-
Hacking Team is an Italian company "famous" for helping the government monitor citizens. They sell intrusion and surveillance tools to governments and law enforcement agencies including Morocco, Ethiopia and the US Drug Control Agency. And these two days they were hacked! "Hacking Team" is reversed by "Hacked" As a hacker team and company specializing in monitoring technology, Hacking Team (hereinafter referred to as HT) has experienced the experience of internal data being made public today. Because of HT's business behavior and their development for the government read the whole passage
-
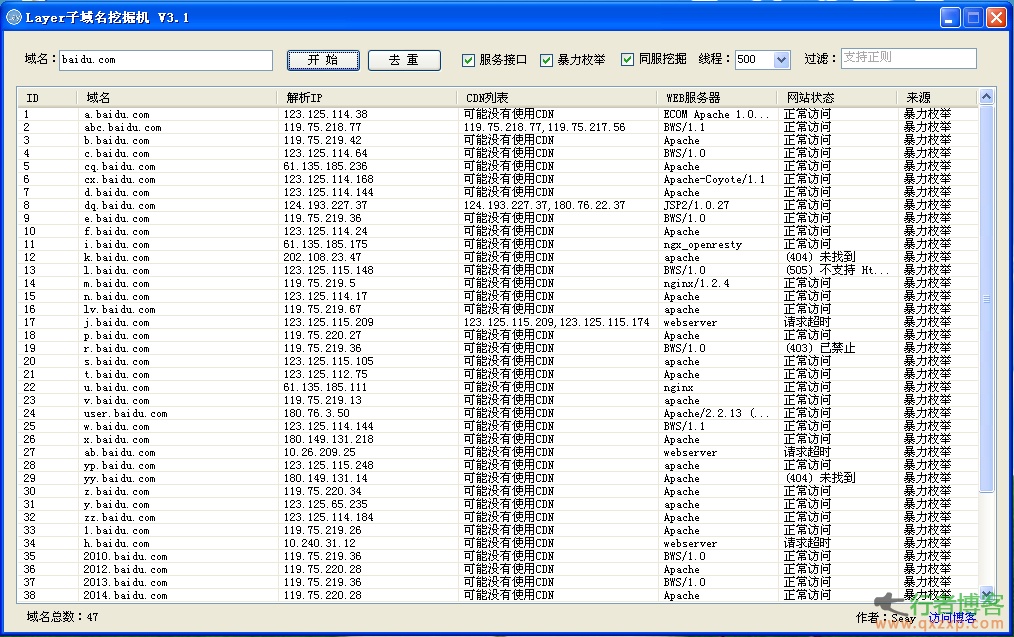
instructions: 1. If you want to use a custom dictionary, please name the dictionary file dic and place it in the same directory as the program. The program will automatically load the dictionary. 2. If there is no custom dictionary, the program will automatically use the built-in dictionary. The built-in dictionary has a total of more than 20000 pieces of data, including common sub domain names, as well as 3000+common words and 1-3 letters. 3. If the domain name below level 2 is to be blasted, you can directly fill in the sub domain name to be blasted, and the program will automatically splice the next sub domain. For example, if you fill in hi.baidu.com, the program will explode .hi.ba... read the whole passage
-
A "hacker" in Nanjing stole 80000 yuan from a game recharge card company in Wuhan by using the hacker software he bought. After the incident, Zhou Wei and Ji Hai, who produced and sold hacker software, were exposed as hackers were caught. But no one expected that Ji Hai, the expert who wrote this hacker software, had a rich family and was not short of money. However, when Ji Hai hired him to write hacker software at a monthly salary of 20000 yuan, he agreed. He said: "This money is too easy to earn. I can do it in an hour in bed." Selling hackers in QQ groups read the whole passage
-
Netsparker is a comprehensive web application security vulnerability scanning tool, which is divided into professional version and free version. The free version is also powerful. Compared with other comprehensive web application security scanning tools, Netsparker can better detect SQL Injection and Cross site Scripting type security vulnerabilities. This version is a professional version. Please do not use it for illegal purposes. Please delete it as soon as possible after testing. Download address: http://pan.baidu.com/s/1bnGLQ7H read the whole passage
-
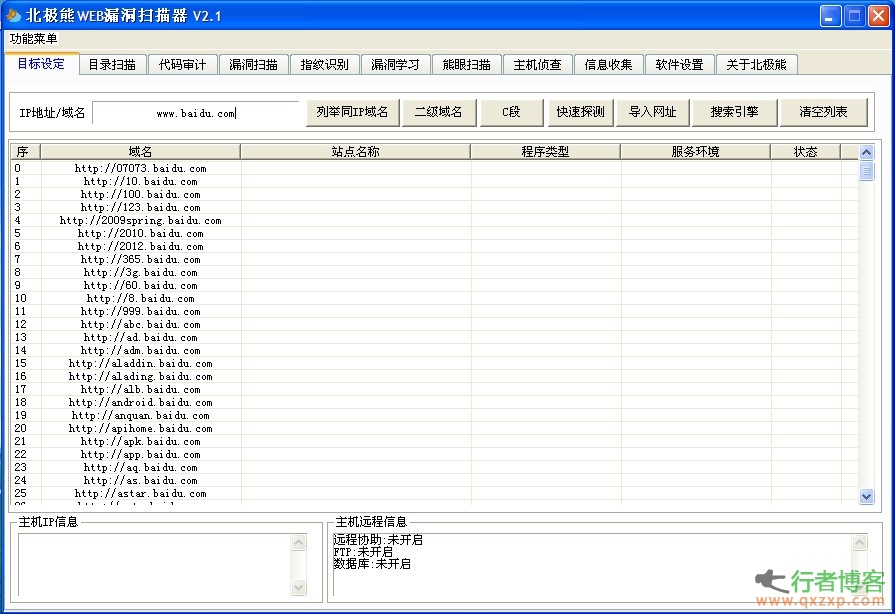
Polar bear scanner is a simple WEB scanner, but it has very rich functions. In addition to the basic secondary domain name detection and C segment, it also provides search engine crawling sites. Unfortunately, directory scanning cannot skip the fake 404 for the time being, but it supports multi task execution, delays (reducing the speed to avoid being intercepted by security software), and also rarely has the code audit function, which allows administrators to quickly conduct white box testing, hidden trojans in website code, and other detection, which is fast... The vulnerability scanning software only comes with 12 scripts, but it is read the whole passage
-
On December 25, it was reported by foreign media that senior executives in the payment industry disclosed that hackers who attacked Target recently, bringing security risks to up to 40 million credit and debit cards, had successfully stolen the personal identification numbers (PINs) of these bank cards. A major American bank is worried that hackers have the ability to crack the encrypted code and withdraw money from the account by pretending to be customers. The source asked the media to remain anonymous because the whole incident is still under investigation. Tajit spokesman said, "There is no encrypted PIN code message read the whole passage
-
Burp Suite is a web application integration attack platform, which contains a series of burp tools. There are a lot of interfaces between these tools that can communicate with each other. The purpose of this design is to promote and improve the efficiency of the entire attack. All tools in the platform share the same robust framework, so as to uniformly handle HTTP requests, persistence, authentication, upstream agents, logging, alarms and scalability. BurpSuite allows attackers to enumerate, analyze, and attack Web applications by combining manual and automated techniques. These different burp workers read the whole passage