-
Now, because all gods share some Oday vulnerabilities in the public website program, we can use our website webshell For example, the common upload vulnerability of the dynamic network, SQL injection vulnerability of various websites, database explosion vulnerability, overflow vulnerability, etc.. However, only obtaining the webshell of the website can no longer meet our needs. We want to further obtain the administrator permissions of the website server through webshell. Here is Xiaocan's introduction to 20 common webshell empowerment ideas I collected. 1. SER-TU authorization (usually using SERFTP server management read the whole passage
-
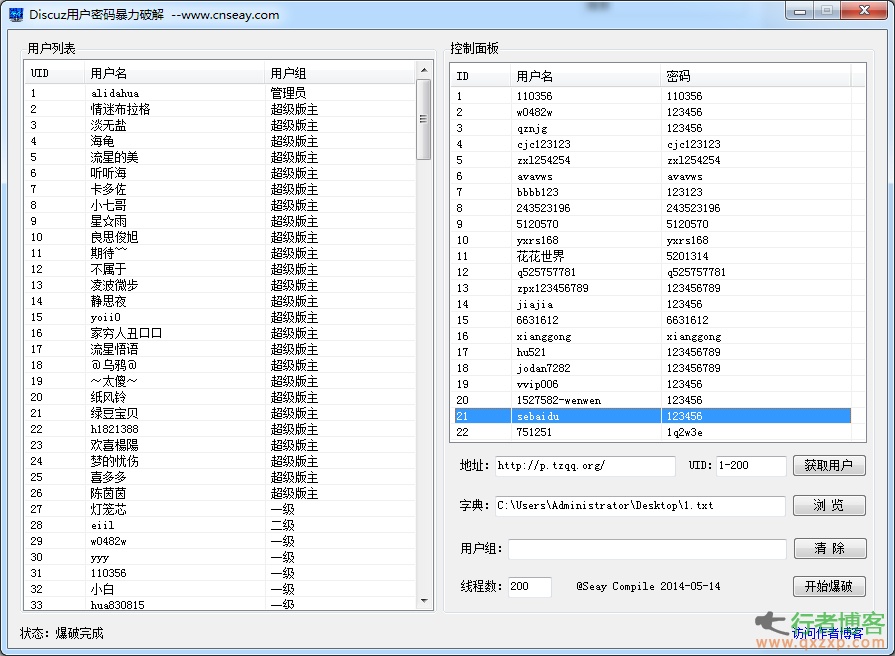
explain: 1. Support discoz X1/1.5/2/2.5/3/3.1 and other versions. 2. The program will automatically judge the code. 3. Those with verification code cannot be exploded. 4. Dictionary supports% username% to use user name as password (% username% 123) 5. Support exporting user name list and successfully exploded list 6. Don't find me when the AV forum is caught If you want to blow up users in only a few specific user groups, you can select an unwanted user group after obtaining the user list, right-click to copy the user group, paste it into the user group input box below, and click read the whole passage
-
On May 23, 360 Security Center issued a Trojan alert, saying that a pirated system called "Win7GhostSP1 Ultimate Installation Edition" had a built-in Trojan driver (intelk36. sys). Its infection rate has been rising since April this year. Recently, tens of thousands of computers have been recruited every day, which may be related to the reinstallation of some XP computers after Windows XP stopped service. This malicious program parasitic in pirated Win7 is also named "Plague Seven" Trojan Horse. When the computer system of the "plague seven" trojan is loaded, the browser home page and famous shopping websites such as Taobao will be hijacked by the trojan read the whole passage
-
1、 Ping It is a command used to check whether the network is unblocked or the network connection speed. As an administrator or hacker living on the network, The ping command is the first DOS command that must be mastered. Its principle is as follows: all machines on the network have unique IP addresses. We send a packet to the target IP address, and the other party will return a packet of the same size. According to the returned packet, we can determine the existence of the target host, The operating system of the target host can be preliminarily determined. below... read the whole passage
-
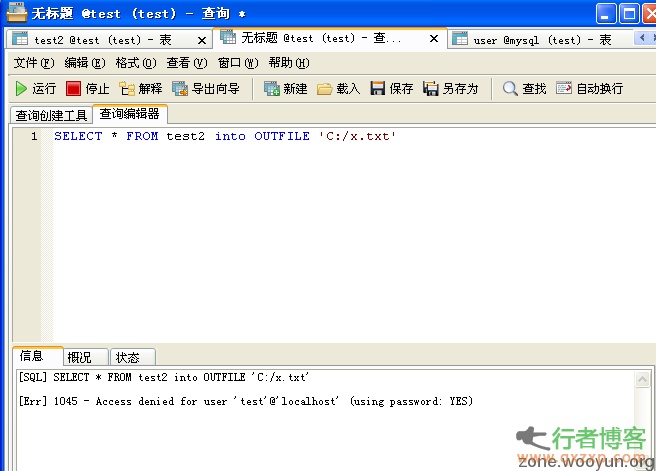
cnrstar (Be My Personal Best!) | 2014-05-20 21:58 As we all know, MySQL users cannot read files through Load_file or write files through into dumpfile or into outfile without File permission, but occasionally find a trick on a website, that is, they can read local files to the database through load data infile, so that we can read files on the server through this bug under low permissions. The codes are as follows: LOAD DATA L... read the whole passage
-
On May 22, it was reported that two foreign hackers had found a way to unlock the stolen Apple devices, according to foreign media reports. In recent days, the two hackers posted many photos of unlocked iPhones and iPads on their Twitter pages. This is "good news" for thieves who steal iPhones and iPads. Apple devices have anti-theft protection function, that is, the "activation lock" option. Users can connect to Apple servers through iCloud services, set passwords remotely and delete all personal data. When the thief swipes the software read the whole passage
-
On May 22, according to the Associated Press, eBay asked users to change their login passwords because the database containing customer names, passwords, e-mail addresses, addresses, phone numbers, birthdays and other information was hacked. EBay said on Wednesday local time that there was no evidence that users' financial information or credit card information had been stolen, and there was no evidence that the attack led to hackers illegally using 145 million active users' accounts. EBay said that the company was investigating the incident, and it was not clear what was affected read the whole passage
-
Social engineering has become one of the most popular attacks at present, and it always appears in some large data leakage cases. For example, RSA break encountered targeted phishing and loading vulnerable Excel files in 2011. Therefore, for enterprises capable of simulating real attacks, social worker penetration testing should become a mandatory strategy for each penetration testing toolkit. Social workers' behavior is very dependent on psychology, and there are many very suspicious lures that can persuade people to engage in certain operations. For example, Robert Cialdini read the whole passage
-
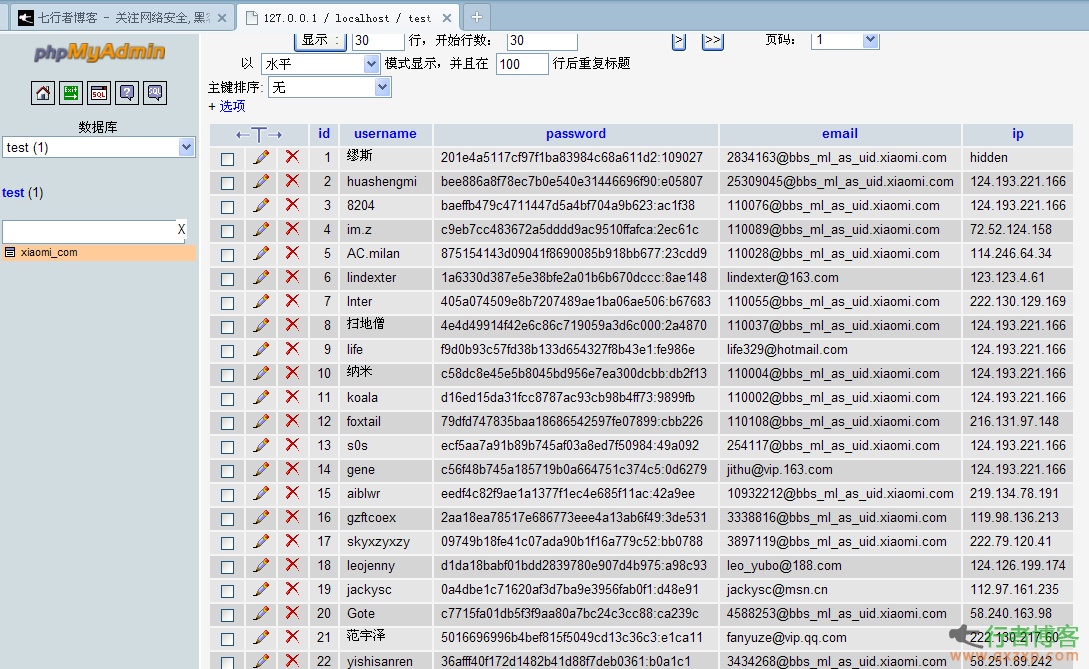
One time analysis of data leaked by Xiaomi Forum, the successful password cracking rate is up to 37.8% Pig Man (A) | 2014-05-14 13:20 Number of leaked data 8281387 The specific time of being stripped is 14:08, June 15, 2012 Started to be spread at 15:51 on May 13, 2014 Time of uploading Baidu disk: 21:29, May 13, 2014 Success rate of password cracking Number of sampling records: 1000 Number of successful samples: 378 Sampling success rate: 37.8% The data was packed at 15:51 on May 13, 2014. This test will sample 1000 passwords for cracking; ... read the whole passage
-
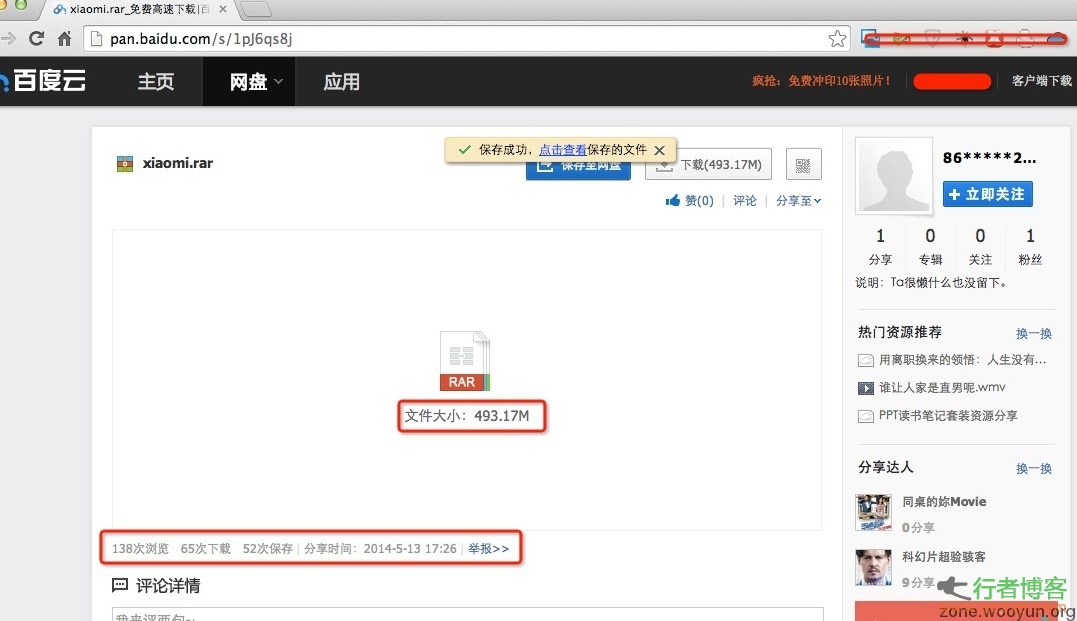
The data of Xiaomi's official forum was leaked on May 13, with 8281387 (about 8 million) leaked data. After data analysis and comparison, Pop found that the leaked data were all forum account information registered before August 2012. The leaked data is encrypted with an independent Salt one-way hash value, but simple passwords can still be quickly cracked. The leaked data is xiaomi.rar, which contains three files (xiaomi_com.frm, xiaomi_com.MYD, and xiaomi_com.MYI) File: xiaomi_com.frm Size: 8690 ... read the whole passage
-
Cyber attacks form an industry and interest chain On May 13, Dongfang.com reported that online game platforms could not log in during prime time. What happened? A few days ago, the Xuhui Public Security Branch received an alarm that the online game platform had been attacked, and the investigation found that the culprit behind it was a network attack criminal gang. Since 2012, in order to seek illegal interests and exclude horizontal competition, this gang led by Tu has acquired bandwidth traffic controlled by hackers, and then organized network attack teams to continuously attack specific websites, making these read the whole passage
-
It is completely possible to collect and infiltrate information from a site by using Google. Now let's test a specific site with Google. ————————————————————————————————————— First, use Google to see some basic information of the site (some details are omitted): site:xxxx.com From the returned information, find the domain names of several departments of the university: http//a1.xxxx.com http//a2.xxxx.com http//a3.xxxx.com http//a4.xxxx.com By the way, ping should be in read the whole passage