1、 Misc
1. Title: What is that?
answer:
(1) After opening the title, a gesture is found, as shown in the following figure:
(2) Open the winHex tool and look for 00000 27200001F4, as shown in the following figure;
(3) Change to 00000 27200002F4, as shown in the figure below;
(4) Save and open the picture to see the flag, as shown in the following figure;
(5) Flag: Flag={Welcome_To_ISCC_2018};
(6) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1ut_w9nQRqCbmJGUqIk_9Og
Password: svyb
2. Title: Secret Telegram
answer:
(1) Open the title and find: ABAAABABBABABAAABABABAAAAAAABABABABABAABAABABAAAAAA encrypted string character, as shown in the following figure;
(2) The observation is Bacon code, and according to the nature of Bacon code, it is shown in the figure below;
(3) Use online tools to decrypt as shown in the figure below;
Decryption URL link: http://tool.bugku.com/peigen/
(4) Results: ILIKEISCC, ilikeiscc
(5) Flag:ILIKEISCC
(6) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/1QVTLEruYe-s4BqohhUya5A
Password: kank
3. Title: Where is the FLAG?
answer:
(1) Open the title and find a png image, as shown in the following figure;
(2) Use Adobe Fireworks CS5 tool to open this picture, as shown in the following figure;
(3) Move the logo of ISCC to see the QR code, as shown in the following figure;
(4) N QR codes are found, as shown in the figure below;
(5) These two-dimensional codes are spliced into a two-dimensional code, as shown in the following figure;
(6) Scanned flag, as shown in the figure below;
(7) Flag:a332b700-3621-11e7-a53b-6807154a58cf
(8) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1H7UQ7kRkX6DslTNF_1-pTA
Password: 5dgt
4. Topic: A cat's mind
answer:
(1) Open the title and find it is a game cat, as shown in the following figure;
(2) Use winHex to view and open, as shown in the following figure;
(3) It is found that there is a WPS version of word document in the picture, as shown in the following figure;
(4) Perform manual separation, and report error doc version, as shown in the following figure;
Note: Hex file header value of WPS version: D0CF11E0A1B11AE1
(5) Open the extracted word document, as shown in the following figure;
(6) Use Buddhism and Zen to decrypt, as shown in the figure below;
Decryption URL link: http://www.keyfc.net/bbs/tools/tudoucode.aspx
(7) Click to comprehend the true meaning of Buddha's words, and decrypt it as shown in the following figure;
(8) Copy the decryption result to the left of winHex;
(9) Base64 decrypt the right content;
Decryption URL link: http://base64.xpcha.com/
(10) The decryption result is decrypted by base32;
Decryption URL link: http://www.qqxiuzi.cn/bianma/base.php
(11) Copy the base32 decryption result to the left of winHex, as shown in the following figure;
(12) The base64 obtained in winHex is decrypted, as shown in the following figure;
(13) The decryption result is decrypted by base32, as shown in the figure below;
(14) Copy the decryption result to the left of winHex, as shown in the figure below;
(15) Flag:F1a9_is_I5cc_ZOl8_G3TP01NT
(16) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1fi_DoySdBLQUUrj0ZSo80w
Password: yvp7
5. Title: Violence is not advisable
answer:
(1) Open the title and find an encrypted zip package, as shown in the following figure;
There are two solutions. Let's look at method one first
(1) Copy it to linux kali and decompress it with the binwalk - e command, as shown in the following figure;
(2) Access the uncompressed folder, as shown in the following figure;
(3) Use the command cat flag.txt to view the content of the txt file, as shown in the following figure;
Vfppjrnerpbzvat
Method 2
(1) Open the compressed package in winHex, as shown in the following figure;
(2) Find 504B030414000008 and 4B01023F00140007, as shown below;
(3) Modify to 504B030414000000 and 4B01023F00140000, as shown in the following figure;
(4) Save and decompress, as shown in the following figure;
(5) Open the flag.txt text file after the file, as shown in the following figure;
(6) Open the flag.txt file, as shown in the following figure;
Vfppjrnerpbzvat
(7) ROT13 for decryption
Decryption URL link: http://www.mxcz.net/tools/rot13.aspx
(8) Flag:isccwearecoming
(9) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1Yv9BX4QMFlqGftZjareWbw
Password: 37c3
6. Title: Many spies
answer:
(1) After downloading the title, it is found that there is a large section of base64 encryption, as shown in the following figure;
(2) Perform base64 decryption, as shown in the figure below;
Decryption URL link: http://www.qqxiuzi.cn/bianma/base64.htm
(3) It is found that the decryption result is still base64, so continue decryption, as shown in the following figure;
Decryption URL link: http://www.qqxiuzi.cn/bianma/base64.htm
(4) It is found that the decryption result is still base64, so continue decryption, as shown in the following figure;
Decryption URL link: http://www.qqxiuzi.cn/bianma/base64.htm
(5) At the fourth layer, it is found that the URL ciphertext is decrypted, as shown in the following figure;
Decryption URL link: http://www.convertstring.com/zh_CN/EncodeDecode/UrlDecode
(6) The decryption result is base64, so continue decryption, as shown in the following figure;
Decryption URL link: http://www.qqxiuzi.cn/bianma/base64.htm
(7) At the sixth layer, it is found that the URL ciphertext is decrypted, as shown in the following figure;
Decryption URL link: http://www.convertstring.com/zh_CN/EncodeDecode/UrlDecode
(8) The decryption result is base64, so continue decryption, as shown in the following figure;
Decryption URL link: http://www.qqxiuzi.cn/bianma/base64.htm
(9) At the eighth layer, it is found that the URL ciphertext is decrypted, as shown in the following figure;
Decryption URL link: http://www.convertstring.com/zh_CN/EncodeDecode/UrlDecode
(10) The decryption result is base64, so continue decryption, as shown in the following figure;
Decryption URL link: http://www.qqxiuzi.cn/bianma/base64.htm
(11) The decryption result is base64, so continue decryption, as shown in the following figure;
Decryption URL link: http://www.qqxiuzi.cn/bianma/base64.htm
(12) The decryption result is base64, so continue decryption, as shown in the following figure;
Decryption URL link: http://www.qqxiuzi.cn/bianma/base64.htm
(13) At the twelfth layer, it is found that the URL ciphertext is decrypted, as shown in the following figure;
Decryption URL link: http://www.convertstring.com/zh_CN/EncodeDecode/UrlDecode
(14) At the 13th layer, it is found that the consequence of decryption is AES, so decryption is required, as shown in the following figure;
Decryption URL link: https://www.sojson.com/encrypt_aes.html
(15) The result of the 14th layer decryption is the decryption of the Buddhist Zen encryption, as shown in the following figure;
Decryption URL link: http://www.keyfc.net/bbs/tools/tudoucode.aspx
(16) Flag: Copy me away
(17) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1ygIKTa3AVnPhzbUheWbiog
Password: afwk
7. Title: Caesar XIII
answer:
(1) Observe the title. The title indicates Caesar in the first clause, as shown below;
(2) So try Caesar (rot13) shift to decrypt, as shown in the following figure;
Decryption URL link: http://www.mxcz.net/tools/rot13.aspx
(3) The second clause of the title description is the keyboard, as shown in the figure below;
(4) Move one position up or down on the keyboard according to the decrypted content, as shown in the following figure;
A Add a small knowledge point, as shown in the figure below;
B returns to the body, as shown in the figure below (the flag is obtained according to the decrypted ciphertext sequence);
(5) Flag:yougotme
(6) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1yOy0OPs4PiOxyIHST6JhQg
Password: 53pq
8. Title: Interesting ISCC
answer:
(1) Download the title and unzip it, as shown in the following figure;
(2) It is found that it is a jpg image and put it into winHex to view, as shown in the following figure;
(3) It is found that the image is the head of the png image, as shown in the following figure;
(4) At the end of the picture, you can see that there is a Unicode code behind the IEND, as shown in the following figure;
(5) Decrypt the Unicode code (click to convert the Unicode code to Chinese), as shown in the following figure;
Decryption URL link: http://tool.chinaz.com/tools/unicode.aspx
(6) After decryption, it is found that there is a hexadecimal code, so continue decryption (click hexadecimal to character). As shown in the figure below;
Decryption URL link: https://www.bejson.com/convert/ox2str/
(7) Flag:flag{iscc is fun}
(8) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/1Uwat1hXovCRmZHhg8Fw1bg
Password: w9ui
9. Title: Digital ciphertext
answer:
(1) As shown in the title, hexadecimal is converted into characters, as shown in the following figure;
Decryption URL link: https://www.bejson.com/convert/ox2str/
(2) Flag:it’s easy!
(3) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/13IuYVJx_HtYg7zr4QUtV6g
Password: vhex
10. Title: Treasure Digging Plan
answer:
(1) After downloading the title, it is found that it is a compressed package, as shown in the following figure;
(2) Attempt to decompress and find the password. As shown in the figure below;
(3) ZIP compressed packets are not pseudo encrypted when detected in winHex. As shown in the figure below;
(4) Use clear text to hit the password, as shown in the figure below;
(5) The password of the compressed package is (ISCCzxc), as shown in the following figure;
(6) After decompressing the compressed package, I found that the title was the same as last year. I don't know what the organizer wants to do with this question;
(7) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/1ZjmkZuuksJfpwPJrqaHsZg
Password: bkpa
11. Title: Nested ZIPs
answer:
(1) After downloading the title, it is found that it is a compressed package, as shown in the following figure;
(2) The password is found after decompressing the compressed package, as shown in the following figure;
(3) First, mask explosion of digital type is carried out, as shown in the following figure;
(4) Get the first layer password and decompress it, as shown in the following figure;
(5) Look at the extracted tips.txt file, as shown in the following figure;
(6) According to the content, it is estimated that the attack is a plaintext attack, as shown in the following figure;
(7) Use ARCHPR to attack plaintext, as shown in the figure below;
(8) Get the decompression password: Z! C @ t # f $12 and extract the file, as shown in the following figure;
(9) Put the third layer of compressed package into winHex, as shown in the figure below;
(10) Pseudo encryption is found, as shown in the figure below;
(11) Change 14000008 to 14000000, as shown in the figure below;
(12) Save and decompress, as shown in the following figure;
(13) After decompression, open flag.txt, as shown in the following figure;
(14) Flag : ISCC_! S_my_favor1te_CTF
(15) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/1XY_QvoK9vaAQcZXNI0QrRQ
Password: ipbt
�0�2
2、 Web
1. Title: Comparing the size of numbers
answer:
(1) There is only one submission dialog box on the website page, as shown in the following figure;
(2) Open the approval element, as shown in the following figure;
(3) Modify the maxlength of the audit element="3", as shown in the following figure;
(4) Change maxlength="3" to maxlength="4", as shown in the following figure;
(5) Input 9999 in the dialog box, as shown in the figure below;
(6) Click Submit, as shown in the figure below;
(7) Flag:key is 768HKyu678567&*&K
2. Topic: Can you cross over?
answer:
(1) Open the web address, as shown in the figure below;
(2) Base64 is found in the web page link, as shown in the following figure;
ADwAcwBjAHIAaQBwAHQAPgBhAGwAZQByAHQAKAAiAGsAZQB5ADoALwAlAG4AcwBmAG8AYwB1AHMAWABTAFMAdABlAHMAdAAlAC8AIgApADwALwBzAGMAcgBpAHAAdAA
(3) Decrypt base64 in the web page link, as shown in the following figure;
Decryption URL link: http://base64.xpcha.com/
(4) Reorganize the decrypted results, as shown in the figure below;
(5) Copy/% nsfocusXSStest%/to the dialog box, as shown in the following figure;
(6) Click Submit to pop up a dialog box, as shown in the following figure;
(7) Flag:flag{Hell0World}
3. Title: Everything is a routine
answer:
(1) Open the link, as shown in the following figure;
(2) Use the scanner to scan, as shown in the figure below;
http://118.190.152.202:8009/index.php.txt
(3) Open the link of scanning results, as shown in the following figure;
(4) Open the HackBar of Fox Fire browser, as shown in the following figure;
(5) Click LoadURL to copy the URL to the dialog box, as shown in the following figure;
(6) Click Post data, as shown in the figure below;
(7) Add? After the web address index.php in the LoadURL? _200=flag, As shown in the figure below;
(8) Enter flag=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa in Post data, as shown in the following figure;
(9) Click Execute to access the webpage, as shown in the figure below;
(10) Flag:ISCC{taolu2333333….}
4. Topic: Can you bypass it?
answer:
(1) Open the link, as shown in the following figure;
(2) Click one randomly, as shown in the figure below;
(3) Change id=2 to 6668952, as shown in the following figure;
(4) There is no filtering after the ID is found, so try to read the file containing the flag, as shown in the following figure;
(5) The discovery page displays base64 and decrypts it, as shown below;
Decryption URL link: http://base64.xpcha.com/
(6) It is found that the decryption result is html static page source code, as shown below;
(7) Flag:ISCC{LFIOOOOOOOOOOOOOO}
(8) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1_5OWy8TCFKbq6vIz-wPhPA
Password: id8e
5. Title: web02
answer:
(1) Open the link, as shown in the following figure;
(2) There is a local link in the text of the title link, so the http request header is modified by capturing packets, as shown in the following figure;
Client-IP:127.0.0.1
(3) Click Intercept is on to place the package, as shown in the figure below;
(4) View the webpage, as shown in the following figure;
(5)Flag:ISCC{iscc_059eeb8c0c33eb62}
6. Title: The Art of SQL Injection
answer:
(1) Open the link, as shown in the following figure;
(2) Click personal information, as shown in the figure below;
(3) Put the link into sqlmap and try to inject it, as shown in the following figure;
Command:
sqlmap –u http://118.190.152.202:8015/index.php?id=1
(4) It is found that it is wide character injection and WAF is prompted, so try to bypass WAF, as shown in the following figure;
Command:
sqlmap -u “ http://118.190.152.202:8015/index.php?id=1 “ —tamper unmagicquotes.py —batch -v 3 —level 3 –dump
(5) Flag:Y0u_@@33w_dxxmn_9rf0Od
7. Title: Try
answer:
(1) Open the link, as shown in the following figure;
(2) In the place where img=, test whether there are files containing vulnerabilities, as shown below;
(3) Files containing vulnerabilities are found, as shown in the figure;
A. payload, As shown below;
B. It is proved that the existing file contains vulnerabilities, as shown in the figure below;
(4) Construct payload, as shown below;
(5) The page is blank, as shown below;
(6) Open the web page source code, as shown below;
(7)Flag:flag{1ntere5ting_PHP_Regu1ar_express1onssssss}
(8) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1hpljgBPsE-V6VWz0YB91_A
Password: m5x3
8. Topic: Local Temptation
answer:
(1) They all said it was a sign in question, so they opened the link. As shown in the figure below;
(2) View the source code, as shown in the figure below;
(3) Flag:ISCC{^&*(UIHKJjkadshf}
9. Topic: Please ping my IP address to see if you can ping it?
answer:
(1) Open the link, as shown in the following figure;
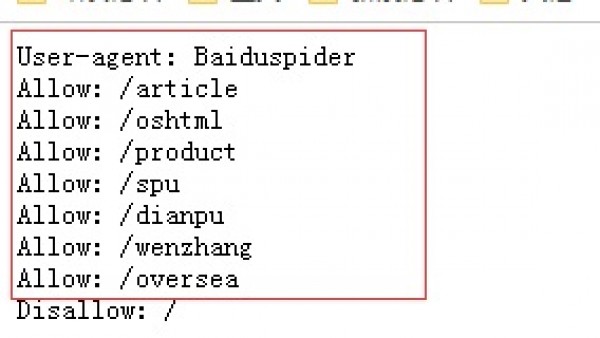
(2) Use the scanner to scan the directory. As shown in the figure below;
Scan results: http://118.190.152.202:8018/flag.txt
(3) Open the scanning results, as shown in the following figure;
(4) Flag:ISCC{8a8646c7a2fce16b166fbc68ca65f9e4}
10. Title: Please give me username and password!
answer:
(1) Open the question link, as shown in the following figure;
(2) The link page prompts the user name and password, as shown in the following figure;
(3) So construct payload for user password access, as shown in the figure below;
Payload:/? username[]&password=3e9
(4) Flag:flag{ISCC2018_Very_GOOD!}
11. Title: web01
answer:
(1) Open the link and find it is a code audit question, as shown in the following figure;
(2) The GET type submitted the password, and the requirements for obtaining the flag are:
A. password=0
B. sha(password)=0
(3) It seems that the final result of the password is equal to 0, and if the condition is true, the flag will be obtained. The construction statement is shown in the figure below;
(4) Flag:ISCC{iscc_ef3w5r5tw_5rg5y6s3t3}
12. Title: Collide
answer:
(1) Open the link and find that it is a code audit topic, as shown in the following figure;
(2) After auditing the source code, use HashPump to attack;
(3) Install HashPump;
A. Method 1:
git clone https://github.com/bwall/HashPump.git
apt-get install g++ libssl-dev
cd HashPump
make
make install
B. Method 2:
pip install hashpumpy
(4) Run HashPump and replace x with%, then use hacbar urldecode, as shown in the following figure;
(5) Run hackbar, as shown in the figure below;
(6) Modify the md5 value with burp packet truncation, as shown in the following figure;
(7) Flag:ISCC{MD5_1s_n0t_5afe}
13. Title: Only admin can see flag
answer:
(1) Open the question link and find that there is only one login dialog box. As shown in the figure below;
(2) View the source code and find an index.txt prompt, as shown in the following figure;
(3) Open index.txt, audit the source code, and find that it is a CBC inversion vulnerability, as shown in the following figure;
(4) The following describes the principle of CBC byte flipping attack, as shown in the figure below;
(5) As shown in the figure above, the schematic diagram of CBC encryption;
A. Plaintext: data to be encrypted.
B. IV: A bit block used for randomized encryption to ensure that different ciphertext can be obtained even if the same plaintext is encrypted multiple times.
C. Ciphertext: encrypted data.
D. The important point here is that CBC works in a fixed length bit group, which is called block. In this article, we will use a 16 byte block.
(6) The whole encryption process is simple;
A. First, group the plaintext (usually 16 bytes). If the number of bits is insufficient, use special characters to fill in.
B. Generate a random initialization vector (IV) and a key.
C. XOR IV with the first set of explicit text.
D. Encrypt the ciphertext generated after xor in C with the key.
E. Xor the second group of plaintext with the ciphertext generated in D.
F. Encrypt the ciphertext generated in E with the key.
G. Repeat E-G to the last set of plaintext.
H. The IV and the encrypted ciphertext are spliced together to get the final ciphertext.
Starting from the first block, first XOR an initial vector iv (iv only works at the first place), then encrypt the result of the XOR with the key to get the ciphertext of the first block, and XOR the encrypted result with the plaintext of the next block, and continue this process. Therefore, the most important characteristics of this model are:
(7) The ciphertext of the previous block is used to generate the ciphertext of the next block, as shown in the following figure;
(8) This is the decryption process. As long as the encryption is understood, the decryption process is also very simple. Similarly, the previous ciphertext participates in the restoration of the next ciphertext.
A. Extract IV from ciphertext, and then group ciphertext.
B. Use the key to decrypt the first group of ciphertext, and then xor with IV to get the plaintext.
C. Use the key to decrypt the second set of ciphertext, and then get the plaintext with the ciphertext xor in 2.
D. Repeat B-C until the last set of ciphertext.
(9) This is the schematic diagram of our flip attack:
It can be noted that the previous Ciphertext is used to generate the next block of plaintext. If we change a byte in the previous Ciphertext and then xor the decrypted ciphertext of the next block, we can get a different plaintext, which we can control. Using this, we can cheat the server or bypass the filter.
(10) Enter an account and password randomly in the login dialog box and use bp to capture packets, as shown in the following figure;
(11) View the returned package, as shown in the following figure;
(12) Use the script to reverse, as shown in the following figure;
(13) Set iv and flipped cipher in the cookie in bp and submit after clearing the post value, as shown in the following figure;
(14) The returned results are shown in the following figure;
(15) The server prompts that the deserialization failed, but in fact, as long as we decode this in base64 at this time, we will find that our username has become admin; The reason is that when we change the mdmin to admin, we modify the first block of data, so the first block of data is destroyed. Because the program requires username to be equal to admin, the padding characters mentioned in the article cannot be used. Also, because the first block data is damaged, and the first block data is related to IV, as long as the CBC character flip attack is performed, and a new IV is obtained, the first block data can be repaired. As shown in the figure below;
(16) Replace the obtained value with iv, cipher does not move, and then submit. As shown in the figure below;
(17) Flag:ISCC{123dasd89as10aas}
(18) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/1mr6NTo2sAkdH90hcFRHW8g
Password: 1kny
14. Title: PHP is the best language in the world
answer:
(1) Open the link and find that it is code audit, as shown in the following figure;
(2) Scan with the scanner and find the no_md5.php file. As shown in the figure below;
(3) The source code given by the audit topic is found to be contained in the file. As shown in the figure below;
(4) So construct the statement in this way, as shown in the following figure:
/no_md5.php? a=GLOBALS
(5) Flag:ISCC{a39f9a1ff7eb4bab8a6a21b2ce111b4}
15. Title: Only Admin
answer:
(1) Open the link to find a login dialog box, as shown in the following figure
(2) Scan with the scanner and find the backup file. As shown in the figure below;
http://118.190.152.202:8020/web.zip
(3) Extract the backup file, as shown in the following figure;
(4) Open config.php and find the code to be audited, as shown in the following figure;
(5) Enter 'or 1 # in the email of the login dialog box and enter the password at will, as shown in the following figure;
(6) Click login, as shown in the figure below;
(7) Run the script and write it into the cookie, as shown in the following figure;
(8) After the script runs, a new item will be added to the cookie, as shown in the following figure;
(9) Open the approval element, as shown in the following figure;
(10) Flag:flag{USer1ali2e1sInt4rt1n9}
(11) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/1btTm5HfZOJkmS7OMgbVGxQ
Password: 6cyp
16. Title: Why is it so simple
answer:
(1) Open the link and find that it is a challenge, as shown in the following figure;
(2) See these two elements, as shown in the figure below;
(3) This is similar to the web topic in DDCTF 2018. Use BurpSuite to capture packets and modify HTTP headers, as shown in the following figure;
(4) Click GO, and the returned results are as shown in the figure below;
(5) Get the second customs address and find that you need to enter a password to get the flag, as shown in the following figure;
(6) Right click to view the web page source code, as shown in the following figure;
(7) Click in the source code /password.js, As shown in the figure below;
(8) A piece of base64 code is found, as shown in the following figure;
(9) Perform base64 decryption, as shown in the figure below;
Decryption URL link: http://base64.xpcha.com/
(10) The result of decryption is an XSS statement and the password for obtaining the flag is found, as shown in the following figure;
password:xinyiji.com
(11) Enter the password and click to get the flag, as shown in the figure below;
(12)Flag:B1H3n5u0xI2n9JIscc
(13) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/11SPmCZ8h7Xov –P-jknpEA
Password: 7vef
17. Title: Sqli
answer:
(1) Open the link to find a login dialog box, as shown in the following figure;
(2) Use BurpSuite to capture packets, as shown in the following figure;
(3) In the login dialog box, enter - 1'OR (1=1 *) or 'for username and x for password, as shown in the following figure;
(4) Save the packet capture content as TXT, as shown in the figure below;
(5) Use sqlmap injection, as shown in the figure below;
A. Inject command statements, as shown in the figure below;
B. Injection results are shown in the figure below;
(6) Flag:flag{hahaha999999999}
(7) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/1TUw4fcYsbH7-sJ9IAPhSxw
Password: tn7y
18. Title
answer:
(1) Open the link to find a login dialog box, as shown in the following figure;
(2) Use BurpSuite to capture packets and try to log in, as shown in the following figure;
C
(3) The returned result shows that the user name is admin, as shown in the following figure;
(4) Use BurpSuite to capture packets and inject them, as shown in the following figure;
(5) The returned results are shown in the following figure:
(6) Use the script to run the password, as shown in the following figure;
(7) The password obtained is: nishishabi1438
(8) Log in with the account password, as shown in the figure below;
(9) Enter flag to get the flag, as shown in the following figure;
(10) Flag:flag{sql_iNjEct_Is_Easy}
(11) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/1E7PuabjjP4ovxw1H0KANtg
Password: 5vsi
�0�2
3、 Reverse
1. Title: RSA256
answer:
(1) Download the title, as shown in the figure below;
(2) Decompress, as shown in the figure below;
(3) To put it bluntly, did the author misunderstand the password? Re place an RSA password, as shown in the figure below;
(4) First, you can see the public key file public.key, without thinking about it, and directly throw it to Kali. Use openssl to solve e and n, as shown below;
Command: openssl rsa - pubin - text - module - in warmup - in public.key
(5) E is 65537, and n is relatively short. First convert it to decimal system, as shown below;
(6) Factorize n, as shown below;
Decryption URL: http://factordb.com/
(7) P and q can be easily solved, as shown below;
(8) Here, RSA parameters are complete, as shown below;
(9) Use python3 code to decrypt ciphertext, as shown below;
(10) Run the program to get the answer, as shown below;
(11) Flag:flag{3b6d3806-4b2b-11e7-95a0-000c29d7e93d}
(12) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1ewjLGoTQN685ly1Q2nY09Q
Password: px37
2. Title: My math is bad
answer:
(1) The download title is found to be an elf attribute file, as shown in the following figure;
(2) Throw it into IDA, as shown in the figure below;
(3) Press F5, as shown in the figure below;
(4) Is to solve two equation groups, and use python z3 to solve them. As shown in the figure below;
(5)Flag: flag{th3_Line@r_4lgebra_1s_d1fficult !}
(6) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1fdFgCYlrQVW-lwTRxAZLZw
Password: hfbv
3. Title: obfuscation and encoding
�0�2
answer:
(1) Download the title to get the ELF file, as shown in the figure below;
(2) Open it with ida, as shown in the following figure;
(3) This question is verified by comparing strings with two-layer encryption;
(4) The two-layer encryption is confused through while. In fact, the two-layer loop can be regarded as if else;
(5) The second layer is to find a base64 script on the base64 network that has changed the character table to decode it, as shown in the following figure;
(6) The first floor needs blasting, and the script is shown in the following figure;
(7) The script running results are shown in the following figure;
(8) Flag:flag{dO_y0U_KNoW_0IlVm?}
(9) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/12Pv9G89pzZAlwVTlpSkE5g
Password: 3r36
4. Title: leftleftright
answer:
(1) Download the title to get the exe file, as shown in the figure below
(2) Put the downloaded file into IDA, as shown in the figure below;
(3) A very simple reverse question moves left and right according to the topic prompts
(4) If there is a shell outside, just find a sheller to remove the shell
(5) Open IDA and observe that the input length needs to be 29
(6) Directly input 29 length non duplicate data in windbg, as shown in the following figure;
(7) The replacement rule of character position can be observed
(8) Compare the target string in IDA, as shown in the following figure;
(9) The script replaces the corresponding program, as shown in the figure below;
(10) The operation results are shown in the figure below;
(11) Flag:Flag{this_was_simple_isnt_it}
(12) Title Download Baidu Cloud Disk Link:
Link: https://pan.baidu.com/s/15HC3pH81JdxJWnXM6tKCCA
Password: x8bi
IV PWN
1. Title: Login
answer:
(1) Download the title, as shown below;
(2) Throw the program into IDA, as shown below;
(3) It is found that there is a login function that requires login to enter the menu function, as shown below;
(4) The account password program has been given, as shown below;
(5) Enter the menu function, analyze and learn that there is stack overflow when entering options, and the return address can be overwritten, as shown below;
(6) Then return to the puts function to puts@got as well as read@got The address is leaked. Then find out the libc on the server through libcdatabase, calculate the address of system and binsh, and finally execute system ('/bin/sh') if the stack overflows
(7) Script, as shown in the following figure;
(8) Flag:flag{welcome_to_iscc}
(9) Download Baidu online disk link;
Link: https://pan.baidu.com/s/10EG4ubVKQIQytjvzst6VuQ
Password: rqdy
2. Title: Write some paper
answer:
(1) Download the title, as shown below;
(2) Throw the questions into IDA, as shown in the figure below;
(3) It is found that it is the practice of hos. First, use get_num to disclose the stack address. As shown in the figure below;
(4) Then use the secret option to construct fake_chunk on the stack, as shown in the following figure;
(5) Finally, use uaf and fastbin stack to return stack memory, and overwrite the return address of the secret function with that of the gg function, as shown in the following figure;
(6) Finally, exit the secret function;
(7) The script is shown in the following figure;
(8) The operation results are shown in the figure below;
(9) Flag:flag{ISCC_SoEasy}
(10) Download Baidu online disk link;
Link: https://pan.baidu.com/s/1hxDG1o7XvBz6u6DQfoq7qA
Password: ge1i
2. Title: Happy Hotel
answer:
(1) Download the title, as shown below;
(2) Use IDA to open the program, as shown in the figure below;
(3) If the program is not related to NX, we can find a way to construct the shellcode
(4) In the game function, we can enter the shell code and disclose the stack address, as shown in the following figure;
(5) In the next sub_400A29 function (as shown in the figure below), the dest pointer can be overwritten by buf. In the previous step, we arranged the shellcde in the stack and disclosed the stack address, so we can overwrite the dest pointer with the got address of a function (I choose free@got )In the following strcpy, we can overwrite the got address with the previous shellcode address, so that we can execute the shellcode and get the shell in subsequent function calls
(6) The script is shown in the following figure:
(7) The flag obtained by running the script is shown in the figure below;
(8) Flag:flag{wish_you_have_a_good_day}
(9) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/10Yp9pAWzYPfe473hm8phVg
Password: 8yhi
�0�2
V Mobile
1. Title: Small test
answer:
(1) Download the title, as shown below;
(2) Use the jadX_apk decompile tool to decompile, as shown in the following figure;
(3) Find bfsprotect.jar in the assets folder, as shown in the following figure;
(4) Modify the jar of bfsprotect.jar to dex, as shown in the following figure;
(5) Use the Android reverse assistant tool to decompile to dex2jar.jar, as shown in the following figure;
(6) Use jd gui to view the decompiled dex2jar.jar, as shown in the following figure;
(7) Open org.isclab.shh.protectapp, as shown in the following figure;
(8) Open the protectClass file to find the flag, as shown in the following figure;
(9) Flag:BFS-ISCC
(10) Title Download Baidu Online Disk Link:
Link: https://pan.baidu.com/s/1F0DjPqp2wRNjNr-7CSQK5A
Password: k3vg