-
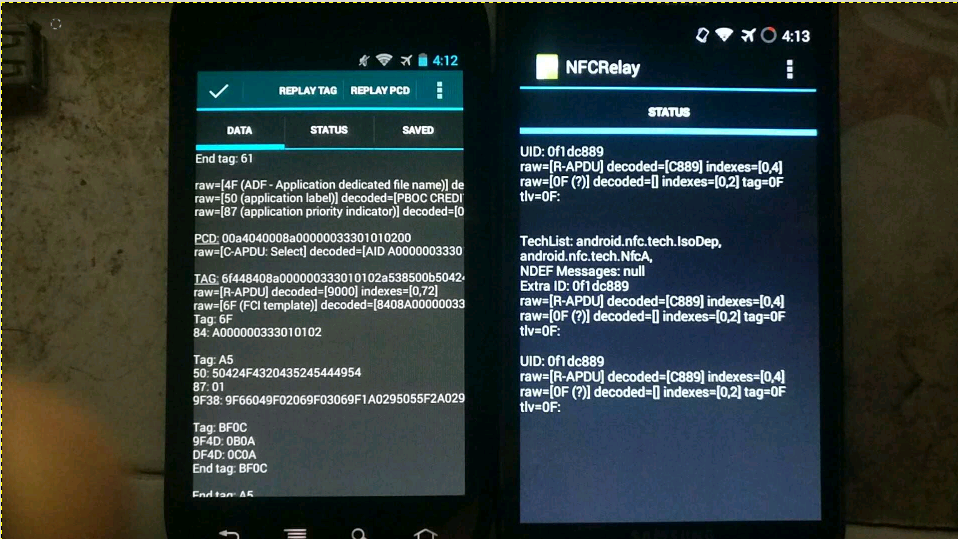
For the theoretical basis, please refer to the PPT of the foreign god: DEFCON-20-Lee-NFC Hacking. I would like to outline the available solutions and functions to be implemented. Test only, do not imitate. Core principles With the help of the CM9 rom version in February 2012, the new nfc read-write tag function can realize software card simulation. (None of the previous versions, The official version of Google has not opened this function. At present, Google has opened other nfc apis for card simulation since Android 5.0. Recently, similar apis have been added to WeChat applet, but I haven't found the actual one yet read the whole passage
-
Internet technology is changing with each passing day, and mobile phone products are constantly updated and iterated. I believe that many small partners are the same as Xiao Bian. Kidney 3, Kidney 4, Kidney 5, Kidney 6, Kidney 7 is coming soon. What about updating old mobile phones? Where have all your old mobile phones gone? When the Internet has completely penetrated into all aspects of our lives, the recycling of second-hand mobile phones will naturally be thought of through the Internet. As a result, online second-hand 3C product trading platforms, such as idle fish, have gradually become popular, and even O2O recycling platforms, such as AiRecycle, are constantly targeting this increasingly read the whole passage
-
It has to be said that people have become more and more inseparable from wifi. Although desktop computers or laptops also contain network cable interfaces, they have basically been abandoned. This is especially true for mobile tablets. They can only use operator networks and wifi to access the Internet. Once smart homes become popular, The application field of wifi will also be greatly expanded. The biggest advantage of wifi is that it is convenient and fast without wiring, but it is inherently weak in stability and security. Hackers break through wifi devices to obtain user information is not uncommon. In short, wi... read the whole passage
-
Cybercrime now targets Apple users, who guide users to click a payment refund link through more sophisticated phishing techniques to obtain users' personal sensitive data. Early stage of phishing - guiding users into "traps" This new phishing attack is disguised as a refund email from the Apple store. Everything starts with a refund email. First of all, the user will receive an email informing the user that the user ID is in the process of payment transaction, asking whether to confirm the purchase of the product in the email. If not, you need to read the whole passage
-
The network black market, as its name implies, is a place on the web where "malicious" services and illegal goods can be bought, sold or leased. Data Value Calculator The black market is experiencing rapid growth, and underground crime is becoming more and more popular. The most profitable product in the black market is user personal information, which is often the purpose of cyber crime. As a global leader in the field of network security software and services, Trendmicro released a network calculator that can calculate the value of data: The author here through read the whole passage
-
This is a new mobile phone ransomware in Canada. When mobile phone users visit adult websites, they will be infected with this malware and blackmailed. Grasp the victim's shame psychology, the hacker will threaten you to pay ransom, or else lock the screen of his mobile phone, and send the message of you browsing the adult website to all the contacts on his mobile phone. Extortion process The attacker used a new variant of the ransomware Koler on the Android platform. When the user visited the adult website XHamster and infected Koler, the variant showed the victim a piece disguised as coming from Canada read the whole passage
-
The hacker Wouter walked into a cafe and ordered a cappuccino gracefully. 20 minutes later. He already knows the birthplace of everyone in the cafe, the school they came from, and the content they have recently browsed on the search engine I met Wouter in a cafe in the center of Amsterdam by accident. Wouter Slotboom, 34, is a hacker. In his backpack, there is always a black device the size of a cigarette box and equipped with an antenna. Wouter Slotboom showed me how hackers can intercept those who use read the whole passage
-
Routing security is a big topic. The background settings of the router are too professional, and the network card is popular. The legendary hacker seems to have disappeared... It seems that the router at home is hopeless. As long as there is a hacker who knows something about it, he will be attacked every minute. Zhaikejun (public account "Letshome") has previously discussed this topic from multiple perspectives, including technical analysis, testing, protocol specification traceability, etc. However, in these things, there is no talk about the security mechanism of routing itself that has been developed for many years. We ignored the heaviest read the whole passage
-
In today's world where user name and password are used as authentication in many places, the importance of password can be imagined. Password is the key to enter your home. When someone has a key to enter your home, think about your security, your property, your privacy... Be afraid. Because weak passwords can be easily guessed or cracked by others, it is very dangerous if you use weak passwords, just like putting the door key under the mat at the door. In the last few days, I submitted weak passwords of multiple telecommunications systems on the vulnerability platform, and read the whole passage
-
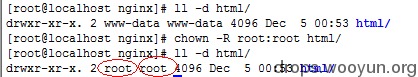
0 × 00 test environment Operating system: CentOS6.5 Web server: Nginx1.4.6 Php version: Php5.4.26 0 × 01 Nginx Introduction Nginx itself cannot process PHP. It is just a web server. After receiving a request, if it is a PHP request, it sends it to the PHP interpreter for processing and returns the result to the client. Nginx generally sends the request to the fastcgi management process for processing, The fastcgi management process selects the cgi sub process processing results and returns them to nginx. Nginx involves two accounts, one is the running account of nginx read the whole passage
-
Breaking network password - violent exhaustion The most basic technology of password cracking is brute force cracking, also known as password exhaustion. If the hacker knows the account number in advance, such as the email account QQ user account, online bank account, etc., and the user's password is set very simply, for example, with a simple combination of numbers, hackers can quickly crack the password using brute force cracking tools. Therefore, users should try to set passwords more complex. Cracking network password - keystroke record If the user password is more complex, it is difficult to use the method of violence exhaustion read the whole passage
-
What is Heartbleed? "Heart Bleeding" loophole, OpenSSL is one of the most catastrophic vulnerabilities in history. It may have been discovered and used for two years. It was announced a few days ago. If you don't introduce too much, just know the severity. This vulnerability will affect all websites and services using the https encryption protocol, including but not limited to Gmail and Facebook - these websites may have been monitored by malicious people to obtain your important information, including but not limited to your account, password, credit card number and password. We don't know whether there is read the whole passage