CentOS HTTPS Certificate Transparency
Don't introduce too much, learn more and recommend https://imququ.com/ Well, this... I've seen it several times anyway···
First of all, there is a problem: Alibaba ECS cannot connect to ct.googleapis.com, that is, it cannot submit the pem to Google's server to obtain the SCT file. At present, my solution is to submit it with foreign vps, obtain the sct, upload it to ECS, and restart Nginx.
Rendering first
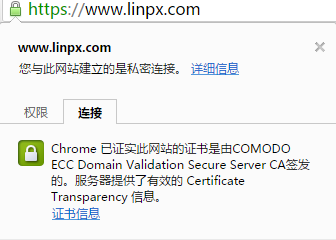
This tutorial is based on AliCloud ECS and CentOS 7. x, and has not been tested too much in other cases
Get SCT
Install Go
yum install golang
Download ct submit and compile it
cd /usr/src wget https://github.com/grahamedgecombe/ct-submit/archive/v1.0.0.tar.gz tar -xzvf v1.0.0.tar.gz cd ct-submit-1.0.0 go build
After the compilation is successful, an executable named ct-submit-1.0.0 will appear in the current directory, and the submission will be executed
Before submission, you need to concatenate the certificates. The certificates to be concatenated here are site certificates and intermediate certificates, and the root certificate is not required.
cat www_linpx_com.crt COMODOECCDomainValidationSecureServerCA.crt COMODOECCAddTrustCA.crt > chained.pem
I put chained. pem in/usr/local/nginx/conf/vhost/sslkey/
Then create a new directory/usr/local/nginx/conf/vhost/sct/to store the SCT files obtained after the next submission
Enter the ct-submit-1.0.0 directory just compiled and execute the submission
./ct-submit-1.0.0 ct.googleapis.com/aviator </usr/local/nginx/conf/vhost/sslkey/chained.pem >/usr/local/nginx/conf/vhost/sct/aviator.sct ./ct-submit-1.0.0 ct.googleapis.com/pilot </usr/local/nginx/conf/vhost/sslkey/chained.pem >/usr/local/nginx/conf/vhost/sct/pilot.sct ./ct-submit-1.0.0 ct.googleapis.com/rocketeer </usr/local/nginx/conf/vhost/sslkey/chained.pem >/usr/local/nginx/conf/vhost/sct/rocketeer.sct ./ct-submit-1.0.0 ct1.digicert-ct.com/log </usr/local/nginx/conf/vhost/sslkey/chained.pem >/usr/local/nginx/conf/vhost/sct/digicert.sct
The above codes have submitted certificates to Google and Digicert servers respectively, but Google cannot submit them because Alibaba ECS cannot connect to Google. You need to get a foreign vps and submit it to your own Alibaba ECS after obtaining it.
Add CT module
Because OpenSSL 1.0.2+has been done for Nginx before, you can see this article: https://www.linpx.com/p/nginx-chacha20poly1305-encryption-suite.html And this article: https://www.linpx.com/p/the-openssl-chacha20poly1305-cipher-suite.html It will not be introduced too much here, but the addition of CT module requires the support of OpenSSL 1.0.2+
cd /usr/src wget https://github.com/grahamedgecombe/nginx-ct/archive/v1.2.0.tar.gz tar -xzvf v1.2.0.tar.gz
Then download Nginx1.9.12
wget http://nginx.org/download/nginx-1.9.12.tar.gz tar -xzvf nginx-1.9.12.tar.gz
Check the configuration arguments of your Nginx. The next step of installation and compilation requires
nginx -V
Copy the content of configure arguments in /After configure, take the content you copied, and then don't forget to add --add-module=/usr/src/nginx-ct-1.2.0 , and then execute
cd nginx-1.9.12 make clean ./configure --prefix=/usr/local/nginx --user=www --group=www --with-openssl=/usr/src/openssl-1.0.2g --add-module=/usr/src/nginx-ct-1.2.0 --with-http_stub_status_module --with-http_v2_module --with-http_ssl_module --with-ipv6 --with-http_gzip_static_module --with-http_realip_module --with-http_flv_module --with-ld-opt="-ljemalloc" make && make install
Modify Configuration
Assume that the configuration file is in the /usr/local/nginx/conf/vhost Contents of
vim /usr/local/nginx/conf/vhost/www.linpx.com.conf
Add in the parentheses of server {}
ssl_ct on; ssl_ct_static_scts /usr/local/nginx/conf/vhost/sct;
be careful :/usr/local/nginx/conf/vhost/sct Replace with the directory where your sct files are stored
Please remember to restart Nginx after configuration!
systemctl restart nginx
Ok, So far, it is complete to enable the Certificate Transparency policy for HTTPS certificates. Next, it is time to review the front-end knowledge and data structure. I hope you can pay more attention to my blog, and also hope you can learn something from my blog. In addition, please remember to take everything with you when reprinting it. Thank you.
This article is written by Chakhsu Lau Creation, adoption Knowledge Sharing Attribution 4.0 International License Agreement.
All articles on this website are original or translated by this website, except for the reprint/source. Please sign your name before reprinting.