For the theoretical basis, please refer to the PPT of foreign gods: DEFCON-20-Lee-NFC-Hacking , I would like to talk about the available solutions and functions. Test only, do not imitate.
Core principles
With the help of the CM9 rom version in February 2012, the new nfc read-write tag function can realize software card simulation. (None of the previous versions, the official version of Google has not opened this function. At present, Google has opened other nfc apis for card simulation operations since Android 5.0. Recently, similar apis have been added to the WeChat applet, but I haven't found a solution that has been implemented. If you find any trouble, please let me know.).
Implementation function
All label data of 13.56hz nfc wireless communication protocol supported by Android phones can be intercepted. There has been no good solution for contactless black box testing of nfc, or it is too high-end (professional equipment is required), Either it is not easy to use (proxmark3 is not cheap, the wireless monitoring method leads to unstable intercepted data, and there is no ready-made solution, and the operation convenience and interactivity are also poor) nfcproxy provides a low-cost and efficient solution for our occasional test dogs, which supports various nfc tags, iso 14443 standards, and apdu data is complete and stable, The secondary development based on the source code of Android app is also very simple, and it is not a problem to change Java casually. Based on this app, multiple test methods can be derived in software mode
1. Data sniffing between card and terminal
2. Data modification during interaction
3. Analog card
The most important thing is simple. Just buy a second-hand mobile phone for two hundred yuan each.
Hardware requirements:
Two android phones with nfc function (salted fish can be handled at a minimum price of 300 yuan), one POS or card reader with contactless function (one POS is the most convenient, and I have a POS that supports UnionPay flash payment), their own bank cards, those that support contactless payment, and those with UnionPay quick pass logo can
1. Based on an Android phone supporting CM9 rom
I use the nexus s of Google's own son generation. The ROM is slim 4.3 build 2-OFFICIAL-1332, a cm based customized version of Android version 4.3.1. I bought it early and it's a little expensive. Now I don't need to buy it if I want to buy second-hand fish. It's cheaper in later generations. The second son, the third son and the fourth son can all be considered. One plus one can also be considered. It's a little expensive. Theoretically, it is OK to support CM9. However, because the CM official website has been yellowed, it is hard to find the old version of the rom, so try to find the old version of the rom corresponding to the mobile phone before deciding what to buy.
2. One Android phone with nfc function (preferably supporting cm9)
I use Samsung GALAXY S2 T version SGH-T989 Hercules, CM version 11-20160815-NIGHTLY-hercules, Android version 4.4.4. It seems that the function of software card simulation has been removed from the cm11, and I have not upgraded the rom version. One can work. As long as the customized rom is not too exotic, it can be done in theory. It is recommended to choose the one that supports cm, which is more safe. Hardware selection is the same as above
Software Requirements
https://github.com/nfcproxy/NFCProxy It has a complete function implementation. You can directly package and use it. I integrate the emv bertlv library based on your own convenience, and can directly unpack interactive data in the app. You can try my github address: https://github.com/alcarl/nfcproxy Download local app package: nfcproxy-app-debug.apk
usage method
Both phones are equipped with nfcproxy. Both phones can open the NFC function and connect to the same wifi. Two phones can access each other
1. Proxy side settings
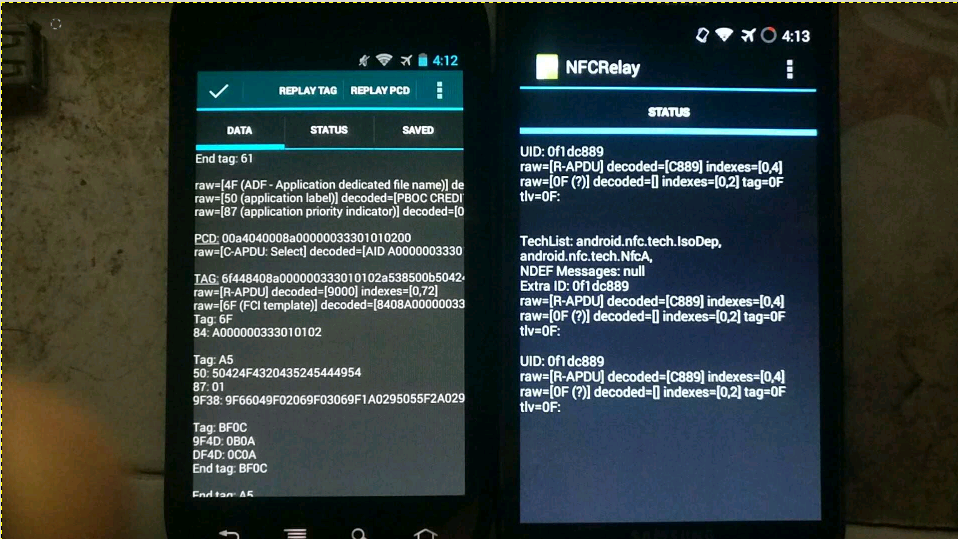
On a mobile phone that supports cm9 card simulation (I have to be nexus s), open the nfcproxy software, click Set, cancel the relay mode radio box, fill in the IP address of another mobile phone, fill in the wifi IP port of another mobile phone, fill in the nfcproxy listening port of another mobile phone, by default, 9999encrypt communications does not need to be selected, and if you play without encryption, always keep screen on casually debug logging, the card number can be displayed. Then exit setup.
2. Setting of relay terminal
On the other mobile phone (I have to be t989), open the nfcproxy software, click Set, check the relay mode radio box IP address, do not fill in the port, fill in the nfcproxy listening port just set on the other mobile phone, default 9999, just like on both sides, encrypt communications do not need to be selected, play without encryption always keep screen on random debug logging check, The card number can be displayed. Then exit setup.
3. Test
1. Open and paste the nfcproxy software of the mobile phone used for relay to the bank card. At this time, the status window should prompt TechList: android.nfc.tech.IsoDepandroid.nfc.tech.NfcA. If there is no response, please check whether nfc is turned on and whether the NFC function of the mobile phone is normal
2. Get the POS machine to the interface where you can select consumption, enter the amount and prompt you to swipe the card
3. Open the nfcproxy software of the mobile phone used for the proxy end and paste it to the POS machine to perform the non receiving card swiping action.
Under normal circumstances, the data window of nfcproxy will prompt: Reader TAG: Tech [android. nfc. tech. Iso. PcdA] Connecting to NFCRelayConnected to NFCRelayTransaction Complete! This means that the mobile phone with the card has been connected, the request from the POS has been forwarded to the card, and the response from the card has been forwarded back, and the transaction has been completed. At this time, the POS should show that you have entered the password, and the transaction is successful. Then look at the data window of nfcproxy on the replay side, you can see the interactive data. Long press on the data to select the three vertical points on the right, and export to file saves the intercepted data to the internal storage directory/NfcProxy
Note 1: If the phone posted to POS does not respond, you need to check whether the nfc function is normal
Note 2: The status prompts that two mobile phones need to be checked for connection to NFCRelay failed wifi Whether it is connected, and whether the configured IP and port are normal
Good luck.
btw: I have been using this scheme for 15 years. It is only necessary for work testing pos. It is convenient to use it occasionally. I used it again recently and decided to sort it out. I have read the article of God before, and I also contributed to the community once. The software itself has great potential, such as dynamic modification of interactive data...... You know, don't mess around. You can check the water meter. In addition, it is also found that some terminals will use some strange modes to read cards, leading to software errors. At this time, they can only use proxmark3 to monitor violently. However, this method of mitm is much more convenient and cheaper than proxmark. At the end, I attached a picture in the PPT. I drew it briefly for everyone to understand

*Author: xinmeow, from FreeBuf COM
Original article reprint please specify: reprint from Seven Travelers Blog
Fixed link of this article: https://www.qxzxp.com/6474.html

