-
Caution for Android devices: versions 4.0-4.3 can be fixed by RCSAndroid. The remote control trojan RCSAndroid on the Android platform is one of the most professional and complex malicious programs exposed in Android. Since the Hacking Team's information disclosure, the security field has been exposed to some vulnerabilities every day Exp and other messages, of course, there is more information to be mined. Now, it's finally Android's turn. Unfortunately, it's very bad news: a new remote access trojan (RAT). RCSAndroid has ten "super abilities" Trend Technology read the whole passage
-
Shenzhen Longgang Police announced a case of computer information system destruction, and found that the "hacker" who invaded the company's server was a criminal suspect who had only junior high school education and learned to be a "god" of the network by himself, and the "hacker" was only a coal miner when he developed the plug-in. On the 14th, the Shenzhen Longgang police announced a case of computer information system destruction. The police said that a leisure online game server independently developed and operated by a computer company in Shenzhen was abnormal. After checking, it was found that someone had used an illegal plug-in to enter the company's server read the whole passage
-
Verizon released the 2014 Data Leakage Investigation Report, which reviewed 63737 cyber security incidents and 1367 confirmed data leakage incidents. The report data shows that the information leakage caused by the database is up to 25%. Make an inventory of the data leakage events at home and abroad in 2014, and explore the underlying technical reasons. In fact, there are still many leakage events, which are either under investigation, unconfirmed or undisclosed. It can be predicted that more serious leakage events may occur in 2015. FreeBuf Science Popularization: What is read the whole passage
-
1. The definition of social engineering is not that you simply search the victim's information on the Internet, which is not even a narrow sense of social engineering. The activities you want to carry out are not limited to narrow social engineering. You need to carry out some in-depth interactive behaviors with victims or information owners. ① In this process, we should make full use of the known information, especially the information extended in search engines, to increase trust. For example, Google Maps can be used to explore the surrounding environment, or to understand the victim's interpersonal relationship and online activity. ... read the whole passage
-
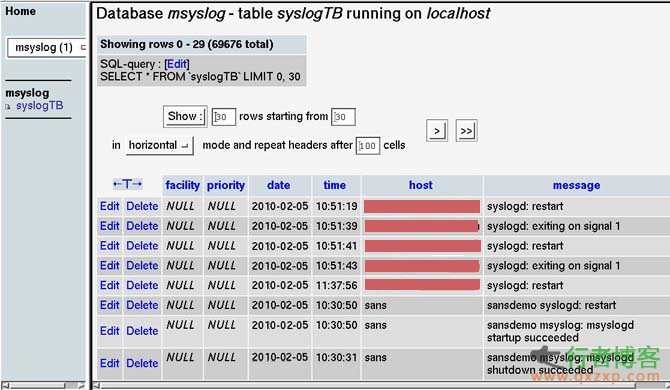
This article will provide a brief overview of log collection and analysis. Specifically, we will focus on three basic issues: log transmission, log collection, and log analysis. It also involves simple log storage and archiving. The purpose of writing this article is to further discuss the log processing of the Linux system retained by the court scene analysis. Log transmission ~~~~~~~~~ First, let's look at log transmission. The traditional UNIX log transmission mechanism is UDP, port 514. Log messages are sent and received by the system log daemon read the whole passage
-
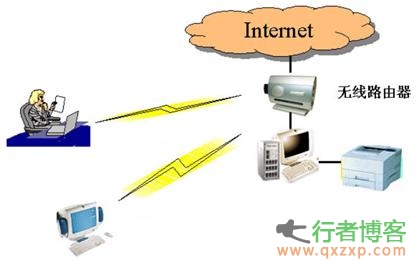
Routing security is a big topic. The background settings of the router are too professional, and the network card is popular. The legendary hacker seems to have disappeared... It seems that the router at home is hopeless. As long as there is a hacker who knows something about it, he will be attacked every minute. Zhaikejun (public account "Letshome") has previously discussed this topic from multiple perspectives, including technical analysis, testing, protocol specification traceability, etc. However, in these things, there is no talk about the security mechanism of routing itself that has been developed for many years. We ignored the heaviest read the whole passage
-
A summary of the foundation, please stay away! Intrusion introduction: 1 upload vulnerability; 2 Storehouse; 3 injection; 4 Side notes; 5 Cookie spoofing 1. Uploading vulnerability is a common form of intrusion. Some websites have upload vulnerabilities, and webshell can be directly obtained through upload vulnerabilities Forms:/uploadfile.asp,/uploadfile.asp and then through the upload tool. 2. Vulgaris is to submit characters to get database files. This vulnerability is also common now, and it is also a kind of Google hacking Command: inurl: co read the whole passage
-
Review of a week's overseas security incidents (9.29-10.05): gratitude and resentment between hackers and games Last week, a hacker gang targeting game companies was ambushed in the United States. The list of stolen software includes the training program of American attack helicopters. This review will focus on the relationship between hackers and games. Last week, a transnational network criminal gang was arrested in the United States. The criminal gang consists of six people from the United States, Canada and Australia. Among the gang members, the oldest is 28 years old, the youngest is 18 years old, and the amount involved is up to read the whole passage
-
Perfect log cleaning summary 1: Start – Programs – Administrative Tools – Computer Management – System Tools – Event Viewer, and then clear the log. 2: The log files of Windows 2000 usually include application log, security log, system log DNS server logs FTP logs WWW logs, etc. Log file default location: Application log, security log, system log The default location of DNS logs is% sys temroot% system32config. The default file size is 512KB. Administrators will change the default size. Ann read the whole passage
-
How to invade the designated website! First, observe the designated website. Intrusion of designated websites requires conditions: You should first observe whether the website is dynamic or static. First, I will introduce what sites can be invaded: I think they must be dynamic websites such as ASP PHP, JSP and other code writing sites If it is static (. htm or html), it will not succeed. If the target website to be invaded is dynamic, you can use the vulnerabilities of dynamic websites to invade. Quote: The following are common ways to invade websites: 1. Upload vulnerability If read the whole passage
-
1、 Penetration test concept Penetration test does not have a standard definition. Some foreign security organizations have reached a consensus that penetration test is an evaluation method to evaluate the security of computer network systems by simulating the attack methods of malicious hackers. This process includes the active analysis of any weakness, technical defect or vulnerability of the system. This analysis is carried out from the location where an attacker may exist, and from this location, the security vulnerability is conditionally exploited. The penetration test also has two obvious read the whole passage
-
First of all, declare that: 1. The scope of intrusion only includes the LAN. If you are in a school, you can invade the entire campus network; 2. The only machine that can intrude is the weak password (the user name is administrator, etc., and the password is empty), or the machine that knows the account password and has opened port 139 but has not opened the firewall. Intrusion tools: Generally, three are used: NTscan abnormal scanner, Recton – D special edition of He Mian Kill, DameWare Mini Chinese 4.5 (The first two tools, antivirus software, will report viruses. It is recommended that the real-time antivirus software be temporarily turned off and this read the whole passage