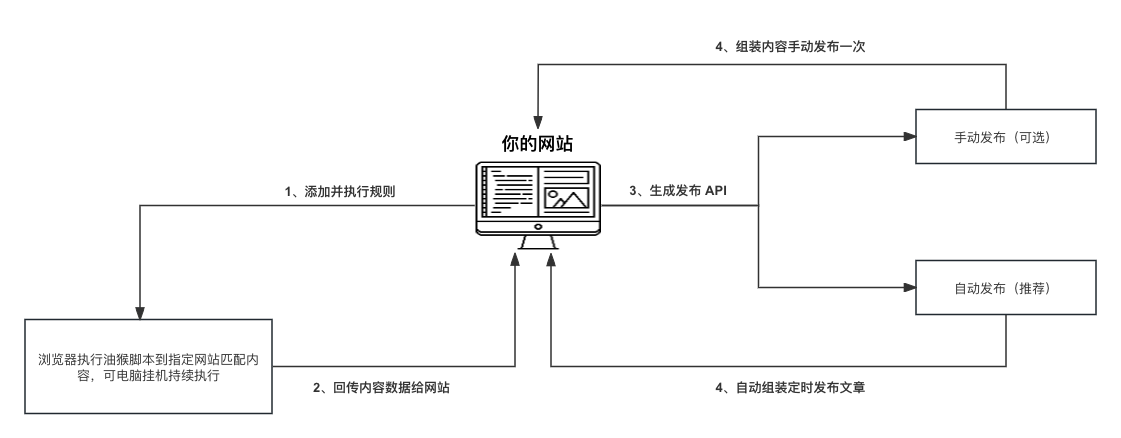
Presumably, all webmaster friends are no strangers to this kind of tool, and they are just talking nonsense and going straight to the topic. This plug-in mainly collects content from the network by setting keywords in batches. Compared with the traditional article collection tool, this plug-in has the advantage that the matching content logic is completely based on browser behavior, and there is no need to simulate any parameters on the server to request, It greatly reduces the interception in the agentless IP state
Read on →
In this guide, the so-called server has been invaded or hacked means that unauthorized people or programs log in to the server for their own purposes and use its computing resources, which usually has a bad impact. Disclaimer: If your server is invaded by a state organ like NSA or a criminal group, you will not notice any problems, and these technologies cannot detect their existence. However, most of the compromised servers are intruded by programs like automatic attack programs or cheap attackers like "script kids", as well as stupid criminals. Such attackers will abuse server resources while accessing the server, and seldom take measures to hide what they are doing
Read on →
Problem details: 'MixedContent: The pageat' XXXX 'was loadedoverHTTPS, but requestedaninsecureXMLHttpRequest endpoint' XXXX '. This request has been blocked; the content must be servedoverHTTPS.' The reason is that the current website is the interaction mode of HTTPS protocol, but HTTP appears on the page
Read on →
1. Modify the/etc/hosts. deny file. The command is as follows: sudovi/etc/hosts. deny 2. Rules for writing content: # Deny specifying IPsshd: 127.0.0.1 # Deny IP segment (wildcard symbol '.') sshd: 127.0.0
Read on →
The command is as follows: tail-10000/nginx_log_path. log | awk vFS='|' '{print $2}' | sort | uniq-c | sort-k1-nr | head-n20
Read on →