-
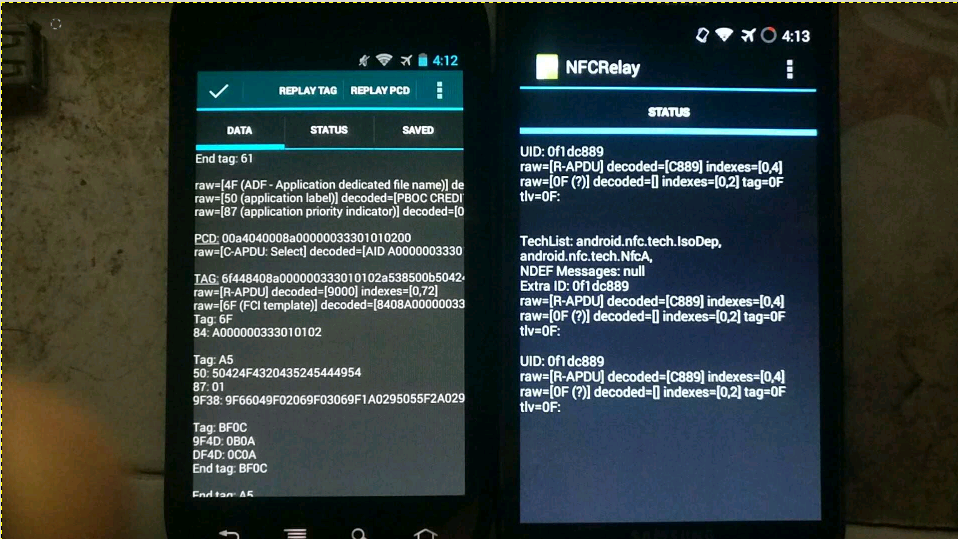
For the theoretical basis, please refer to the PPT of the foreign god: DEFCON-20-Lee-NFC Hacking. I would like to outline the available solutions and functions to be implemented. Test only, do not imitate. Core principles With the help of the CM9 rom version in February 2012, the new nfc read-write tag function can realize software card simulation. (None of the previous versions, the official version of Google has not opened this function. At present, Google has opened other nfc apis for card simulation operations since Android 5.0. Recently, similar apis have been added to WeChat applet, but I haven't found it yet read the whole passage
-
Recently, the Alpha Team of 360 Mobile Phone Guard exclusively discovered the WeChat remote arbitrary code execution vulnerability and named it badkernel. The Alpha team of 360 mobile phone guards found that through this vulnerability, an attacker could gain full control of WeChat, endanger the user's circle of friends, friend information, chat records and even WeChat wallet, and could affect hundreds of millions of WeChat users, with great harm. At present, relevant researchers of Alpha team have reported this vulnerability to Tencent Emergency Response Center and provided repair suggestions. Use badkernel leak read the whole passage
-
Internet technology is changing with each passing day, and mobile phone products are constantly updated and iterated. I believe that many small partners are the same as Xiao Bian. Kidney 3, Kidney 4, Kidney 5, Kidney 6, Kidney 7 is coming soon. What about updating old mobile phones? Where has your old mobile phone gone? When the Internet has completely penetrated into all aspects of our lives, the recycling of second-hand mobile phones will naturally be thought of through the Internet. As a result, online second-hand 3C product trading platforms, such as idle fish, have gradually become popular, and even O2O recycling platforms, such as AiRecycle, are constantly targeting this increasingly read the whole passage
-
It has to be said that people have become more and more inseparable from wifi. Although desktop computers or laptops also contain network cable interfaces, they have basically been abandoned. This is especially true for mobile tablets. They can only use operator networks and wifi to access the Internet. Once smart homes are popularized, the application field of wifi will also be greatly expanded. The biggest advantage of wifi is that it is convenient and fast without wiring, but it is inherently weak in stability and security. Hackers break through wifi devices to obtain user information is not uncommon. In short, wi read the whole passage
-
Cybercrime now targets Apple users, who guide users to click a payment refund link through more sophisticated phishing techniques to obtain users' personal sensitive data. Early stage of phishing - guiding users into "traps" This new phishing attack is disguised as a refund email from the Apple store. Everything starts with a refund email. First of all, the user will receive an email informing the user that the user ID is in the process of payment transaction, asking whether to confirm the purchase of the product in the email. If not, you need to read the whole passage
-
There is a vulnerability in the AirDrop file transfer function. Malicious applications can be silently installed on millions of Apple devices and replace legitimate apps. AirDrop is a technology developed by Apple to directly and quickly transfer files between devices. However, security researcher Mark Dowd found a serious vulnerability in iOS and OS X systems. An attacker can use this vulnerability to overwrite arbitrary files on the target device. Even if the user does not choose to receive the file, he can also push and install malicious applications to the device. Vulnerability Details Analysis read the whole passage
-
The network black market, as its name implies, is a place on the web where "malicious" services and illegal goods can be bought, sold or leased. Data Value Calculator The black market is experiencing rapid growth, and underground crime is becoming more and more popular. The most profitable product in the black market is user personal information, which is often the purpose of cyber crime. As a global leader in the field of network security software and services, Trendmicro released a network calculator that can calculate the value of data: The author here through read the whole passage
-
WordPress plug-ins or themes that use the Genericons package may be affected by a DOM based XSS vulnerability, because the default WordPress theme TwentyFifteen and the well-known plug-in Jetpack contain the vulnerable page example.html, which affects millions of users. Cause of loophole Any WordPress plug-in or theme that uses the generics package will be affected by this DOM based cross site scripting vulnerability, because usually the generics package contains an example.html file, which contains a base read the whole passage
-
This is a new mobile phone ransomware in Canada. When mobile phone users visit adult websites, they will be infected with this malware and blackmailed. Grasp the victim's shame psychology, the hacker will threaten you to pay ransom, or else lock the screen of his mobile phone, and send the message of you browsing the adult website to all the contacts on his mobile phone. Extortion process The attacker used a new variant of the ransomware Koler on the Android platform. When the user visited the adult website XHamster and infected Koler, the variant showed the victim a piece disguised as coming from Canada read the whole passage
-
At the RSA security conference in San Francisco on Tuesday, researchers presented their latest research results - the 0day vulnerability in iOS 8 "no iOS zone". As the name implies, it can enable Apple's iPhone, iPad, and iPods devices within a certain WiFi range to be restarted continuously. The only thing the victim can do after being attacked is to run away. Overwhelming: "iOS free zone" Adi Sharabani and Yair Amit, researchers of Skycure, a mobile security company, presented their latest research at the RSA security conference in San Francisco on Tuesday. The name of their research is also very aggressive, and it is called "iOS free zone". This read the whole passage
-
Recently Cylance released a serious vulnerability in Windows system, through which an attacker can steal user authentication information. This vulnerability affects all Windows versions, including the latest Windows 10 preview, as well as products of more than 30 companies, such as Adobe, Apple, Box, Oracle, Symantec, etc. Vulnerability Overview This variant vulnerability can be traced back to 1997. It is derived from the classic SMB vulnerability discovered by Aaron Spangler. This security hazard called "Redirect to SMB" (redirect to SMB protocol) will give attackers a chance to rob read the whole passage
-
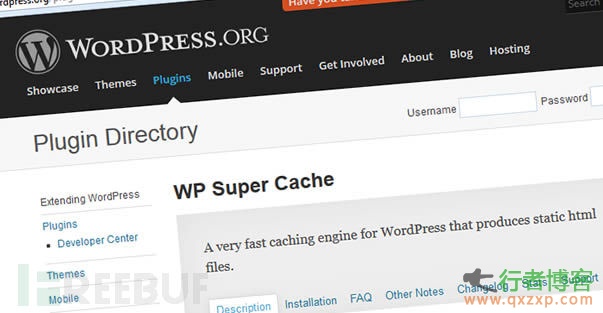
The popular WordPress cache plug-in WP Super Cache recently exposed a high-risk vulnerability, which allows attackers to inject malicious code into pages, putting millions of WordPress websites at risk. WP Super Cache is a classic, old and easy to use cache plug-in, which can greatly improve website performance, so it has always been one of the things that WPers must install. Vulnerability Details An attacker can use a specially constructed query statement to insert malicious script into the plug-in cache file list page. In order to ensure the normal display of content, the page read the whole passage