diary
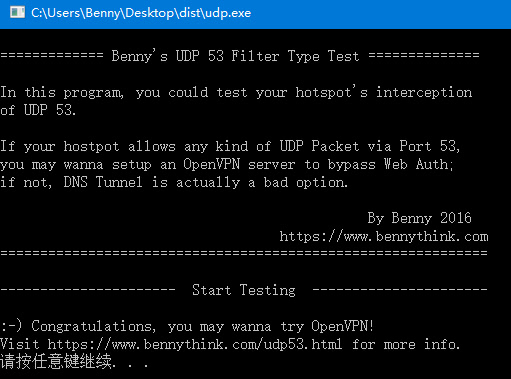
At the same time, the pagoda environment is equipped with the ss plug-in (which can bypass the Web authentication to access the Internet for free udp53
I Principle Introduction
II Environmental detection
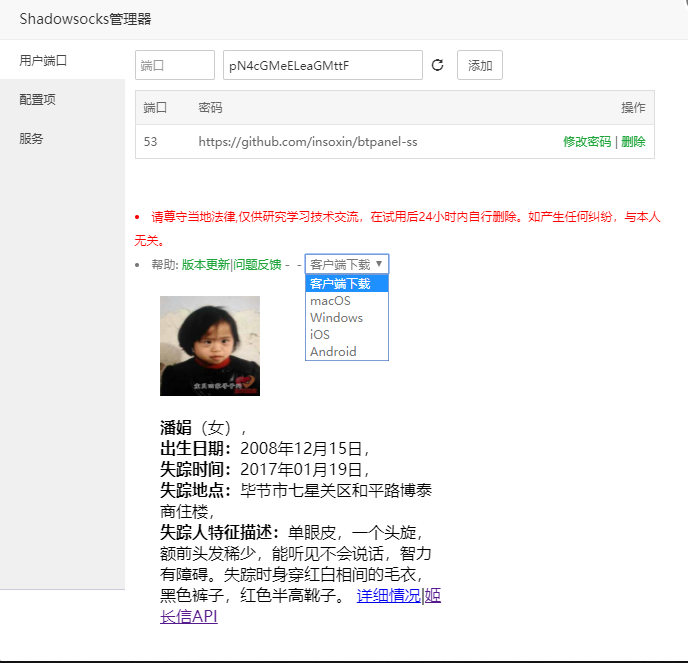
III Installation of pagoda ss plug-in
-
git clone https: //github.com/insoxin/btpanel-ss/ -
cd btpanel-ss -
bash install.sh install
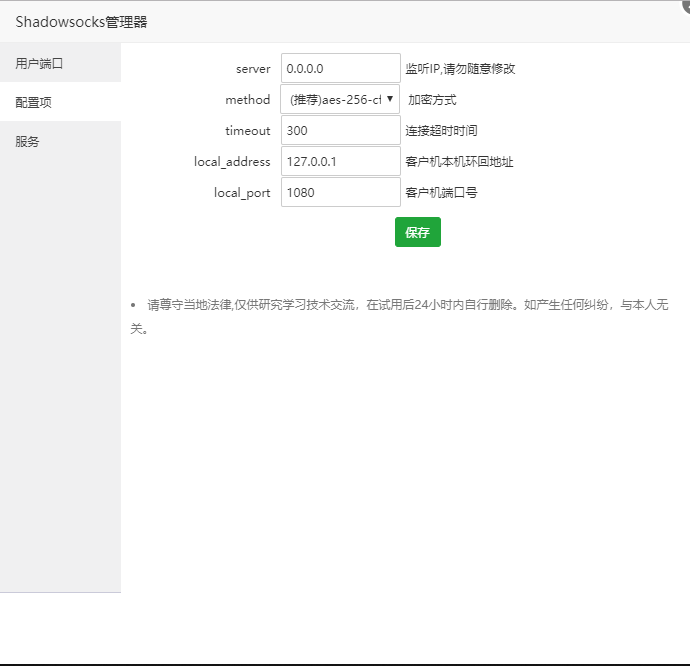
V matters needing attention
1. Speed
2. IP problems
3. Safety issues
Popular articles
-
one WP AutoBlog plug-in (v1.2.15) original&Kaixin version with decryption, cracking ideas | long-term update -
two My unique skill -
three Happy New Year's Day 2019, New Year -
four IPhone X Plus exposure: 6.5-inch screen price breaks ten thousand iOS learning from beginner to proficient Ji Changxin -
five At the same time, the pagoda environment is equipped with the ss plug-in (which can bypass the Web authentication to access the Internet for free udp53
Best article
-
one WP AutoBlog plug-in (v1.2.15) original&Kaixin version with decryption, cracking ideas | long-term update -
two IOS shortcuts, many practical (non) small functions -
three Programmer Algorithm Foundation - Dynamic Programming -
four Android users are reluctant to change iPhones, mainly because there is no headphone jack - iOS learning from beginner to proficient is all in Ji Changxin -
five My unique skill
Comments:
Ekkles Published on: It is recommended to change the encryption to AEAD encryption. repostone Published on: You are ready to update. performer Published on: good-looking! Daily headlines Published on: The article is good, I really like it Xifengli Blog Published on: Advanced~~~~~~~~

