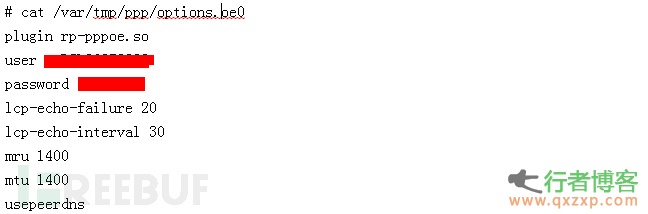As an indispensable network device in the home, home wireless routers bring great convenience to ordinary people, but also bring us many security risks in the Internet era. This article will disassemble the common attack process of common home wireless routers and put forward corresponding defense suggestions, hoping to help everyone.
1、 Stealing wireless password
The most common attack against wireless routers is to steal wireless passwords. The common wireless encryption methods of wireless routers are WEP and WPA/WP2. The wireless passwords of wireless routers can be easily obtained by using different attack methods and some special techniques through the encryption methods configured for wireless routes.
The following figure shows common wireless route encryption methods:

1.1 WEP cracking
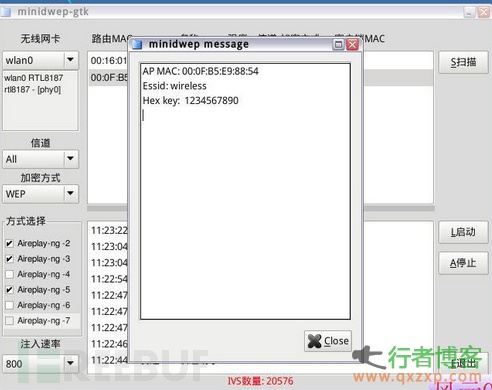
If the wireless encryption mode of your home router is configured as WEP encryption, you have to modify it immediately. Because of the defect of WEP encryption system, the network scrubber can recover the password by collecting enough handshake packets (that is, data packets during the connection authentication between the computer and the wireless router) and using the analysis encryption algorithm. The attack success rate of this encryption method is nearly 100%. A common attack technique is to use MIDIWEP to sniff the surrounding wireless signals. When enough IVS are captured, the wireless password can be automatically solved, as shown in the following figure:
1.2 WPA/WPA2 blast
Another encryption method of the wireless router is WPA/WPA2 encryption. Compared with WEP encryption, there is no way to directly crack the WPA/WPA2 password from some public methods for the time being. Instead, the handshake packet can only be captured first, and then the handshake packet can be violence Cracking , but the combination of some skills and common user password strategy is weak, and the probability of success is also high.
First, use tools such as feedingbottle to sniff and capture packets from the surrounding wireless network. After capturing a complete handshake packet, you can use EWSA to force the saved handshake packet under Windows Cracking According to the data from the previous test, the cracking rate of 550Ti video card is about 13000/s, so the use of pure digital wireless password is the weakest. According to the calculation, the time for a single PC to crack a nine digit pure number is about 999999999/10000/60=27.8 hours
The all-purpose certain treasure has even provided the service of running and holding handbags online. Using the cluster server to run and hold handbags can greatly shorten the time of cracking.
1.3 WPS Cracking
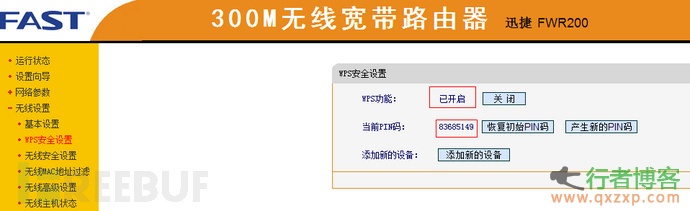
In fact, few people have noticed that the home wireless router has a WPS (QSS or AOSS) function on it, which is enabled by default. The following figure shows the WPS (QSS or AOSS) function interface of some common home routers.
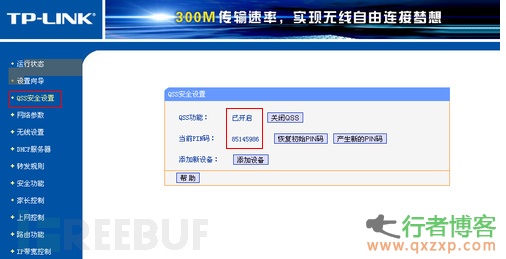
WPS is a certification project organized and implemented by the Wi Fi Alliance, which is mainly committed to simplifying the installation and security performance configuration of WLAN. On a wireless router that supports WPSWPS (QSS or AOSS), users do not need to enter a wireless password, just enter a PIN code or press a button (PBC) to connect securely WLAN 。 But the process of connecting a wireless router with a PIN code can be cracked violently. First, let's talk about the composition of the PIN code, The WPS PIN code is an 8-digit pure number, and the 8th digit is a checksum, which is calculated according to the first 7 digits, The first four digits of the PIN code and the next three digits of the PIN code are verified separately. Therefore, in the process of brute force cracking the PIN code, you only need to try 11000 (10 ^ 4+10 ^ 3) to solve the PIN code, and then use the PIN to connect the router to capture the wireless password.
The tool used for brute force PIN code cracking is reaver or inflator (graphical reaver). The tool can scan the surrounding wireless network and mark the wireless signals that enable the WPS function. After selecting the target of brute force cracking, call the reaver command line to crack. If the router has good performance and good signals, The cracking rate is 2 seconds/pin~~4 seconds/pin, so it can be calculated that the maximum time cost of cracking the wireless password is 9.17 hours (3 * 11000/60/60). The weaker router will crash during the cracking process. At this time, it will have to wait for a period of time to crack after the router's performance is stable. The following figure shows the situation when the cracking is successful:
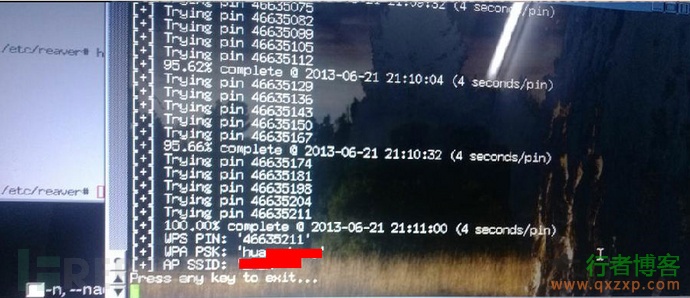
Many router manufacturers have gradually realized the PIN code Cracking Some wireless router manufacturers will add some PIN brute force attack protection, and this prompt will appear when cracking these wireless routers
warning:detected ap rate limiting, xxxxx
However, it is found in practice that most routers will be released after about 60 seconds. At this time, you only need to add the – l 3 parameter to the reactor command. The - l parameter refers to how often the router attempts to crack the router that has limited the PIN attempt. The command defaults to 300. After setting the value to 3, the new cracking will start after about 20 detections for about one minute, Try the PIN code for 10 times, and then wait for about one minute again, and so on. So on this kind of router with some PIN protection, the rate of PIN code cracking is about 11 ([60+5 * 10]/10) seconds/pin. According to the previous formula, the maximum time cost of PIN cracking is 33.6 hours (11 * 11000/60/60). The following figure shows the success of attempting to crack some routers with PIN protection:
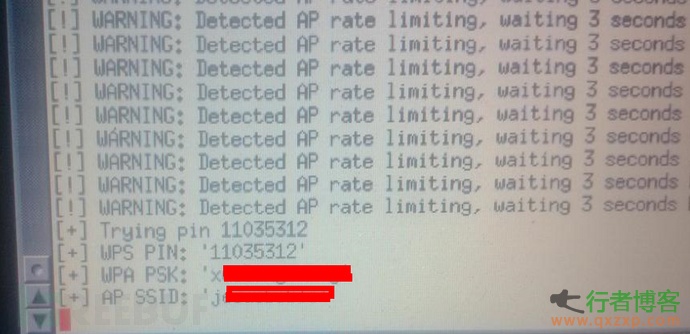
1.4 TELNET back door
A vulnerability platform once disclosed that many routers' public network addresses allow telnet remote login. Because the telnet password is the same as the WEB management password, it is easy to successfully access the wireless router through the (admin: admin) telnet router's public network address, and then execute the wlctlshow command to obtain the wireless router's wireless password, This problem exists in some batches of household wireless routers of common brands.

Some routers integrated with busybox also have telnet enabled by default for public network addresses. After logging in, you can not only see the wireless password, The PPPOE password can also be easily obtained:
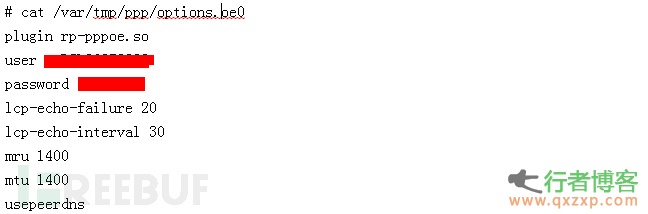
The author once wrote a special script to try to log in to the telnet service of the public network address using only the username and password combination of admin: admin. After successful login, only one wlctl show command was executed and the echo information was extracted, By scanning some public address network segments, it is found that there are a large number of home routers on the public network with telnet enabled and admin: admin as the default password. The following figure shows some wireless passwords extracted during batch scanning of the tool:
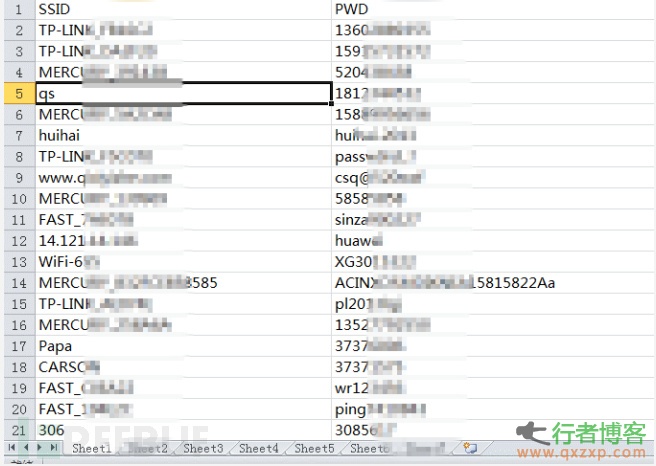
1.5 APP Share leaked password
Similar to some mobile apps of the WIFI auxiliary class, it is also a way to disclose wireless passwords. For example, the default configuration of some APPs is to share the wireless password in the phone, so all wireless passwords connected to the phone will be shared by default, including home wireless routers or friends' wireless routers, so if you or connect you WIFI % of friends' mobile phones have installed such APP, which is likely to cause the leakage of family wireless passwords. After installing such APP, the author often tries to search the passwords of surrounding wireless signals, often with gains.
By default, The APP will not tell you the password of successful connection, but since the system will automatically save the WIFI password of successful connection, the Android phone after root can read it by browsing the configuration file WIFI Password, the method is as follows: http://jingyan.baidu.com/article/91f5db1bea61d51c7e05e36e.html
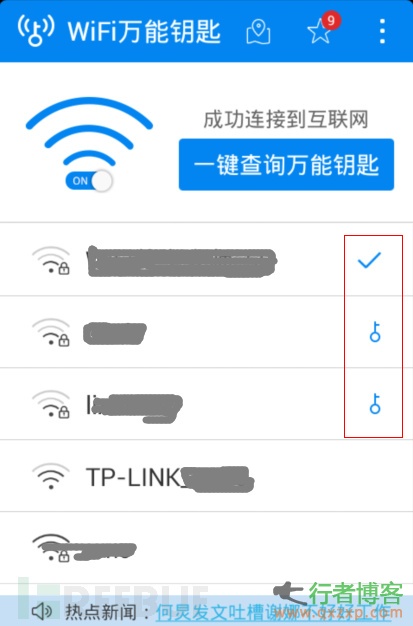
2、 Hazards after theft
2.1 Man in the middle attack
When the wireless password is obtained, hacker Then he got the access to the WLAN. The next common attack method is to sniff the middle man, poison it through ARP, and combine it with CAIN Wireshark, ssltrip, dsploit and other tools can sniff the sensitive information of LAN hosts.
CAI: When used in combination with wireshark, it can not only sniff the wireless password, but also capture other traffic information of users in the LAN, such as information transmitted by clear text protocols such as Internet records.
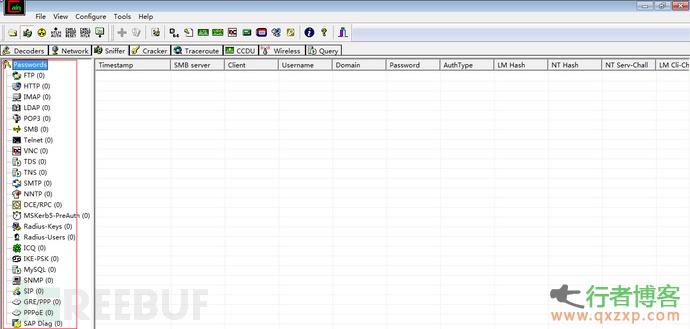
SSLSTRIP: a tool released by Moxie Marlinspike at the Black Hat Conference. It can break through ssl encrypted protocols (such as https), carry out man in the middle attacks with ARP poisoning, and implement man in the middle sniffing of HTTPS and other protocols.
The following figure shows the principle of SSLSTRIP sniffing online banking:
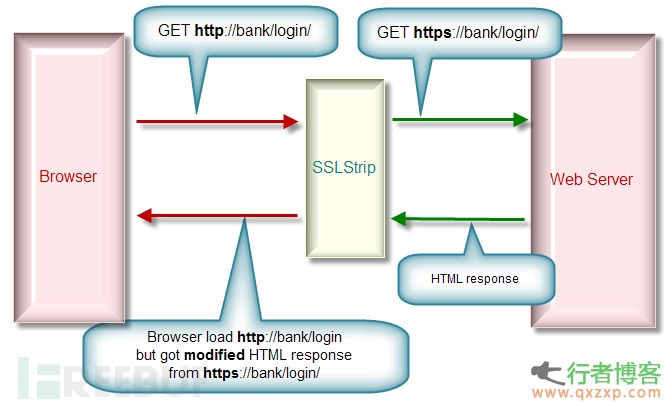
Dsploit: It is a network analysis and penetration suite under Android. The tools related to man in the middle attack include multiple protocol password sniffing HTTP/HTTPS session hijacking, picture replacement, etc. This tool is short and simple, and one mobile phone can pose a huge threat to the LAN.
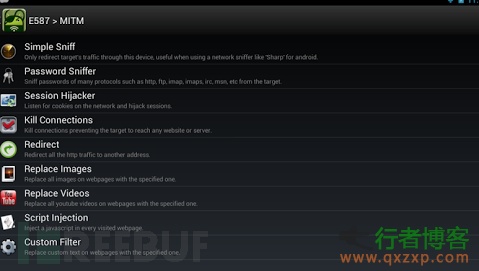
2.2 Stealing PPPOE password
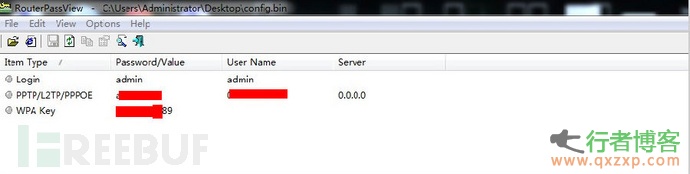
Get the wireless password through the above steps. By sniffing or weak password guessing, you can easily log in to the home router to make some configuration changes and view. For example, download the router configuration file and use a routerpassview software to view the PPPOE password. You can also directly change the DNS configuration for phishing and man in the middle attacks at the DNS level.
3、 Some safety suggestions
After getting familiar with the above attack methods against home wireless routers, let's talk about defense:
1. The encryption mode of home wireless router should be WPA/WPA2. It is recommended to use a complex password with more than 8 digits and mixed uppercase and lowercase letters, special symbols and numbers for wireless passwords;
2. Modify the default management password of the home wireless router;
3. Turn off the WPS (QSS or AOSS) function of home wireless routing;
4. Add additional router security policies, such as limiting access to specific MAC addresses, and temporarily manually adding MAC addresses when friends visit;
5. Turn off the automatic hotspot sharing function when using some wireless APP to prevent the disclosure of your home wireless password;
6. Log in to the router frequently to check the wireless connection status and DHCP client list
The copyright of this article belongs to the NSTRT team. If you think this article is useful, you can share it with your friends. Also, we hope that more people will also pay attention to our WeChat official account trt917. We will regularly share some information security related knowledge, hoping it can be helpful to everyone.
[This article is written by the NSTRT team, FreeBuf.COM exclusively publishes articles, reprinting without permission is prohibited]
Original article reprint please specify: reprint from Seven Travelers Blog
Fixed link of this article: https://www.qxzxp.com/5783.html