-
This version thanks to God [YYY] for modification and sharing. The specific features are as follows: ◎ Based on the latest domestic version (theoretical support for Android P) ◎ Replace the package name, do not update, do not roll over, stable and easy to use ◎ The new password will be displayed in color below the hotspot ◎ Intelligent password display, blank password and copy button will not be displayed when no password is obtained ◎ Remove nearly 98% of redundant code&layout&advertising&permission ◎ Brand new interface, retaining the top bar, switch and portable Wifi button ◎ The built-in browser is removed, and the connection is successful without jumping ◎ Removing obstacles read the whole passage
-
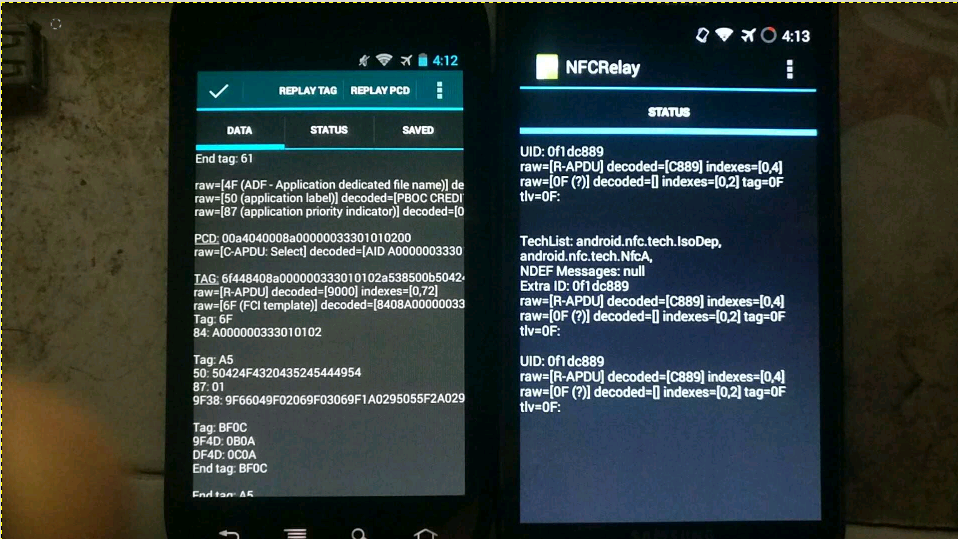
For the theoretical basis, please refer to the PPT of the foreign god: DEFCON-20-Lee-NFC Hacking. I would like to outline the available solutions and functions to be implemented. Test only, do not imitate. Core principles With the help of the CM9 rom version in February 2012, the new nfc read-write tag function can realize software card simulation. (None of the previous versions, The official version of Google has not opened this function. At present, Google has opened other nfc apis for card simulation since Android 5.0. Recently, similar apis have been added to WeChat applet, but I haven't found the actual one yet read the whole passage
-
The used WIFI password saved in the file wpa_supplicant.conf of Samsung 4.3+system has been encrypted into garbled code, and it was broken by many methods. The following method is borrowed from the Great God, and can be used for personal testing. Use RE Manager to open build.prop in the system directory with a text editor, Found: ro. securestorage. support=true Modify to: ro. securestorage. support=false Then restart After the change, the connected password will not be encrypted. Open the date/misc/wifi folder with the RE Manager, where read the whole passage
-
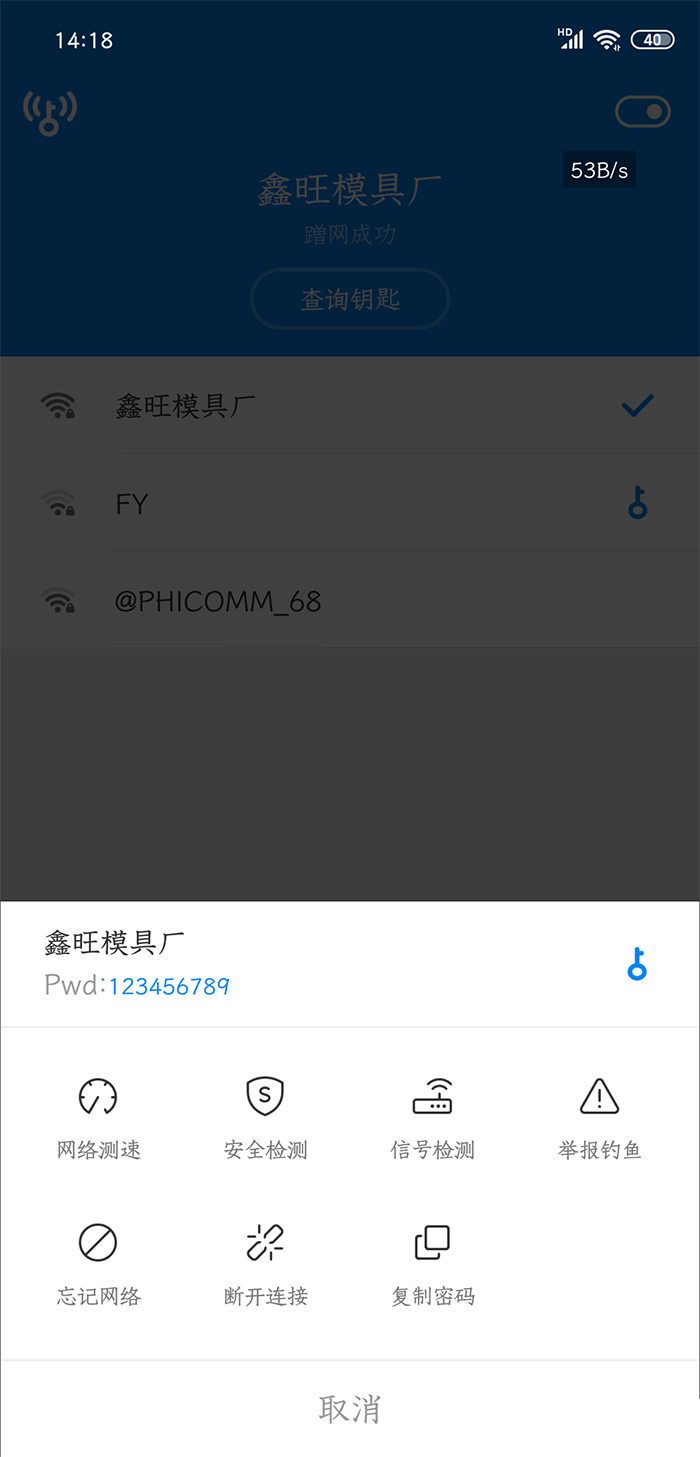
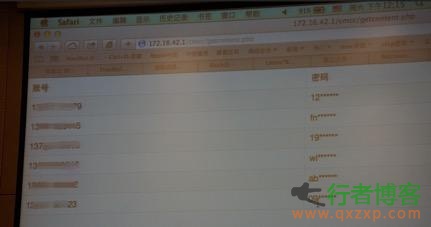
Note: The master key is not a password cracking software, but a software for sharing wifi passwords. Through this software, you can get the wifi shared by others to connect to the wireless network. However, this software has many advertisements and does not display the wifi password. So there is this modified version. This modified version removes program advertisements and can display the wifi password. This software is modified according to the advertised version of Triumph God. Thanks again. It is also a deep change. In fact, this is nonsense. The reference must be completely consistent read the whole passage
-
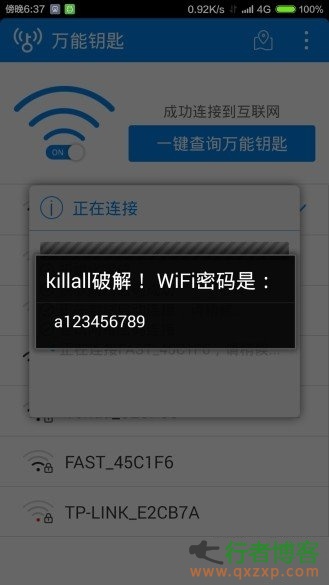
The best neighbor is a good person who does not have a Wi Fi password. However, the neighborhood relationship is so indifferent now that the password always blocks the door when you want to rub a Wi Fi. Without a good neighbor in China to provide a Wi Fi password, we will take the initiative to rub! Today, Hard Chuangbang will dedicate a method to capture Wi Fi passwords. At present, the common Wi Fi encryption methods are WEP WPA2 and WPS (links are their own cracking methods). However, some netizens reported that the previous methods to crack WPA2 took too long and were not applicable to all WPS enabled access points. And today we introduce read the whole passage
-
When three well-known British politicians used unencrypted open WiFi networks, security experts immediately hacked them. Public WiFi risk Through a live demonstration of a real cyber attack, the three famous British politicians, David Davis Mary Honeyball and Lord Strasburger experienced the security risks of open WiFi. Every day we can find a surprising number of WiFi networks around us. But how many people really realize that these WiFIs may not be safe? The security experts of F-Secure deployed a fake and malicious W read the whole passage
-
At the RSA security conference in San Francisco on Tuesday, researchers presented their latest research results - the 0day vulnerability in iOS 8 "no iOS zone". As the name implies, it can enable Apple iPhone The iPad and iPods are constantly restarted, and the only thing the victim can do after being attacked is to run away. Overwhelming: "iOS free zone" Adi Sharabani and Yair Amit, researchers of Skycure, a mobile security company, presented their latest research at the RSA security conference in San Francisco on Tuesday. The name of their research is also very aggressive, and it is called "iOS free zone". This read the whole passage
-
Common sense tells us that users are the weakest link in IT risk management, especially for some "naive and brave" users... But how did hackers use this naivety (lack of protection awareness) to enter user terminals and company accounts? Many of the methods they used involved some psychological tricks, so most of the attacks involved phishing and social engineering. Here are seven reasons why users should be hacked: 1、 Automatic hook up Because of its effectiveness, great influence and simplicity, phishing has always been read the whole passage
-
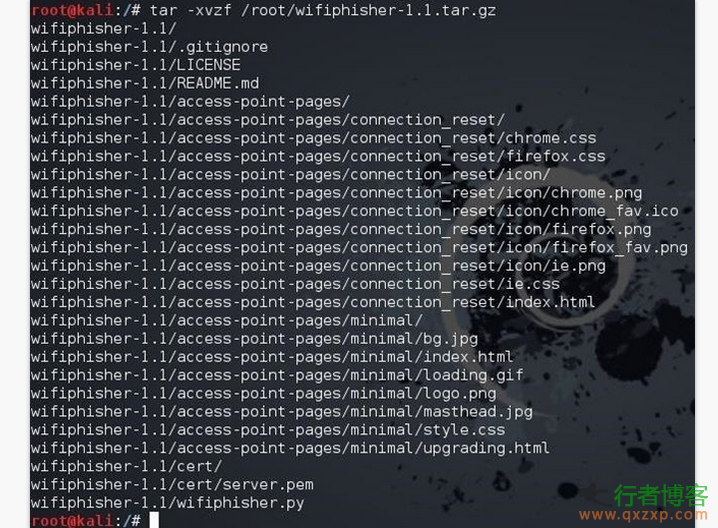
Disclaimer: The security tools and procedures (methods) provided by this website may be offensive, and they are only used for security research and teaching at your own risk! 3vilTwinAttacker can help penetration testers build a fake phishing WiFi. On the surface, this is a normal AP (network access point) that provides online services, but in fact it is imperceptibly sniffing for network traffic. Software dependencies Kali linux is recommended Ettercap Sslstrip Airbase ng (included in airfrack ng) DHCP Nmap DHCP Installation (Debian) read the whole passage
-
On March 15, CCTV once again focused on the security of mobile phone applications, exposed the security of free WiFi at the party, and demonstrated to everyone on the spot that it used fake phishing WiFi technology to steal the online content of audience. Frankly, many mobile phone users are also used to "surfing the Internet". They like to log in to WiFi in public places such as cafes, teahouses, hotels and so on for various operations, which is quite unsafe! ”West Lake Debate "-- Sheep Wall of China SIS Conference In the "West Lake Debate read the whole passage
-
Nowadays, more and more shopping malls, coffee shops, restaurants and other public places provide open WiFi networks. But sometimes even if our device is connected to WiFi, when we open a webpage, an authentication page will pop up immediately... Is it very depressing? This Spring Festival, I will share with you several ways to bypass common WiFi authentication. I wish you a happy New Year. For entertainment only, please obey the rules and regulations, and don't be beaten by the boss^_^ WiFi requiring identity authentication This is an open WiFi network. Before actually using the network read the whole passage
-
Disclaimer: The security tools and procedures (methods) provided by this website may be offensive, and they are only used for security research and teaching at your own risk! Greek security researcher George Chatzisofroniou has developed a WiFi security testing tool called WiFiPhisher. Although there are many tools on the Internet that can crack the wireless network, WiFiPhisher is different from it. It does not need to use brute force attack to obtain the user's wireless WiFi password. If you are interested, you can download it on GitHub for free. WiFiPhisher principle 1.... read the whole passage