-
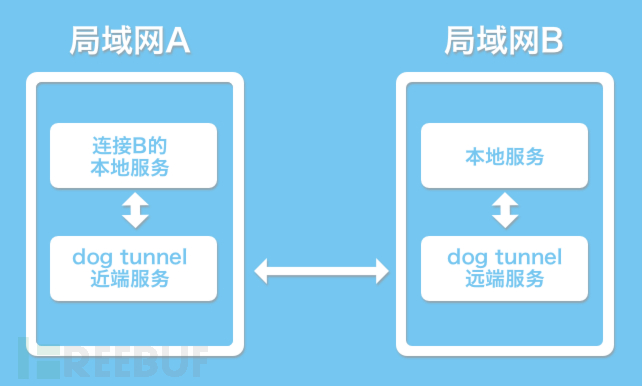
Goudong is a high-speed P2P port mapping tool, which also supports Socks5 proxy. Open source starts after version 0.5, The UDP bottom layer is rewritten based on the open source library KCP, which greatly improves the efficiency and has obvious advantages in harsh environments. At the same time, non P2P version (Lite version) is provided. The connection process at both ends does not rely on the intermediate server at all. It supports encryption and login authentication, and automatic reconnection. However, it needs to manually ensure that both ends can connect normally (otherwise, please use the default P2P version) function The remote designated port can be mapped to the near end through the doghole for high-speed access characteristic ... read the whole passage
-
000Webhost, the world's most popular free web hosting company, encountered a large-scale data leakage event, with 13.5 million users' personal data leaking. FreeBuf encyclopedia: 000webhost 000webhost is a free virtual host product owned by Hosting24, a famous foreign space provider, which is known as "better than paid virtual hosts". And indeed, as said, the space is very high-quality and stable. The space provider has also seen that China has a large population, and it is difficult for Chinese users to apply. His reputation is really good. 000webhost provides read the whole passage
-
IBM has discovered a new type of data theft malware called Corebot. It is a highly modular malware, and some security detection systems will recognize CoreBot as Dynamer! Ac or Eldorado. It specializes in stealing system, email credentials, and software keys, and even downloading and executing other malicious programs. Once the attacker collects the above sensitive information, it will be sold to criminal organizations. Relatively speaking, what can attract the attention of security researchers is information theft malware, remote access tool (RAT), ransomware read the whole passage
-
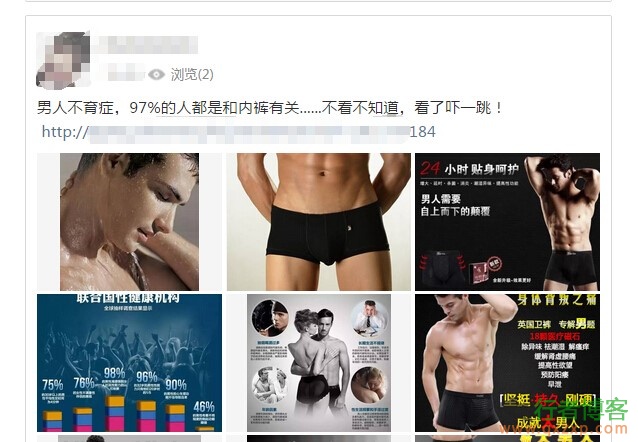
We often see that QQ space automatically forwards some bad information with links, even though our QQ password has not been stolen. Recently, through the analysis of a QQ space automatic forwarding link, it was found that the automatic forwarding mechanism carefully constructed the code to obtain the user's QQ number and key value by using the vulnerable page of Tencent website, thus obtaining some sensitive operation permissions of the user. And through this vulnerability, it automatically forwards some bad information to induce users to click, thus leading to large-scale dissemination. Communication phenomenon If one day, you find many Q's read the whole passage
-
Router Scan is a router security testing tool that can specify IP segments to perform security tests such as brute force cracking on routers, and supports multiple TP-LINK Routers of Huawei, Belkin, D-Link and other major brands are a set of security testing tools developed by Russian security personnel. Support router model Black 2.0 (в разработке) DSL-AC68U EA-N66 RT-AC66R RT-AC87U RT-N11P RT-N66W WL-566gM HG – Cisco: Linksys WRT54G2 – D-Link: DAP-1150 ... read the whole passage
-
The cracking method provided in this article is for software trial only, please delete it within 24 hours as everyone knows, Burp Suite is a resounding web application penetration test integration platform. From the initial mapping and analysis of the application attack surface to the process of finding and exploiting security vulnerabilities, all tools work together seamlessly to support the overall test program. All tools in the platform share the same robust framework to uniformly handle HTTP requests, persistence, authentication, upstream agents, logging, alarms, and scalability. Burp Suite allows attackers to read the whole passage
-
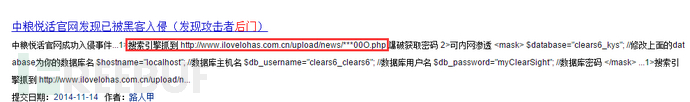
Shenzhen Longgang Police announced a case of computer information system destruction, and found that the "hacker" who invaded the company's server was a criminal suspect who had only junior high school education and learned to be a "god" of the network by himself, and the "hacker" was only a coal miner when he developed the plug-in. On the 14th, the Shenzhen Longgang police announced a case of computer information system destruction. The police said that a leisure online game server independently developed and operated by a computer company in Shenzhen was abnormal. After checking, it was found that someone had used an illegal plug-in to enter the company's server read the whole passage
-
Recently Cylance released a serious vulnerability in Windows system, through which an attacker can steal user authentication information. This vulnerability affects all Windows versions, including the latest Windows 10 preview, as well as Adobe, Apple Box, Oracle, Symantec and other products from more than 30 companies. Vulnerability Overview This variant vulnerability can be traced back to 1997. It is derived from the classic SMB vulnerability discovered by Aaron Spangler. This security hazard called "Redirect to SMB" (redirect to SMB protocol) will give attackers a chance to rob read the whole passage
-
If we can learn anything from the various hacker attacks that took place in 2014, I believe everyone will come to the same conclusion that today's hacker attacks have become more and more intelligent and deadly. In the recent Sony Pictures blackout, we can see that the purpose of hackers to invade the system is not only to destroy the system, but also to completely destroy their own intrusion targets. Not long ago, the United States "Star Spangled Banner" website published "Russia and Georgia war only a few read the whole passage
-
Verizon released the 2014 Data Leakage Investigation Report, which reviewed 63737 cyber security incidents and 1367 confirmed data leakage incidents. The report data shows that the information leakage caused by the database is up to 25%. Make an inventory of the data leakage events at home and abroad in 2014, and explore the underlying technical reasons. In fact, there are still many leakage events, which are either under investigation, unconfirmed or undisclosed. It can be predicted that more serious leakage events may occur in 2015. FreeBuf Science Popularization: What is read the whole passage
-
Write in front Penetration testing is both a technology and an art. This technology (art) was not known by everyone at the beginning. It is the so-called that no one can walk at birth, from never knowing to getting started to becoming familiar with it, step by step, everyone is like this; But in this process, thinking is undoubtedly the most important thing. It's just like we solved problems in high school when we had ideas. It's sad to hold a shovel (technical knowledge) but not where to start. Here are some general rules I summarized read the whole passage
-
In the last two years, PoS malware due to Target, Home Depot The POS attack that Kmart encountered has attracted wide attention. With the arrival of Black Friday shopping season, PoS malware is bound to attract attention. PoS attackers will not only rely on their own malware to attack and steal victim data. They will also use a large number of other tools to achieve their goals. Some are also used by system administrators, such as putty, and some are software in the Sysinternals Suite toolkit provided by Microsoft. Through these workers used by hackers read the whole passage