-
Some of the technologies and tools mentioned in this article may be offensive and are only for safe learning and teaching purposes. Illegal use is prohibited! Software Introduction This software is a website security detection software for White Hat. The software is completely free. You can use this software to analyze the site and help you get more information from the side. During the use of the software, some anti-virus software may prompt you to visit unsafe websites and upload information. This operation is caused by third-party sites querying the host location, This product does not contain any back door, please feel free to use it read the whole passage
-
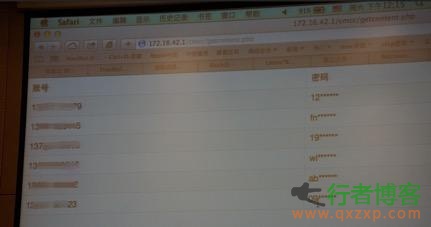
The network black market, as its name implies, is a place on the web where "malicious" services and illegal goods can be bought, sold or leased. Data Value Calculator The black market is experiencing rapid growth, and underground crime is becoming more and more popular. The most profitable product in the black market is user personal information, which is often the purpose of cyber crime. As a global leader in the field of network security software and services, Trendmicro released a network calculator that can calculate the value of data: The author here through read the whole passage
-
On March 15, CCTV once again focused on the security of mobile phone applications, exposed the security of free WiFi at the party, and demonstrated to everyone on the spot that it used fake phishing WiFi technology to steal the online content of audience. Frankly, many mobile phone users are also used to "surfing the Internet". They like to log in to WiFi in public places such as cafes, teahouses, hotels and so on for various operations, which is quite unsafe! ”West Lake Debate "-- Sheep Wall of China SIS Conference In the "West Lake Debate read the whole passage
-
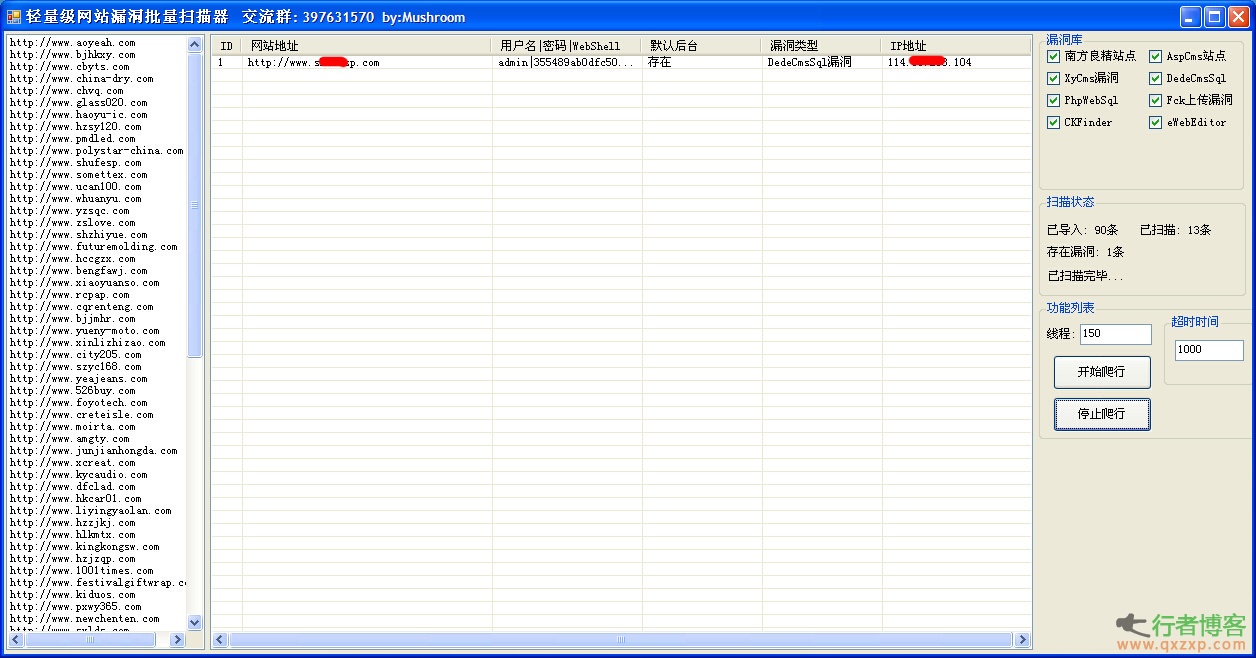
Lightweight website vulnerability batch scanning artifact (website vulnerability detection tool) is a green and free website vulnerability scanning and detection tool. The software is powerful. It can test the security of your website through web crawlers and detect popular attacks, such as cross site scripts, SQL injection, etc., can be used to crack small websites, help us find various vulnerabilities effectively and quickly, increase the security of websites, and immunize against various network attacks in advance. How to use lightweight website vulnerability batch scanning artifact 1. Right click on the left margin of the software and select "Import Site" (event read the whole passage
-
In 2001, a seven day and seven night "Sino US Hacker War" made Chinese people who were not familiar with the Internet world realize a new group - hackers. The network has been rapidly popularized in China at an unimaginable speed. Hackers have never stopped their black hat and white hat wars against network security. In 2013, 552 million people around the world leaked their identity information due to hacker attacks, while in China, 164 million people were injured due to cyber crimes, with an average loss of 224 dollars per person. With the growing popularity of smart phones, 12 million malicious links against smart phones are available at any time read the whole passage
-
The OpenSSL "heart bleed" vulnerability is far more serious than expected. Some users have not considered that a large number of applications on mobile phones also require account login, and many of their login services are built by OpenSSL. Therefore, before the vulnerability is repaired, it is very easy to lose user account information by logging into online banking, online shopping and other important accounts with mobile phones. The password needs to be changed in time after the vulnerability is patched. After the news of "vulnerability" broke out, the AVL mobile security team under Antian quickly accessed the login portal of mainstream online banking, online shopping, securities, and airline travel software read the whole passage
-
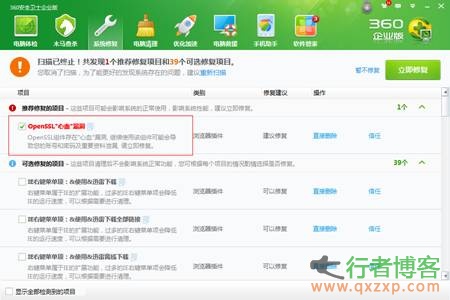
The radiation range of OpenSSL "heart bleeding" vulnerability is expanding. At Cisco After Juniper network equipment is exposed to the impact of this vulnerability, A large number of software on Windows has also been found to have vulnerabilities, which can be used by hackers to attack Internet users' computers and capture private data such as keys. The attack code has been published on GitHub, a foreign technology website. In this regard, 360 security guards launched an emergency vulnerability repair program on the evening of the 10th, which is the only PC security software that can prevent this vulnerability at present. When the "heart bleeding" vulnerability was just exposed, hackers mainly attacked read the whole passage
-
What is Heartbleed? "Heart Bleeding" loophole, OpenSSL is one of the most catastrophic vulnerabilities in history. It may have been discovered and used for two years. It was announced a few days ago. If you don't introduce too much, just know the severity. This vulnerability will affect all websites and services using the https encryption protocol, including but not limited to Gmail and Facebook - these websites may have been monitored by malicious people to obtain your important information, including but not limited to your account, password, credit card number and password. We don't know whether there is read the whole passage
-
With the rise of e-commerce, many small and medium-sized enterprises have their own servers. Internally, it is used to establish a LAN to improve office efficiency; Establish a website to publicize the products and image of the enterprise more widely and strive for more customers. However, as the core product of the network, the server technology is relatively complex, especially in the era of virus ridden network, the security problem becomes more prominent. The author has been managing the server and checking its security in the company for some time, and has accumulated some experience in practical work, hoping to share it with everyone. 1、 Enhanced Network read the whole passage
-
Write in front In fact, before I translated this article, I thought it might be a client script based technology, similar to xss. But through translation, I learned that web bugs are usually written by client server scripts. Compared with some hackers who use it to invade, it is more official to use web bugs to collect user information without the user's knowledge. Introduction Nowadays, the Internet technology has made great changes in people's daily life. People exchange information with each other through the mouse and keyboard. The complexity of information read the whole passage
-
It is reported that Microsoft pointed out earlier that between July 2012 and July 2013, XP shares 30 security vulnerabilities with Windows 7 and Windows 8. Now, this sharing mode will become a new way for hackers to find Windows XP vulnerabilities, that is, to find XP vulnerabilities through reverse engineering. A new way for hackers to discover shared XP vulnerabilities (picture from ITxinwen) It is reported that after Microsoft ends its support, one of the major problems it will face will be security vulnerabilities, which means that when Microsoft releases new security patches for Windows 7 and Windows 8, hackers can read the whole passage
-
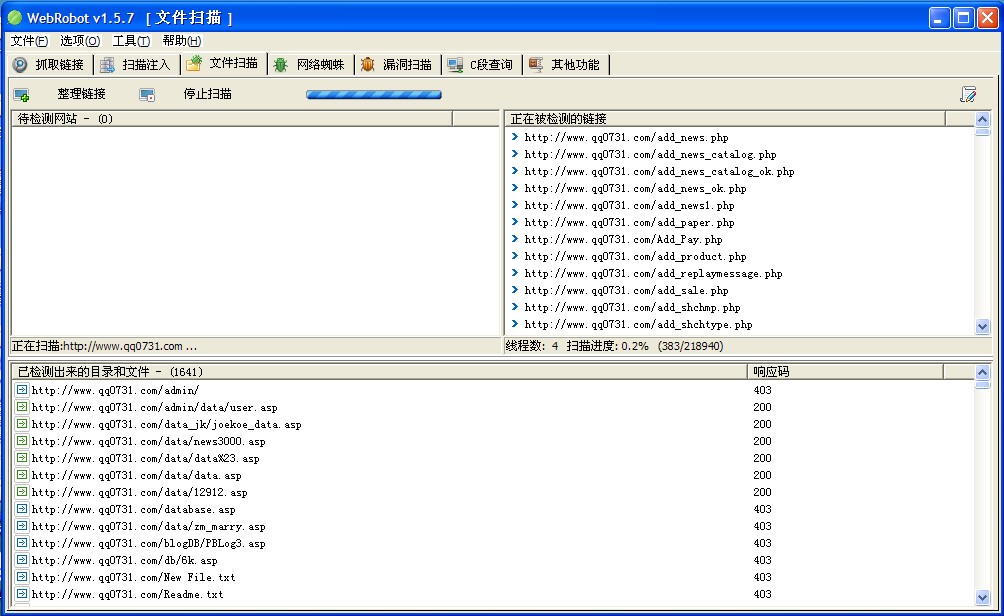
Artifacts WebRobot v1.5.7 Quick Sidenote Tool The functions are as follows: 1. Batch detection (batch search for injection points and sensitive files for fast and efficient detection of network security) 2. Sidenotes 3. Added the last file directory scanning tool 4. You can add keywords with vulnerabilities to search 5. Grab all links of the specified page 6. Get the content of page explosion error, and add keywords by yourself 7. Other functions will be added later depending on the situation Update the following 1. [Grab link] Add Google and Baidu search read the whole passage