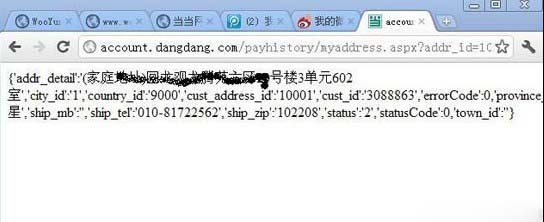
■ Some netizens verified that more detailed customer information can be captured by using vulnerabilities.
■ Lu Kunqian, a trainee reporter of New Express
Tens of thousands of user information are exposed to risks, and Dangdang reported that the loopholes have been repaired
A few days ago, the third-party security issue feedback platform "Black Cloud Vulnerability" released information through microblog, saying that Dangdang could lead to user data disclosure due to design defects. In just two days, hundreds of netizens have forwarded and commented. Although Dangdang immediately dealt with the vulnerability on the day when the news was announced, and said that "technicians immediately repaired it within 10 minutes", why did a thing that could be completed within 10 minutes make a storm? Mr. Fang, the person in charge of "Black Cloud Vulnerability", told the reporter of New Express that the main reason for the release of Dangdang's vulnerability information was that Dangdang had not paid attention to the vulnerability before, so the platform chose to disclose information to attract Dangdang's attention to security issues.
Vulnerability can reveal tens of thousands of user information
According to the report description released by the Black Cloud vulnerability, users can get the addresses, names and contact information of all Dangdang recipients as long as they modify the specific website step by step after logging in. In the detailed description, the reporter said that the vulnerability was due to "improper design at some place, which cannot be too detailed, and is too easy to find".
After the vulnerability was announced, some netizens also personally verified the authenticity of the information and confirmed that Dangdang's vulnerability could capture more than 40 million address information. Many insiders also participated in the discussion. Shi Shuwei, the general manager of the Product Business Department of Beijing Vitality Tianhui Technology Co., Ltd., said on his microblog that "this black dragon is too big, isn't it? There's no problem with value transfer, but he doesn't even judge whether the ownership of addressid belongs to the current user!" Li Tiejun, the anti virus engineer of Jinshan Network, forwarded the microblog and said, "If there are loopholes, they should be dealt with in time. The sky will not fall. It is fatal not to pay attention to security loopholes and not to repair them in time."
Mr. Wang, who has been engaged in programming for a long time, told the New Express that the vulnerability of Dangdang was a low-level error. "Even an amateur can find problems by copying the address." He said that generally such user information should not appear on the address, but should be encrypted. But encryption may cost a lot of time, Therefore, most websites seldom do this, "but I didn't expect that e-commerce companies as big as Dangdang would not encrypt data."
On the day of receiving the report, Dangdang said that it had repaired the vulnerability in the morning of the same day, and said that after the system log inspection, there was no leakage of a large number of user information.
Defying vulnerability reports several times
In fact, it is not the first time that Dangdang has been found to have loopholes. According to Mr. Fang, the person in charge of the black cloud vulnerability, at least two times before, it was found that there was a vulnerability in the system of Dangdang, but after contact, Dangdang did not give any response. Mr. Fang said that on the black cloud vulnerability, the general report is provided by netizens, and the platform will put the report in the background first, and will release the report after confirming the vulnerability and notifying the e-commerce to deal with it. "The general vulnerability report should be released after being repaired", which Mr. Fang thought could avoid the vulnerability causing system crash or information disclosure. However, in fact, not every e-commerce company attaches importance to vulnerabilities. He said that it was precisely because Dangdang had not responded to previous vulnerability reports that it chose to make public reports before vulnerability repair, and wanted to draw Dangdang's attention to security issues.
The reporter saw on the platform that every vulnerability information published on the website has a list clearly indicating the vulnerability type, hazard level, vulnerability status and other information, while the column of vulnerability status on Dangdang shows that "the manufacturer has not been contacted or actively ignored".
The reporter found through the platform that in addition to the vulnerabilities announced this time, Dangdang had also been found "Dangdang Collection Management XSS Vulnerability", "Dangdang Multiple Storage XSS Vulnerability", "Dangdang User Privacy Disclosure Vulnerability", etc. Mr. Wang told the reporter that the first vulnerability is also to allow "people with a mind" to steal user information by inserting applications in the address bar, "This vulnerability can even reveal more confidential information such as user passwords." And the response column of the report also shows that "the manufacturer could not be contacted or the manufacturer actively refused." This reporter called Ye Xiaozhou, the manager of the public relations department of Dangdang, to ask whether the above vulnerability has also been resolved, but as of the submission, no response has been received.
Linking to Jingdong Mall and Vancl have found system vulnerabilities
According to Mr. Fang, the black cloud vulnerability was established by a group of IT people who are interested in network security in July 2010, but the site has only been established for more than a year, and more than 3000 vulnerabilities have been found. Through the public information provided by the platform, it can be found that JD Mall, 163 Mailbox, Sohu Weibo, etc. have all had different levels of system vulnerabilities, and Vancl has also had such user information disclosure program vulnerabilities as Dangdang.
Mr. Fang believes that loopholes in programming are inevitable, but now the problem is that some e-commerce companies are not concerned about loopholes, "such as Dangdang, a large listed e-commerce company, has not done enough to fulfill its responsibilities in this regard." In fact, according to the information queried by reporters, China still has not established a third-party platform for monitoring program loopholes, There is still a large gap in supervision.
However, some netizens believe that the way of reflecting the problem of the black cloud vulnerability is the same as that of "forcing the palace"
Zhao Zhan, a researcher at the Intellectual Property Center of China University of Political Science and Law, said that at present, the Tort Liability Law of the People's Republic of China clearly protects citizens' right to privacy, and the Criminal Law also stipulates that the disclosure of personal information may be subject to criminal liability. Consumers can protect their rights through civil and criminal channels when encountering the above situations, but the key is that it is difficult to collect evidence, Especially in the case of Dangdang, before consumers can retain evidence and notarize, Dangdang has taken technical countermeasures. From this point of view, the monitoring and management of network vulnerabilities still depends on the consciousness of e-commerce. However, Zhao Zhan also revealed that the Ministry of Industry and Information Technology is currently taking the lead in formulating the first national standard on personal information protection, which has not yet been promulgated.
Original article reprint please specify: reprint from Seven Travelers Blog
Fixed link of this article: https://www.qxzxp.com/2981.html

