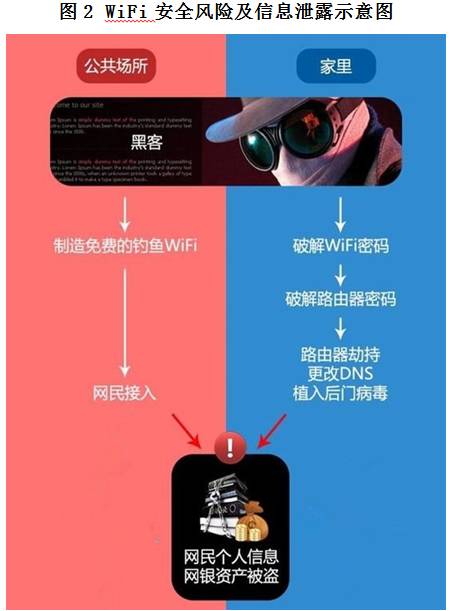
In addition, malicious two-dimensional code is also one of the means of criminals. When a user scans a malicious QR code, it is equivalent to clicking a short message link with a Trojan virus, and the mobile phone will be implanted with a Trojan virus. According to the survey data, the proportion of teenagers aged 7-19 who "scan the QR code frequently without considering whether it is safe" is as high as 40.3%. The login password is simple, unified and easy to crack. One code universal is simple and easy to remember, but there are many security risks. When criminals steal or crack one of your accounts, they will try to log in the corresponding data on other websites or accounts. The professional term is "hit the database". For example, after obtaining your bank account, you can try to log in to Alipay account to trigger the "domino effect". The data shows that 75.93% of netizens in China have the problem of using the same password for multiple accounts, especially for the youth group, which accounts for 82.39%
How to effectively protect personal information?
If information has no value and purpose, no one should be so foolish as to make every effort to collect, disclose or buy such information. According to the survey of Suning Financial Research Institute, there are two kinds of buyers in the personal information trading market: one is formal companies, such as health care products companies, insurance companies, wealth management companies, real estate intermediary companies, decoration companies, private "pheasant universities", various training institutions, etc. They try their best to obtain personal information mainly for marketing needs, Although they have no harmful motive, they still break the law; The other is a fraud gang, whose main purpose is to carry out precise fraud. Sadly, most of the members of the fraud gang are young people between the ages of 15 and 25, and they really want to say to them: "There is no end to the sea of suffering, and it is good to return.".
For law-abiding citizens, in the era of the gradual systematization of personal information disclosure and trafficking, and the growing harm, if the illegal acts of personal information trafficking cannot be effectively curbed, that person's property security is tantamount to wishful thinking.
From a global perspective, although personal information disclosure is a worldwide problem, some foreign practices are still commendable. In the United States, telephone companies or post offices can sell users' phone numbers and home address information to relevant demand parties (such as advertisers), but at the same time, they have set a proactive legal binding clause, that is, citizens can avoid telephone harassment by applying for the "No Call" service of the Federal Trade Commission of the United States. Once there is a violation, every call will be fined 11000 dollars; In Japan, the Five Related Laws of the Personal Information Protection Law effectively regulate the purchase and sale of personal information; In Germany, there are not only the Federal Data Protection Law and the Law on Preventing the Processing and Abuse of Personal Data at the national level, but also the State Data Protection Law at the state level to protect citizens' personal information in an all-round way; In France, the government not only severely punishes the unauthorized collection and use of private information by issuing strict regulations, but also sets up the National Information Management Committee to supervise the abuse of personal information.
A stone from another mountain can be used to attack jade. Our country's personal information protection legislation should also speed up the process. Only by clearly defining the information leakage and trading behavior, and defining the penalty, can we truly form a deterrent effect and cut off the evil hand of information trafficking to a certain extent.
Of course, as individuals, the first thing we need to learn is how to be independent in the era of information "streaking". In my opinion, the most important points are the following four: First, keep personal information properly, especially bank cards, mobile phones and other information carriers, fill in personal information carefully during network registration and real name verification, and do not disclose personal private information such as ID card number, payment account number, mobile phone number at will; The second is to develop the good habit of regularly changing passwords. For important accounts (such as common mailboxes, online payments, chat accounts, etc.), passwords must be set separately. Never use more than one code, and passwords should preferably be set into more complex combinations such as numbers+letters; Third, regularly kill viruses on mobile phones and computers, especially for those who often visit websites of unknown origin; Fourth, do not connect free WiFi at will, do not click on unknown links and scan unknown QR codes in SMS, and do not trust the so-called refund, loan capital verification, judicial assistance, commodity refund, point exchange, prize winning tax refund and other information in phone, SMS, QQ and WeChat. If these four points are achieved, personal information disclosure will not become a disease without solutions.

