-
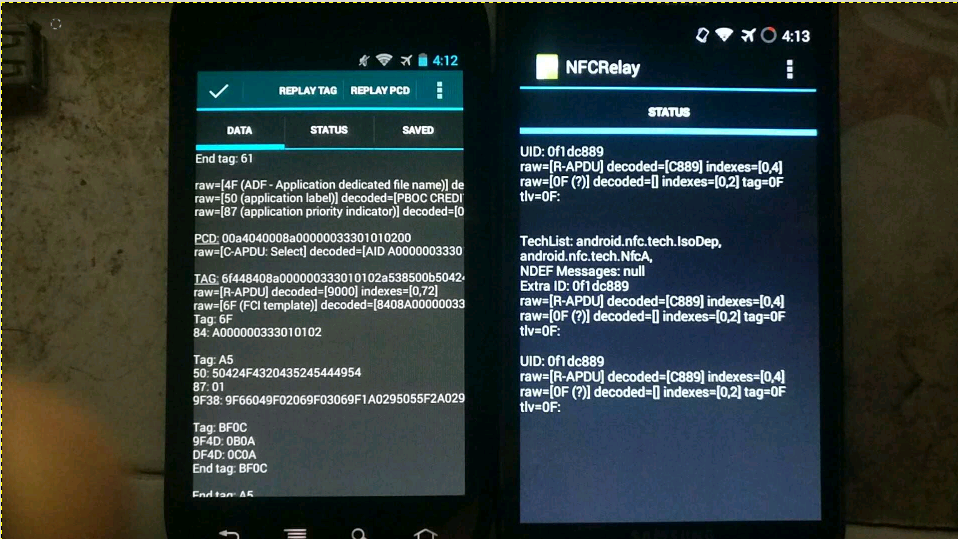
For the theoretical basis, please refer to the PPT of the foreign god: DEFCON-20-Lee-NFC Hacking. I would like to outline the available solutions and functions to be implemented. Test only, do not imitate. Core principles With the help of the CM9 rom version in February 2012, the new nfc read-write tag function can realize software card simulation. (None of the previous versions have this function. The official version of Google has not opened this function. At present, Google has opened other nfc apis for card simulation since Android 5.0. Recently, similar apis have been added to WeChat applet, but I haven't found it yet .. read the whole passage
-
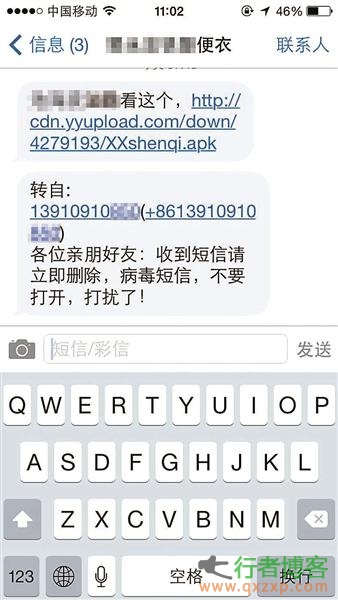
Beijing, Aug. 3 (Reporter Wang Siyuan) According to China Business News, a mobile phone trojan named "locust" suddenly broke out yesterday. After the trojan horse intrudes into the mobile phone, it will automatically impersonate the owner of the phone and continue to send SMS messages to all the numbers in the address book, resulting in pyramid like proliferation. Security experts said that the virus has occurred all over the country at present, with a spread scale of about one million, and the suspect is likely to be a student at school. Website link opens the black hole of fee absorption Li Jun from Zigong, Sichuan received a friend's number at 11:00 yesterday morning .. read the whole passage
-
"XXX (owner's name), ht://********XXshenqi.apk”。 If you receive such a virus containing message, do not click to download it, otherwise the mobile phone will automatically send the message in groups, so that more users will be fooled into joining the group of text messages. As of last night, the police in many places have issued tips on the official microblog to remind mobile phone users not to click to download such software. Lawyers said that if citizens suffered losses due to such software, they would have difficulties in claiming compensation. Lawyers advise users to call the police for help in such cases. ” The incident happened to acquaintances .. read the whole passage
-
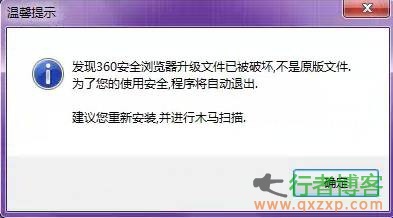
On May 23, 360 Security Center issued a Trojan alert, saying that a pirated system called "Win7GhostSP1 Ultimate Installation Edition" had a built-in Trojan driver (intelk36. sys). Its infection rate has been rising since April this year. Recently, tens of thousands of computers have been recruited every day, which may be related to the reinstallation of some XP computers after Windows XP stopped service. This malicious program parasitic in pirated Win7 is also named "Plague Seven" Trojan Horse. If the computer system of the "plague seven" trojan is loaded, the browser home page and famous shopping websites such as Taobao will be hijacked by the trojan .. read the whole passage
-
For a long time, online games have been the target of hackers, and popular works such as World of Warcraft are "big cakes". Today, Blizzard released a blue post to report the latest discovery of the new stolen number trojan. Juranok, the community manager, said in the latest post that the Blizzard team has received a report about a new trojan virus recently, which can even steal accounts with security token protection. It can steal your account by sending your account, password and security token information to the account thief in real time .. read the whole passage
-
The National Computer Virus Emergency Response Center found that a malicious backdoor_Idr. A variant of backdoor_Idr. A has recently emerged through the monitoring of the Internet. This variant masquerades as a picture icon to entice computer users to click to run. After the variant runs, it will release a picture to confuse computer users, and it will also release a dynamic link library file, and load and decrypt it. Once the DLL file is decrypted, the infected operating system will actively connect to the Web server designated by the malicious attacker to receive and execute the remote transmission .. read the whole passage
-
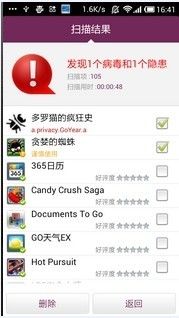
Computer viruses have always been a deadly weapon for hackers to steal user information. With the proliferation of mobile phone users, hackers have focused on mobile phone users and developed various mobile phone virus software, which has brought losses to users. The mobile phone virus "GoYear" uses confusion+encryption to automatically ROOT the mobile phone and gain the highest authority to completely control the mobile phone, steal the user's address book, SMS, account password and other private information, and send it back to the hacker in the background. At the same time, it will also carry out rogue promotion and automatically download applications on users' mobile phones, which will consume a lot of hands .. read the whole passage
-
The National Computer Virus Emergency Treatment Center found that a malicious trojan Trojan_Generic. F recently appeared through the monitoring of the Internet. The malicious trojan program disguised itself as a Java upgrade program by modifying the key values related to the registry of the infected operating system to automatically start with the system boot. After the malicious trojan/program runs, it will find the host process in the infected operating system and inject itself into the process file. At the same time, the trojan will copy itself to the designated directory of the infected operating system and rename it .. read the whole passage