Nginx HSTS HTTPS Preload List
HSTS is the abbreviation of "HTTP Strict Transport Security" (HTTP Strict Transport Security). After this setting is enabled, mainstream browsers will forcibly use HTTPS to request resources, which can more effectively protect the data security of your website and users. In general (HSTS is not enabled), the browser will allow users to continue to use insecure connections to access after they understand the security risks. However, if HSTS is enabled, this is not allowed. Therefore, you must plan to use HTTPS for a long time before starting HSTS.
First, our website linpx.com joined Chrome's HSTS Preload List In Chromium transport_security_state_static.json Can be viewed in
Enable HSTS
HSTS is a response header in the following format:
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload;
- The max age, in seconds, tells the browser that the website must be accessed through the HTTPS protocol within a specified time. That is, for the HTTP address of this website, the browser needs to replace it with HTTPS locally before sending the request
- IncludeSubDomains, an optional parameter. If this parameter is specified, it means that all sub domains of this website must also be accessed through the HTTPS protocol
- Preload, an optional parameter, preloads to the browser cache
The HSTS response header can only be used for HTTPS responses; The website must use the default 443 port; Domain name must be used, not IP. After HSTS is enabled, users cannot choose to ignore the site certificate once it is wrong.
Here is a simple tutorial for Nginx to start HSTS
Open the Nginx conf configuration file corresponding to the website
Suppose my configuration file is in the directory of/usr/local/nginx/conf/vhost
vim /usr/local/nginx/conf/vhost/www.linpx.com.conf
join
server { ··· add_header Strict-Transport-Security "max-age=31536000; includeSubdomains; preload"; ···
Apply for Preload List
HSTS will not take effect until the browser has visited your website once. If you want to take effect in advance, you need to apply for HSTS Preloading List.
At present, the Preload List is maintained by Google Chrome, which is used by Chrome, Firefox, Safari, IE 11 and Microsoft Edge. If you want to add your domain name to this list, you must first meet the following conditions:
Go when you feel comfortable HSTS Preload List (hstspreload.appspot.com) This page applies.
Enter your website in the only text box. This list is reviewed manually, so it may take a while
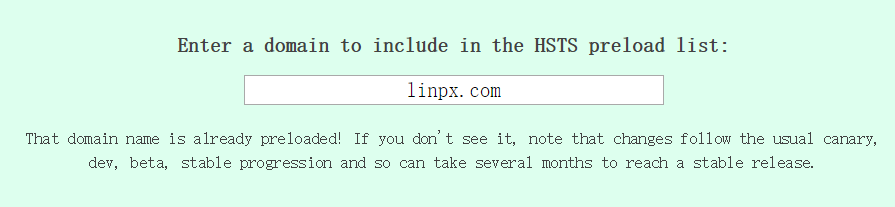
This is the effect of successfully joining the HSTS website
Special Reminder : For HSTS and HSTS Preload List, if you cannot ensure that HTTPS services are always provided, do not enable them. Because once HSTS takes effect, if you want to redirect the website to HTTP, old users will be redirected indefinitely. The only way is to change the domain name.
That's about it. This article is based on the previous article( Optimization of Nginx's SSL configuration )Supplement to.
At the same time, because I have read QuQu's articles many times, and I am familiar with and agree with what he said, this article refers to many parts: imququ.com/post/sth-about-switch-to-https.htm
This article is written by Chakhsu Lau Creation, adoption Knowledge Sharing Attribution 4.0 International License Agreement.
All articles on this website are original or translated by this website, except for the reprint/source. Please sign your name before reprinting.