-
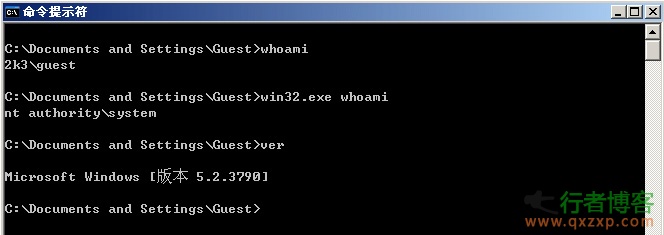
CrowStrike found that the tool MS14-058 (CVE-2014-4113), a Windows local authorization vulnerability that has been used for more than half a year, has been disclosed. Its right raising success rate reaches 100%: Usage: C: >Win32.exe "net user qxzxp qxzxp/add" (The current path of win32.exe is followed by a command line after a space) Win64.exe is an authorization tool for 64 bit operating systems. As above, in general, it is a 32-bit operating system. The vulnerability occurred in Win32k.sys, which led to the hacker's success rate of power raising read the whole passage
-
1. The definition of social engineering is not that you simply search the victim's information on the Internet, which is not even a narrow sense of social engineering. The activities you want to carry out are not limited to narrow social engineering. You need to carry out some in-depth interactive behaviors with victims or information owners. ① In this process, we should make full use of the known information, especially the information extended in search engines, to increase trust. For example, Google Maps can be used to explore the surrounding environment, or to understand the victim's interpersonal relationship and online activity. ... read the whole passage
-
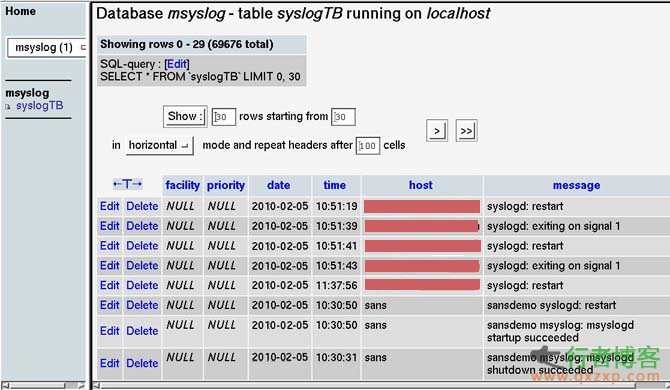
This article will provide a brief overview of log collection and analysis. Specifically, we will focus on three basic issues: log transmission, log collection, and log analysis. It also involves simple log storage and archiving. The purpose of writing this article is to further discuss the log processing of the Linux system retained by the court scene analysis. Log transmission ~~~~~~~~~ First, let's look at log transmission. The traditional UNIX log transmission mechanism is UDP, port 514. Log messages are sent and received by the system log daemon read the whole passage
-
Router Scan v2.44 is a router security testing tool that can specify IP segments to perform security tests such as brute force cracking on routers. It supports a variety of routers of TP-LINK, Huawei, Belkin, D-Link and other major brands. Seeing this picture, I was shocked. So it seemed that this software router's multi line blasting was similar to that of 3389 blasting. It took me a little time to perfect the Chinese version. It feels good. Don't do bad things. It's only for security testing and research~ Official download address: http://stascorp.com/load/1-1-0... read the whole passage
-
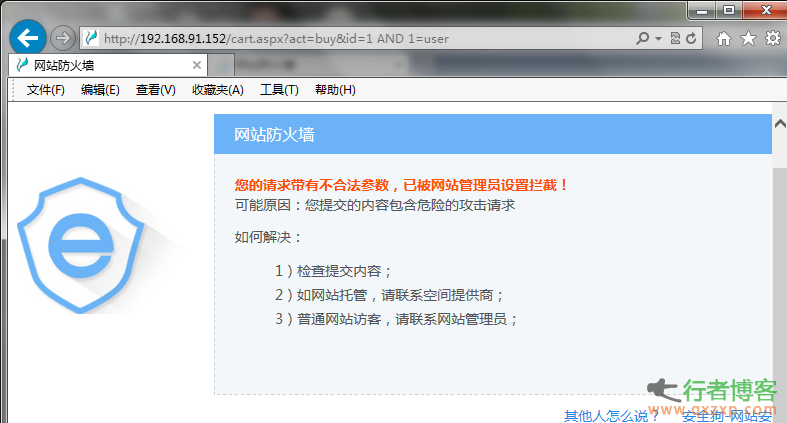
Test time: October 21, 2014 Test version: IIS version V3.3.09476 (2014-09-24), Apache version 3.1.3.08512 (2014-05-29), which are the latest versions available today. The core character used to bypass:% 0A, which needs to be used together with the comment character in some special occasions. Detailed test steps: 1. The machine has installed V5shop with injection (IIS6+ASPX+MSSQL2005 architecture to test the IIS version of the security dog). Routine injection tests: http://192.168.91.152/cart.aspx?act=buy&id=1 AND 1... read the whole passage
-
Part I: Social Engineering - Information Spying 1、 Use the information around you Try to make use of the existing information, which will be able to deal with emergencies. Such information refers to rules, regulations, methods and agreements. Rules refer to the rules of an industry. We can think of them as trade rules or internal agreements. For example, stall A, in order to rob stall B of its business, is wrong to deliberately lower the price of stall B and break the unfair business law. So we should try to understand such information from all walks of life, such as read the whole passage
-
Routing security is a big topic. The background settings of the router are too professional, and the network card is popular. The legendary hacker seems to have disappeared... It seems that the router at home is hopeless. As long as there is a hacker who knows something about it, he will be attacked every minute. Zhaikejun (public account "Letshome") has previously discussed this topic from multiple perspectives, including technical analysis, testing, protocol specification traceability, etc. However, in these things, there is no talk about the security mechanism of routing itself that has been developed for many years. We ignored the heaviest read the whole passage
-
Perfect solution to the problem of wordpress 4.0 Chinese label 404 After the WordPress site has made pseudo static and defined the format of fixed connection, the problem of 404 Chinese tags will appear. Everything else is normal, that is, opening the WordPress Chinese tag tag is a 404 page error. Since wp is a foreign product, it does not consider the compatibility of chinese labels. many friends will encounter the problem of chinese labels 404. let me share some solutions to this problem. Resolve the problem that WordPress cannot open the Chinese tag link read the whole passage
-
The bus LED screen displays the words "Come here" Recently, many citizens in Dalian found that the words "passer-by A came here for a visit" scrolled on the LED advertising screens of some buses in our city... Reporters learned from relevant units yesterday that since the 5th of this month, they found that the bus LED system had been hacked, and the words "wuyun passer-by A came here for a visit" appeared on the LED screens of more than 300 public buses. After emergency treatment, the virus was basically eliminated. The bus LED screen shows "Come here" Mr. Wang, a citizen, told reporters that on the 11th read the whole passage
-
I think we will not be too familiar with the SSL "painstaking" vulnerability a while ago. After the vulnerability came out, everyone organized people to do something. The analysis of this analysis and the patching of this patch. Sadly, even if it is repaired, it can still be bypassed and make everyone exhausted. The storm is rising again: SSL3.0 Heartbleed is coming again The storm has just passed, and our manufacturers haven't had time to relax. Today, we received another terrible news: "Heartbleed" is coming again! But this time, it is SSL 3.0. According to roadside social consumption read the whole passage
-
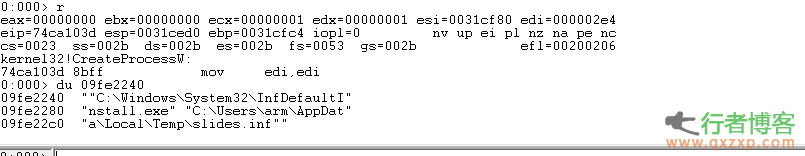
OLE package management INF arbitrary code execution vulnerability, CVE-2014-4114, can be triggered on all Windows platforms that will release a patch tomorrow. This vulnerability affects Windows Vista, Windows 7 and other operating systems, and can be triggered by Microsoft documents. Moreover, this vulnerability is a logical vulnerability, which can be easily exploited successfully. At present, the samples have spread and are easy to be modified and reused by hackers. It is expected that the Microsoft patch will come out early this morning. Han Haiyuan reminds users not to open office documents sent by strangers during this period. The vulnerability was first exploited from iSIGHT read the whole passage
-
ISIGHT found the latest 0day vulnerability that affects the full version of Windows system during Russian cyber espionage activities. The vulnerability number is CVE-2014-4114. At present, Microsoft is urgently making a patch for this vulnerability. Yesterday, Microsoft's partner iSIGHT Partners announced that a new Windows 0day vulnerability was found during the cyber espionage war against NATO, EU telecommunications and energy sectors. The vulnerability affects the current full version of Microsoft's systems, including Windows Server2008 and Windows Server2012, which are currently the most widely used server systems read the whole passage