At about 16:00 this afternoon, a netizen found a repo called the source code of the backstage project of the website of Station B on GitHub. In just a few hours, the number of forks has reached 1.6w+, and the official has not replied yet. Let's see what's going on?
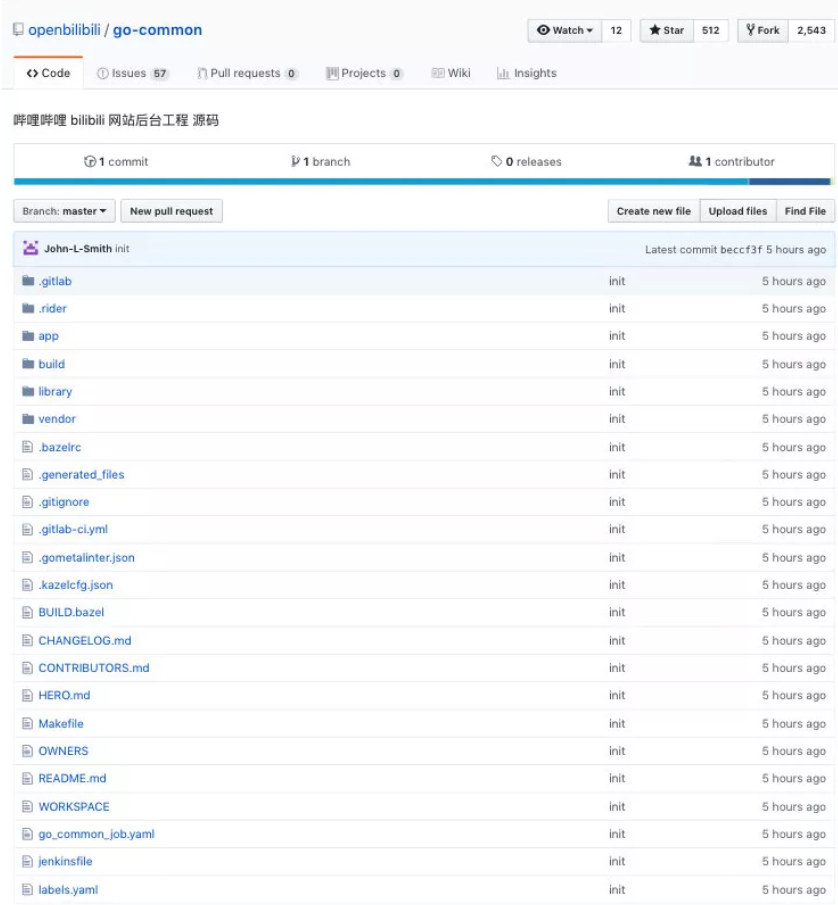
However, the project is not hosted under the official organization domain of Station B. Is it open source?
According to the readme description of repo, it seems to be used for internal communication of the team, for example, it specifies the person in charge of each business of the project and the relevant project specifications.
Look back at the files in the repo from the gitlab-ci.yml According to the file, the project should be hosted in GitLab, Repo also contains relatively complete and detailed business codes, as follows :
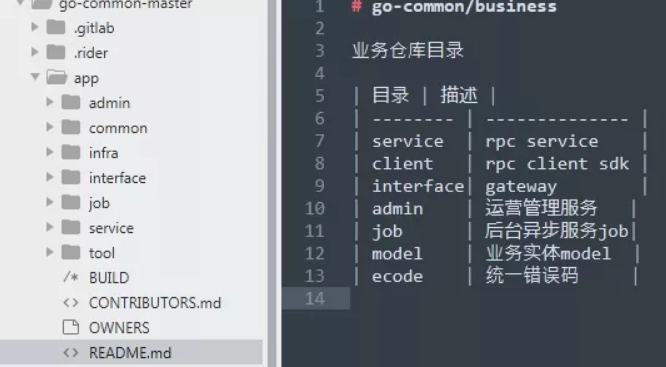
This is the background project source code of Station B, and The most direct consequence of this source code leakage is undoubtedly to expose many hidden dangers directly 。 If someone wants to attack Station B through its back-end code, he does not need to reverse engineer it to guess its operating principle and vulnerability location - now he can read the source code directly to find many undisclosed vulnerabilities.
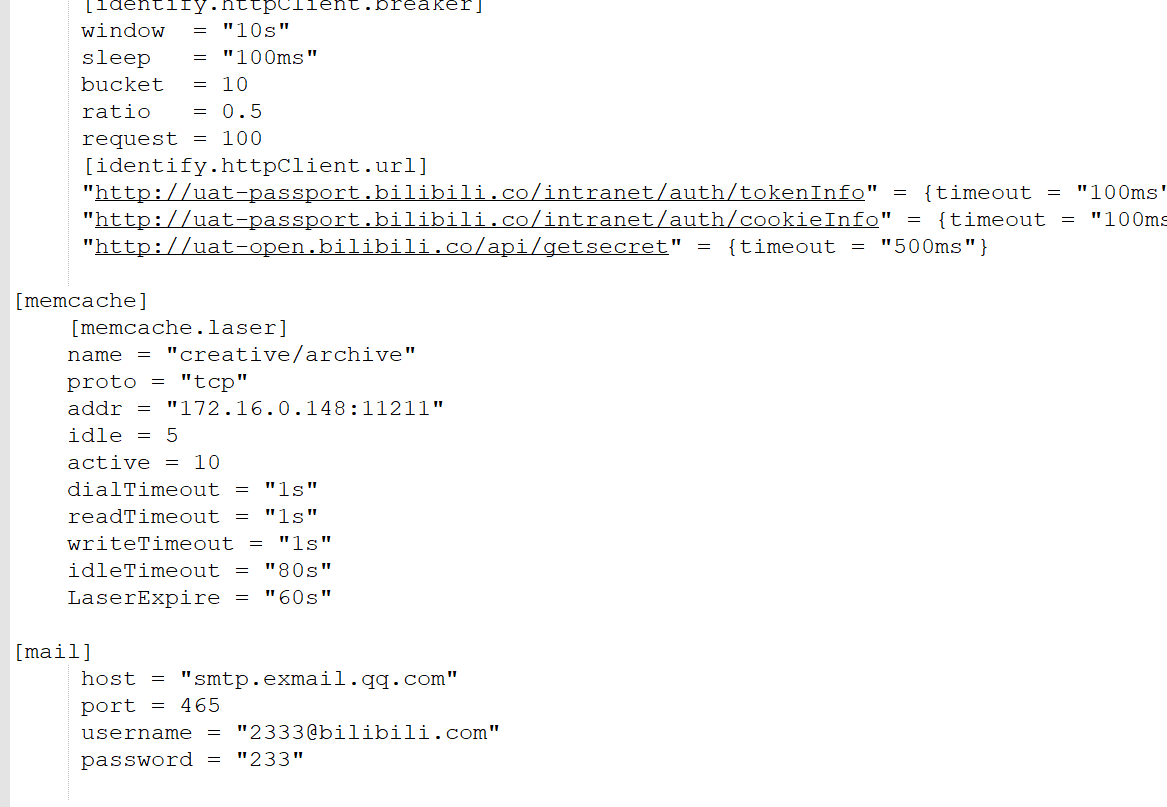
The code comments of site B developers are also very humorous. Do you think you can draw a lottery
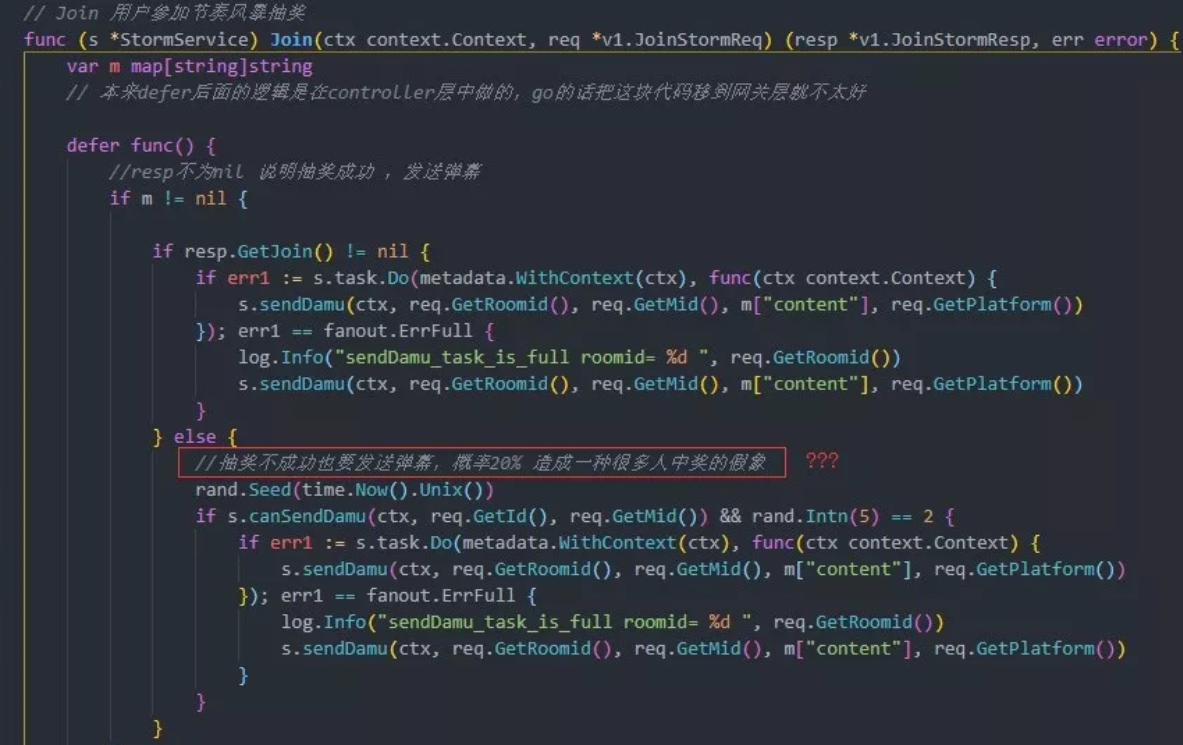
Of course, the access to the warehouse has been forbidden at present. Don't make fun of it. Can you run successfully after downloading the local database? Ha ha ha~





