Today, Red Hat announced that Bash Shell has a security vulnerability, which hackers can use to launch attacks. In short, the problem is serious. Since we must solve the problem after it is discovered, Laozuo did not understand the specific reason for it for a while. In short, it is necessary to fix the vulnerability. Theoretically, since the vulnerability has been discovered, we have to solve it, because users with ulterior motives will display their own technologies in turn.
First, check whether Bash vulnerabilities exist
env -i X='() { (a)=>\' bash -c 'echo date'; cat echo
Execute the above command. If the following feedback message appears, it says that there is a vulnerability and needs to be patched.
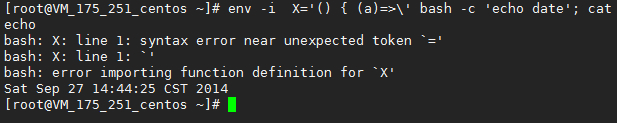
If the above characters appear, it indicates that there is a vulnerability. Then see the following to upgrade the patch according to different system environments.
Second, upgrade the bash patch of different systems
What Laozuo needs to say is that in case we need to do a good backup first, we can also remedy the backup in case of incompatibility problems that lead to system errors. If snapshot backup is available, snapshot backup will be used, and for others, website and database will be backed up. At the time of writing this article, Lao Zuo had successfully tested in Centos and Debian.
A - centos system
yum clean all
yum makecache
yum -y update bash
If it is a centos system, just run the simple script above.
B - Ubuntu system
apt-get update
apt-get -y install --only-upgrade bash
C - debian system
For 7.5 64 bit&&32-bit environment
apt-get update
apt-get -y install --only-upgrade bash
If running in 6.0. x 64 bit environment
wget https://soft.laozuo.org/systems/bash_4.1-3 +deb6u2_amd64.deb&& dpkg -i bash_4.1-3+deb6u2_amd64.deb
If running in 6.0. x 32-bit environment
wget https://soft.laozuo.org/systems/bash_4.1-3 +deb6u2_i386.deb&&dpkg -i bash_4.1-3+deb6u2_i386.deb
Finally, we will run the script detection in the first step to see what the feedback is.
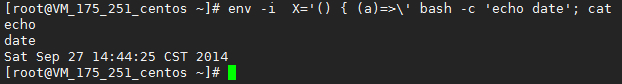
If you can see:
date
Such feedback information indicates that the patch is completed. Support We have completed the repair of Linux Bash security vulnerabilities.

Scan the code to follow the official account
Get more news about webmaster circle!
Entrepreneurship, operation and new knowledge






















