-
It has to be said that people have become more and more inseparable from wifi. Although desktop computers or laptops also contain network cable interfaces, they have basically been abandoned. This is especially true for mobile tablets. They can only use operator networks and wifi to access the Internet. Once smart homes are popularized, the application field of wifi will also be greatly expanded. The biggest advantage of wifi is that it is convenient and fast without wiring, but it is inherently weak in stability and security. Hackers break through wifi devices to obtain user information is not uncommon. In short, wi... read the whole passage
-
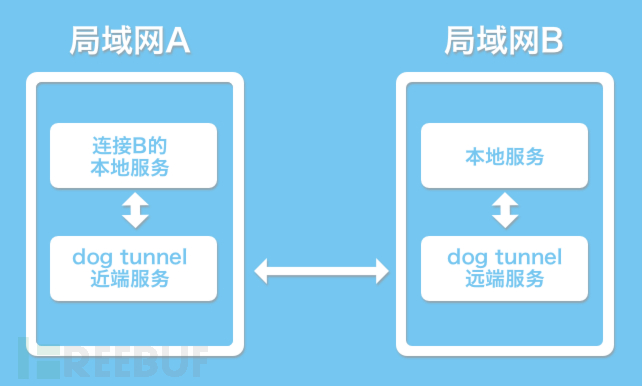
Goudong is a high-speed P2P port mapping tool, which also supports Socks5 proxy. Open source began after version 0.5. The UDP bottom layer is rewritten based on the open source library KCP, which greatly improves the efficiency and has obvious advantages in harsh environments. At the same time, non P2P version (Lite version) is provided. The connection process at both ends does not rely on the intermediate server at all. It supports encryption and login authentication, and automatic reconnection. However, it needs to manually ensure that both ends can connect normally (otherwise, please use the default P2P version) function The remote designated port can be mapped to the near end through the doghole for high-speed access characteristic ... read the whole passage