Scheme introduction
Scheme introduction
Function introduction

Scenario introduction
-
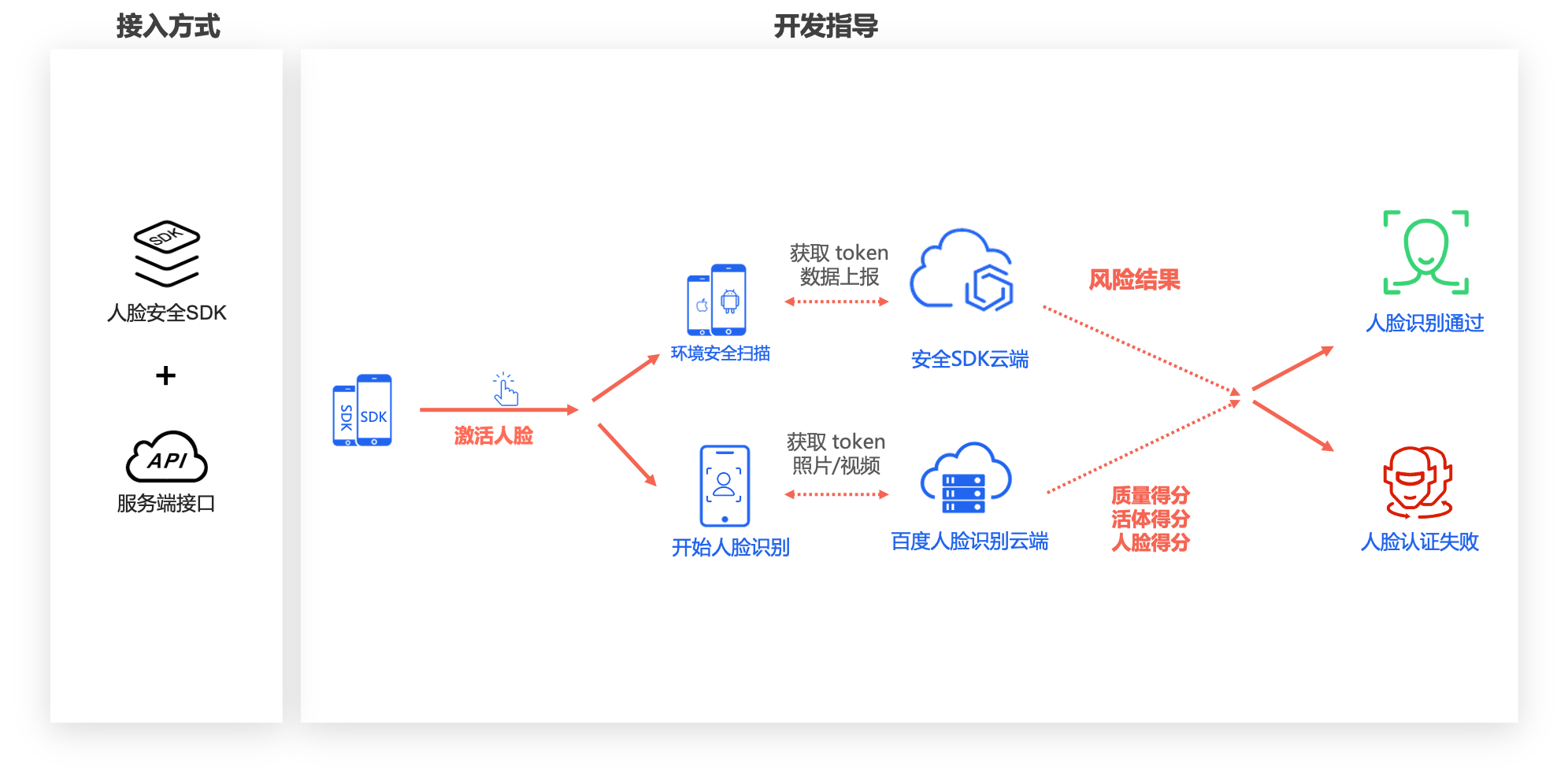
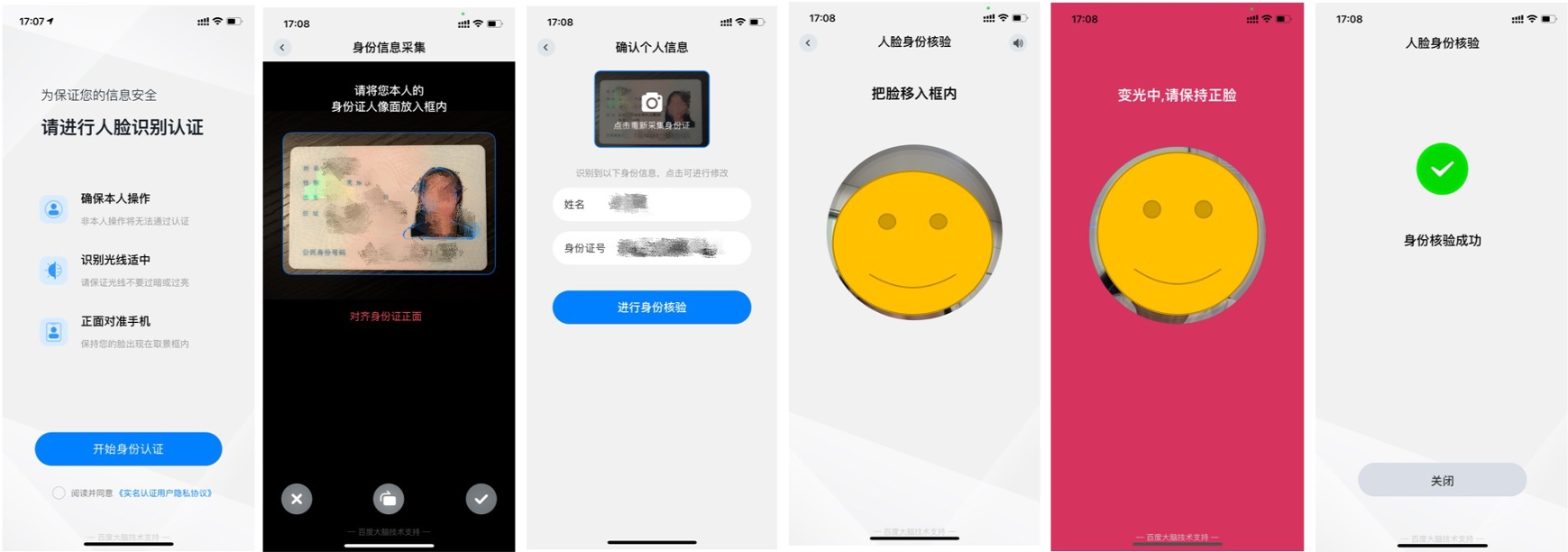
APP real name authentication scheme : It is applicable to the native APP scene. The real-time face collection is carried out by integrating the offline face collection SDK, and it supports multiple live detection methods such as action, pupil dazzle, etc., and calls the cloud based face real name authentication API or face comparison API for user authentication. For APP solution integration, please refer to Integration Document -
H5 Real Name Authentication Scheme : Applicable to H5 scenarios (including browsers, public accounts, and applets), realizing the same experience of faces as APP on H5 pages Real time action, pupil dazzle, silence And other live detection methods, together with calling the cloud based face real name authentication API or face comparison API for user authentication. For H5 scheme integration, please refer to Integration Document -
If you do not use the SDK or H5 page provided by Baidu due to security considerations or business needs, we have opened OCR ID card recognition, face real name authentication V4 and other APIs, you can choose according to your business situation Access through API 。 The scheme also supports Privatization The collection SDK, live detection, face comparison and security risk control functions are deployed locally.
1、 Business demands
1.1 Currently, remote identity verification faces risks
-
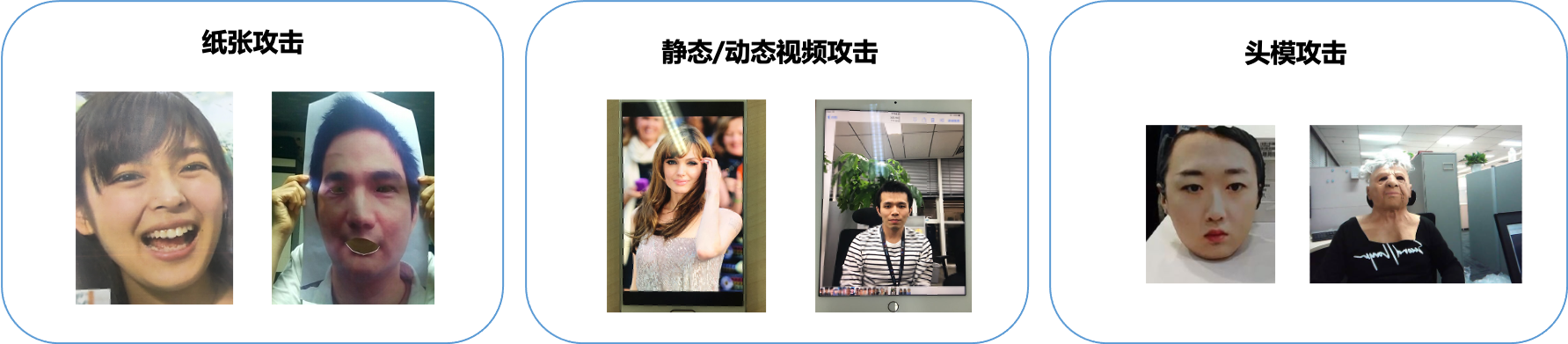
Risk 1: multiple prosthesis attacks 。 include Static electronic image, video image, print photo, photo digging, mask attack, print photo+fill light Etc. In order to falsely use the authority/information of others, the black industry even spends a lot of money to create realistic Mask head mold 。 Human face vivisection risk needs credible vivisection detection capability to block.
-
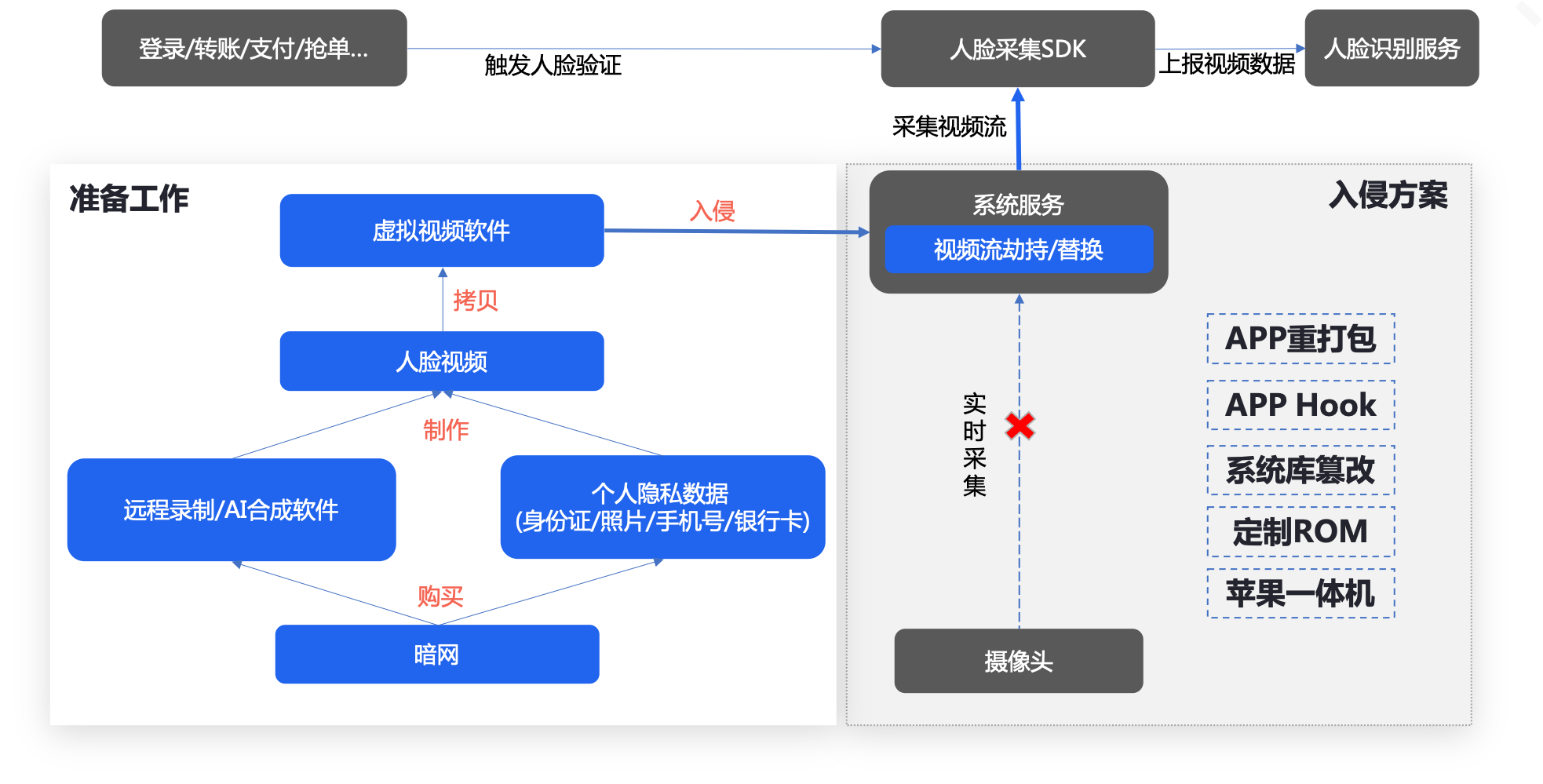
Risk 2: The device bottom layer tampers with the picture 。 In recent years, black industry gangs with a certain level of technology use mobile phones with customized operating systems to change the video stream data that should be obtained from the actual camera to read the specified video file, and initiate Face bypass attack 。 Such loopholes have a huge impact on corporate reputation and personal assets.
1.2 Face real name authentication scheme
-
Be sure to be a real person : Through the end cloud and live detection, the operator can be ensured to be a real person, which can effectively resist attacks such as color print photos, videos, 3D modeling, etc. -
Ensure data security : Discard the traditional way of directly collecting camera data from face SDK, upgrade to the safe data channel collection method, and ensure that face data collection is true and effective from the multi-dimensional aspects of code logic, collection method, and transport layer. -
Make sure you are : Based on the "real person", compare the collected face pictures, names, ID card numbers with the authoritative data source ID database to ensure the authenticity of the operator's identity. Avoid fraud risks such as ID card or face image forgery, and be authoritative and reliable.

2、 Scheme advantages
-
Authoritative data source verification : Compare the real-time collected human face pictures, names, ID numbers with authoritative data sources to ensure the authenticity of the operator's identity. Avoid fraud risks such as ID card or face image forgery, and be authoritative and reliable. -
Strong anti cheating ability : Provide up to 10 offline/online live detection schemes, support picture quality verification, multi frame picture recognition, and effectively resist cheating behaviors such as photos, composite images, video remakes, 3D models, etc; For the first time in the industry, composite image verification is introduced to effectively deal with image/video attacks after PS and face fusion. -
Data encryption and tamper proof : Discard the traditional way of directly collecting camera data from face SDK, upgrade to the safe data channel collection method, and ensure that face data collection is true and effective from the multi-dimensional aspects of code logic, collection method, and transport layer.
-
Various forms of interaction: It supports access methods such as APP, general/WeChat H5, PC, etc. The product forms are comprehensive, flexible and combined to meet the needs of various scenarios -
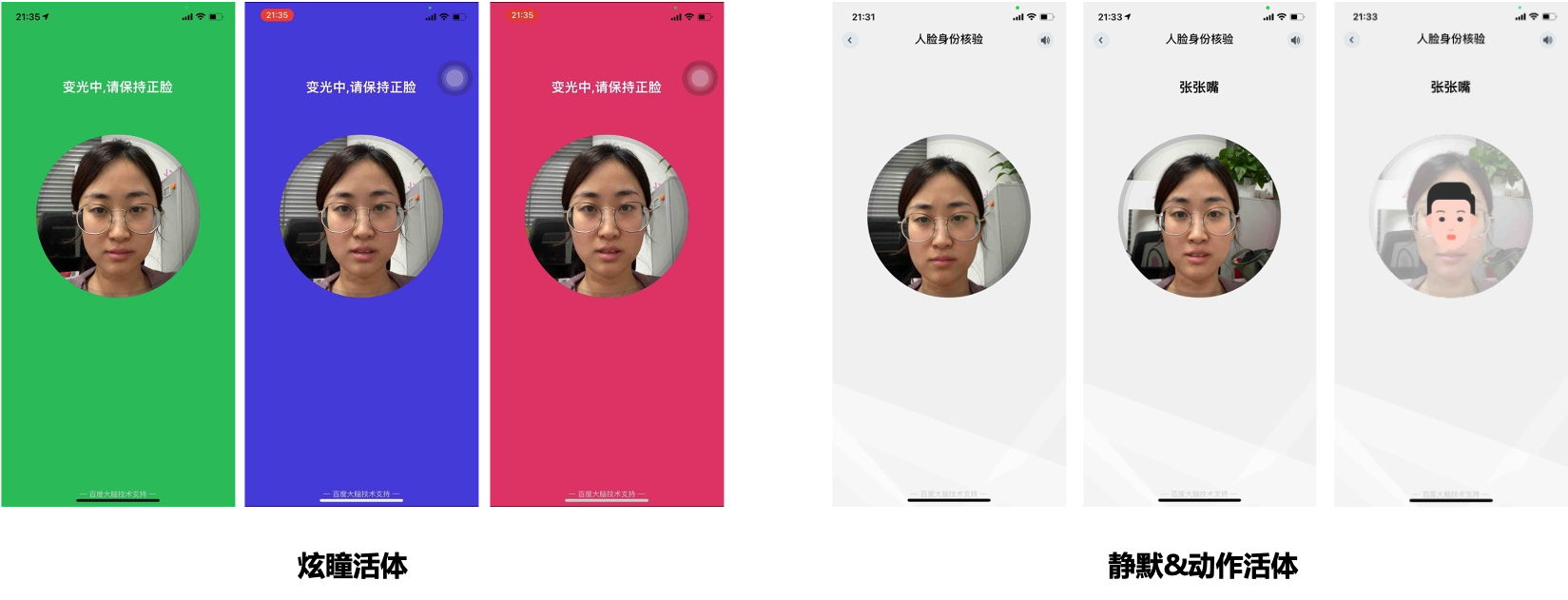
Various methods of live detection : 10 online/offline live detection schemes are provided, which support real-time pupil dazzle, action, voice reading digital (including lip language), silent pictures and other anti cheating means, and can be flexibly selected according to different business needs.
-
Visualization scheme configuration: The scheme supports user-defined setting of face quality parameters and live detection actions, and the interface return parameters and thresholds can be flexibly configured according to business needs. -
Provide UI and demo: A complete set of sample code including UI interaction is provided, which can be used after modifying the parameter configuration, greatly reducing the development integration cost.
3、 Applicable scenarios

-
Financial risk control In financial scenarios with high security requirements, such as investment and wealth management, insurance claims, and securities trading, the face real name authentication scheme is used to convert offline business to online self-service mode to meet business needs such as remote account opening and insurance receipt. At the same time, it can assist in password retrieval and other security measures, reduce the risk of malicious tampering and substitution of user identity information, and improve information security management -
Civil affairs For social security identity verification, government visitor registration, self-service windows in the government affairs hall and other scenarios, the originally cumbersome and time-consuming counter business will be transferred to online self-service, without waiting in line at the window, to improve business processing efficiency -
Hotel check-in The hotel industry has a frequent flow of personnel. In the past, the way of judging whether the ID card is true or not by naked eyes is inefficient, and the accuracy is difficult to guarantee, which cannot meet the regulatory needs of enterprises and the government. Apply face real name authentication technology to verify the identity information of residents with high accuracy and provide more convenient and high-quality services for residents -
Service personnel identity supervision In service industries such as goods transportation and housekeeping, there is a high requirement for the identity authenticity of employees. Using the face real name authentication scheme, practitioners can complete real name authentication by themselves, prevent identity from being replaced or used falsely, improve the efficiency of identity audit, and ensure business security -
Shared business In shared services such as shared shuttle bus, customized bus and time-sharing lease, the ability of live detection, ID card recognition, face quality detection and face comparison is combined to improve the efficiency of the whole process of "registration authentication audit vehicle use", achieve the full process of driving identity verification, ensure information security and effectively avoid the risk of intelligent travel services -
Examinee identity verification At present, the recruitment examination, professional license examination, enterprise internal evaluation and other assessments are gradually transferred to online operation, but there are many risks such as information fraud and substitution examination, and it is difficult to systematically supervise. Introducing the real name authentication scheme of face, providing convenient and efficient identity verification services, ensuring the authenticity and effectiveness of candidates' identities, and helping to strengthen industry supervision
