Recently, the Alpha Team of 360 Mobile Phone Guard exclusively discovered the WeChat remote arbitrary code execution vulnerability and named it badkernel. The Alpha team of 360 mobile phone guards found that loophole Attackers can gain full control of WeChat, endanger users' circle of friends, friend information, chat records and even WeChat wallets, and affect hundreds of millions of WeChat users, with great harm. At present, relevant researchers of Alpha team have reported this vulnerability to Tencent Emergency Response Center and provided repair suggestions.

Using the badkernel loophole Quasi worm like communication can be carried out, and a single user can send friends and group links after winning the WeChat call; It can also obtain users' private information, including address book, SMS, recording, video, etc; At the same time, it may cause users' property losses. By recording WeChat payment passwords, automatic transfer and red envelope sending can be carried out.
In addition, users are most vulnerable to daily use scenarios such as using WeChat to scan, scan QR codes, click links in circles of friends, and click links in WeChat groups. A user's ordinary action may lead to the use of his WeChat permission, resulting in threats such as privacy disclosure and property loss.
The badkernel vulnerability lies in the x5 kernel used by WeChat. The x5 kernel is a chrome browser kernel customized by Tencent, so all applications using the x5 kernel may suffer from this loophole Impact. From the official website of x5 (x5. tencent. com), the Alpha team of 360 Mobile Guard found that the x5 kernel was used in WeChat, mobile QQ, QQ space, JD, 58, Sohu Video, Sina News and other applications.
Among them, since WeChat has become the most commonly used APP for mobile phone users, mobile phone manufacturers are also willing to open authorization to WeChat, and most of the rights management software will not prompt the use of WeChat permissions, so for WeChat users, this vulnerability is very harmful. At present, this vulnerability has been submitted to Tencent Emergency Response Center and provided repair suggestions. Tencent has internally repaired this vulnerability and started to push updates to users.
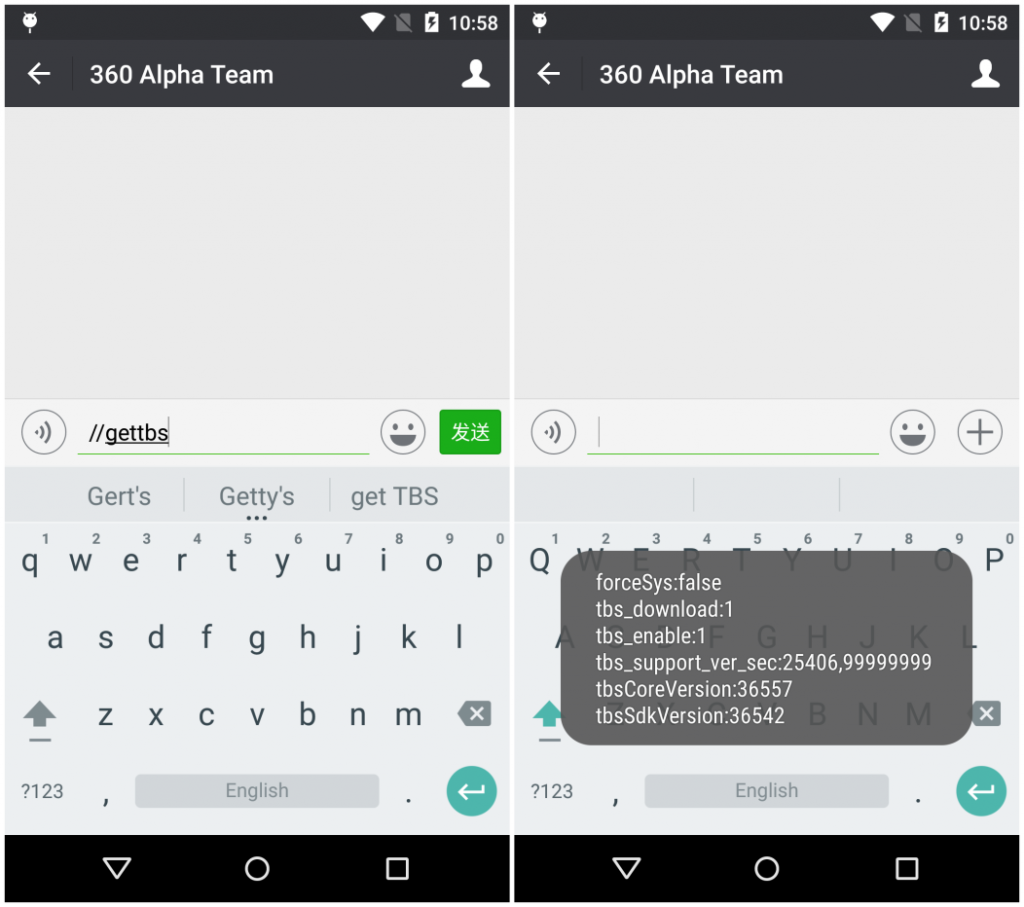
Figure 3: 360 Mobile phone guards provide vulnerability detection methods
Self inspection mode
Users can determine whether they have received an update for this vulnerability by entering "//gettbs" in any chat dialog box. If tbsCoreVersion is greater than 036555, it indicates that the vulnerability has been fixed and the user does not need to worry, otherwise, it indicates that WeChat accepts the loophole influence. Security experts remind users that while waiting patiently for updates, please follow the three don'ts. Don't scan the QR code, click on the links in the circle of friends, or click on the links in the WeChat group at will to prevent WeChat from being controlled remotely.
From FreeBuf.COM
Original article reprint please specify: reprint from Seven Travelers Blog
Fixed link of this article: https://www.qxzxp.com/6449.html


