to configure OpenSSL ChaCha20-Poly1305 upgrade
You may have heard or used CloudFlare and Google are promoting the use of ChaCha20-Poly1305 cipher suite, and even used the Strict SSL certificate in CloudFlare's DNS resolution service. Its configuration enables users to use ChaCha20-Poly1305 for encryption and verification when accessing systems above Android 5.
This tutorial is to teach you how to enable your OpenSSL to support ChaCha20-Poly1305. At the same time, this tutorial also teaches you how to update OpenSSL. It can also be regarded as a note of my own. Of course, this tutorial has been practiced and applied on linpx.com.
Tutorials are practiced under CentOS 7, and 6 has not yet been practiced
If you want to successfully practice under 6, you need to upgrade GCC 4.7 or above and binutils 2.22 or above···
So let's go, we need to update OpenSSL to the latest version, download the source code and start compiling:
cd /usr/src wget https://www.openssl.org/source/openssl-1.0.2-latest.tar.gz tar -zvxf openssl-1.0.2-latest.tar.gz cd openssl-1.0.2g
matters needing attention : The openssl-1.0.2-liatest.tar.gz obtained from wget is the version of openssl-1.0.2g, so the following version is also the version of 1.0.2g
After completing the above, we now have 1.0.2g source code to compile OpenSSL, but before we compile, we need to mark the ChaCha20-Poly1305 patch of CloudFlare
https://github.com/cloudflare/sslconfig/tree/master/patches
The patch of OpenSSL 1.0.2 stable is used here, openssl__chacha20_poly1305_draft_and_rfc_ossl102g.patch has not been tried, but it is OK to use the stable patch. Here is a reminder of this pitfall
curl https://raw.githubusercontent.com/cloudflare/sslconfig/master/patches/openssl__chacha20_poly1305_cf.patch -o openssl__chacha20_poly1305_cf.patch patch -p1 < openssl__chacha20_poly1305_cf.patch
Next, we can start compiling OpenSSL
./config make make test make install
After compiling, we found that $PATH is still an old version, and we need to fix this problem
openssl version OpenSSL 1.0.1e-fips 11 Feb 2013 mv /usr/bin/openssl /usr/bin/openssl.bak mv /usr/include/openssl /usr/include/openssl.bak ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl ln -s /usr/local/ssl/include/openssl /usr/include/openssl echo “/usr/local/ssl/lib” >> /etc/ld.so.conf openssl version OpenSSL 1.0.2g 1 Mar 2016
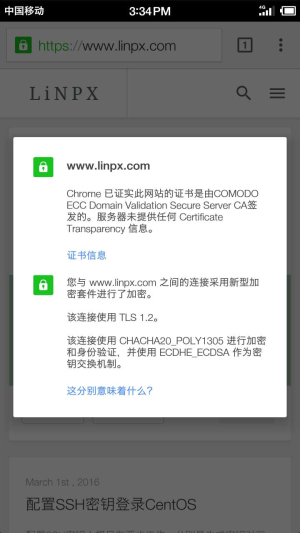
Check whether CHACHA20 is included
openssl ciphers | grep chacha -i ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-CHACHA20-POLY1305
So far, I have installed the latest OpenSSL for the server and supported ChaCha20-Poly1305. Now it is only necessary to compile a new version for Nginx and reference the new encryption suite Next The article explains in detail.
This article is written by Chakhsu Lau Creation, adoption Knowledge Sharing Attribution 4.0 International License Agreement.
All articles on this website are original or translated by this website, except for the reprint/source. Please sign your name before reprinting.