-
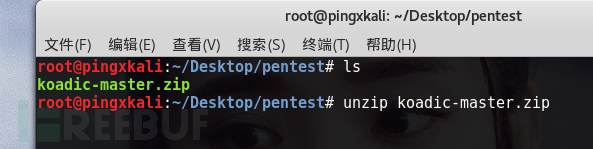
preface: I saw a recommended tool Koadic on a friend's blog. After I contacted it, I found that it was very good. I thought that the power of this tool was the various module functions after I got the shell. I will write it myself and send it to you. First, clone the project locally: Project address https://github.com/zerosum0x0/koadic.git Then unzip it. If you want to install it to the directory you specified, you should first cd it to that directory and download it. I copied it there, so I unzip it. As shown below Run koadic cd ko... read the whole passage
-
I don't know if you have heard of Hak5 products. They are the favorite products of hackers and penetration testers. Among them, many PoC hacking tools have appeared in the popular American TV series The Hacker Corps. It has been several weeks since Hak5's PACKETSQUIRREL was launched. In this article, I will analyze this $59 "gadget" and make a similar tool at a low cost. What is PACKET SQUIRREL? This is a multi-functional Ethernet tool, which can provide us with highly concealed remote .. read the whole passage
-
The cracking software provided in this article is for software trial only, please delete it within 24 hours. As we all know, Burp Suite is a resounding web application penetration test integration platform. From the initial mapping and analysis of the application attack surface to the process of finding and exploiting security vulnerabilities, all tools work together seamlessly to support the overall test program. All tools in the platform share the same robust framework to uniformly handle HTTP requests, persistence, authentication, upstream agents, logging, alarms, and scalability. Burp Suite allows attackers .. read the whole passage
-
Do a little research on passwords . Zi Fei SpongeBob (Hehe) | 2014-09-24 13:44 Recently, I have been researching and infiltrating, and found some rules of passwords. I want to write a tool, so I want to investigate something The most common combination of passwords is letter+number The most frequently used symbol should be _ underline... because it seems that the mailbox symbol only supports this habit in those days 1. Alphabetical part: the first letter of each word of the name in the general four names For example, Wang Xiaoming The letters in the password are generally wang xia read the whole passage
-
0x01 Lead Well, I want to infiltrate the bank and take photos at the same time, but there are too many people... I just succeeded here twice. It was stated that I was just a friendship test and did not do any damage. In addition, I put forward my own penetration test ideas for banks to provide some suggestions for the safety construction of banks. I'm not good. If there is anything wrong, please correct it. 0x02 Let's talk about the bank's ATM first The ATM in China is very safe. Anyway, I have no way to deal with it. If you are abroad, you can try these methods. Some ATMs read the whole passage
-
1、 Penetration test concept Penetration test does not have a standard definition. Some foreign security organizations have reached a consensus that penetration test is an evaluation method to evaluate the security of computer network systems by simulating the attack methods of malicious hackers. This process includes the active analysis of any weakness, technical defect or vulnerability of the system. This analysis is carried out from the location where an attacker may exist, and from this location, the security vulnerability is conditionally exploited. The penetration test also has two obvious features .. read the whole passage
-
1. Analyze the content and functions of the target website (1) First, determine which language the website is written in Or whether there are mixed uses This can be obtained by viewing the website source file, observing website links, capturing submission requests, etc (2) Crawl the website directory, and use tools to crawl the website directory, which can help the previous step to make the results more accurate Archive the crawling results. If possible, analyze whether the website uses a common program here, and if so, record it Proceed to the next step (3) According to the results of the previous step, the site root directory or .. read the whole passage
-
1. What is a domain Some people say that domain is an organizational structure and a security boundary. The domain also has another name, Active Directory. No matter what the domain is, it always has some characteristics. With it, it is much easier to manage an organization's organizational units, personnel, especially computers, because the domain is built on computers. It will be very convenient to join computers in the domain, share files, and share Internet access. The domain has an important role, domain controller (DC). It has supreme authority. It can be used for other users in the domain .. read the whole passage
-
There are many ways to hack social workers. First of all, I heard that Kameng of KaTesco is more active recently. Then I will talk about how the webmasters of Kameng of social workers are generally non mainstream MCs, and there are more accounts registered everywhere. Now let's talk about the social work sub station, and we will share with you our main social work station, Kameng. First of all, check your pants. Maybe not, because they have many forum accounts registered. I've done three or four with pants. There is also a more commonly used, now .. read the whole passage
-
Simple analysis of various network environment penetration tests 1、 Penetration test concept Penetration test does not have a standard definition. Some foreign security organizations have reached a consensus that penetration test is an evaluation method to evaluate the security of computer network systems by simulating the attack methods of malicious hackers. This process includes the active analysis of any weakness, technical defect or vulnerability of the system. This analysis is carried out from the location where an attacker may exist, and from this location, the security can be actively used conditionally .. read the whole passage
-
Some experience summary of webshell empowerment of server empowerment. First, WEB SHELL privilege promotion skills C:\DocumentsandSettings\AllUsers\ApplicationData\Symantec\pcAnywhere\ See whether you can jump to this directory. If it works, it's best. Directly download its CIF file, crack it to get the pcAnywhere password, and log in c:\ProgramFiles\serv-u\ C:\WINNT\system32\config\ Run its SAM and crack the password c:\winnt\system32\inetsrv\data\ Is servernone read the whole passage
-
Scorpio web security penetration test toolset ScorpioV5 software screenshot: More functions will be found by the users themselves. Plug in update function. For the following functions, you only need to update the plug-in. Operating environment: windows xp,win7,win8, + .net4.0 Solve the problem of win8 crash Solve the problem of killing soft drugs Function will not be used? Please click Help in each function window. You can also view the instance description in the directory. Doc document Download address: http://pan.baidu.com/s/17V5WV read the whole passage