-
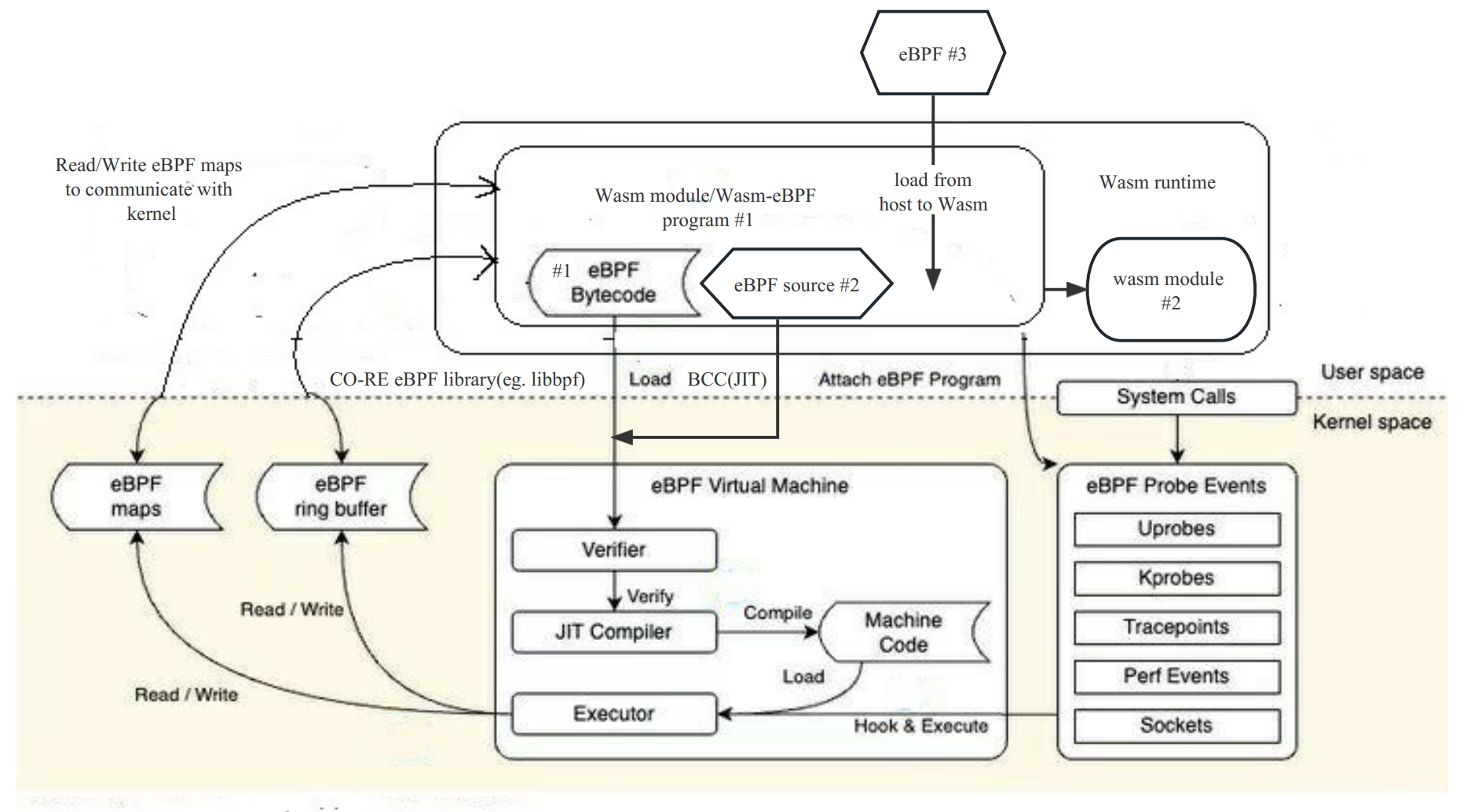
Highlights: currency : Provides most of the eBPF functions for WASM. For example, from ring buffer perhaps perf buffer Get data from, pass maps provide kernel EBPF and User status Bi directional communication and dynamics between Wasm programs load , additional perhaps Disattach EBPF program, etc. It supports a large number of eBPF program types and map types, covering Tracing , Networking , Security Use scenarios for. High performance : For complex data types, no additional serialize expenses. adopt Shared memory To avoid additional data copies between the host and the WASM side. Simple and convenient development experience : Provide and libbpf-bootstrap Similar development experience, Auto generate Wasm-eBPF skeleton Header file and the type definition. Very light : The binary file compiled is only 1.5 MB The size of the compiled WASM module is ~90K , which is much lighter than the traditional way of distributing and running eBPF programs in containers, while maintaining good isolation and sandbox characteristics. You can easily use any language, build your own Wasm-eBPF runtime on any platform, and use the same tool chain to build applications!
-
Demo video: https://www.bilibili.com/video/BV1vD4y1P78S/ -
Sample code:
/* Load and verify BPF application */ skel = bootstrap_bpf__open(); if (!skel) { fprintf (stderr, " Failed to open and load BPF skeleton \\n " ); return one ; }
<span style="color:var(--color-prettylights-syntax-comment)"><span style="color:var(--color-prettylights-syntax-comment)">/*</span> Parameterize BPF code with minimum duration parameter <span style="color:var(--color-prettylights-syntax-comment)" >*/</span></span> skel->rodata->min_duration_ns = env.min_duration_ms * <span style="color:var(--color-prettylights-syntax-constant)">1000000ULL</span>; < span style="color:var(--color-prettylights-syntax-comment)"><span style="color:var(--color-prettylights-syntax-comment)">/*</span> Load & verify BPF programs <span style="color:var(--color-prettylights-syntax-comment)">*/</span></span> err = bootstrap_bpf__load(skel); <span style="color:var(--color-prettylights-syntax-keyword)">if</span> (err) { <span style="color:var(--color-prettylights-syntax-constant)">fprintf</span>(stderr, <span style="color:var(--color-prettylights-syntax-string)"><span style="color:var(--color-prettylights-syntax-string)">"</span>Failed to load and verify BPF skeleton<span>\\n</span><span style="color:var(--color-prettylights-syntax-string)">"</span></span>); <span style="color:var(--color-prettylights-syntax-keyword)">goto</span> cleanup; } < span style="color:var(--color-prettylights-syntax-comment)"><span style="color:var(--color-prettylights-syntax-comment)">/*</span> Attach tracepoints <span style="color:var(--color-prettylights-syntax-comment)">*/</span></span> err = bootstrap_bpf__attach(skel); <span style="color:var(--color-prettylights-syntax-keyword)">if</span> (err) { <span style="color:var(--color-prettylights-syntax-constant)">fprintf</span>(stderr, <span style="color:var(--color-prettylights-syntax-string)"><span style="color:var(--color-prettylights-syntax-string)">"</span>Failed to attach BPF skeleton<span>\\n</span><span style="color:var(--color-prettylights-syntax-string)">"</span></span>); <span style="color:var(--color-prettylights-syntax-keyword)">goto</span> cleanup; }</ pre>
extern "C" fn handle_event ( _ctx : u32 , data : u32 , _data_sz : u32 ) { let event_slice = unsafe { slice :: from_raw_parts ( data as * const Event , one ) } ; let event = & event_slice [ zero ] ; let pid = event . pid ; let ppid = event . ppid ; let exit_code = event . exit_code ; if event . exit_event == one { ! ( "{:<8} {:<5} {:<16} {:<7} {:<7} [{}]" , "TIME" , "EXIT" , unsafe { CStr ::from_ptr ( event.comm.as_ptr ( ) as * const i8 ) } .to_str ( ) .unwrap ( ) , pid, ppid, exit_code ) ; .. . }
# push to Github Packages ecli push https://ghcr.io/eunomia-bpf/sigsnoop:latest # pull from Github Packages ecli pull https://ghcr.io/eunomia-bpf/sigsnoop:latest # run eBPF program ecli run https://ghcr.io/eunomia-bpf/sigsnoop:latest
-
Subsequent update plan: -
Continue to improve multilingual support; -
Support more perfect eBPF features; -
Explore more application scenarios;
-