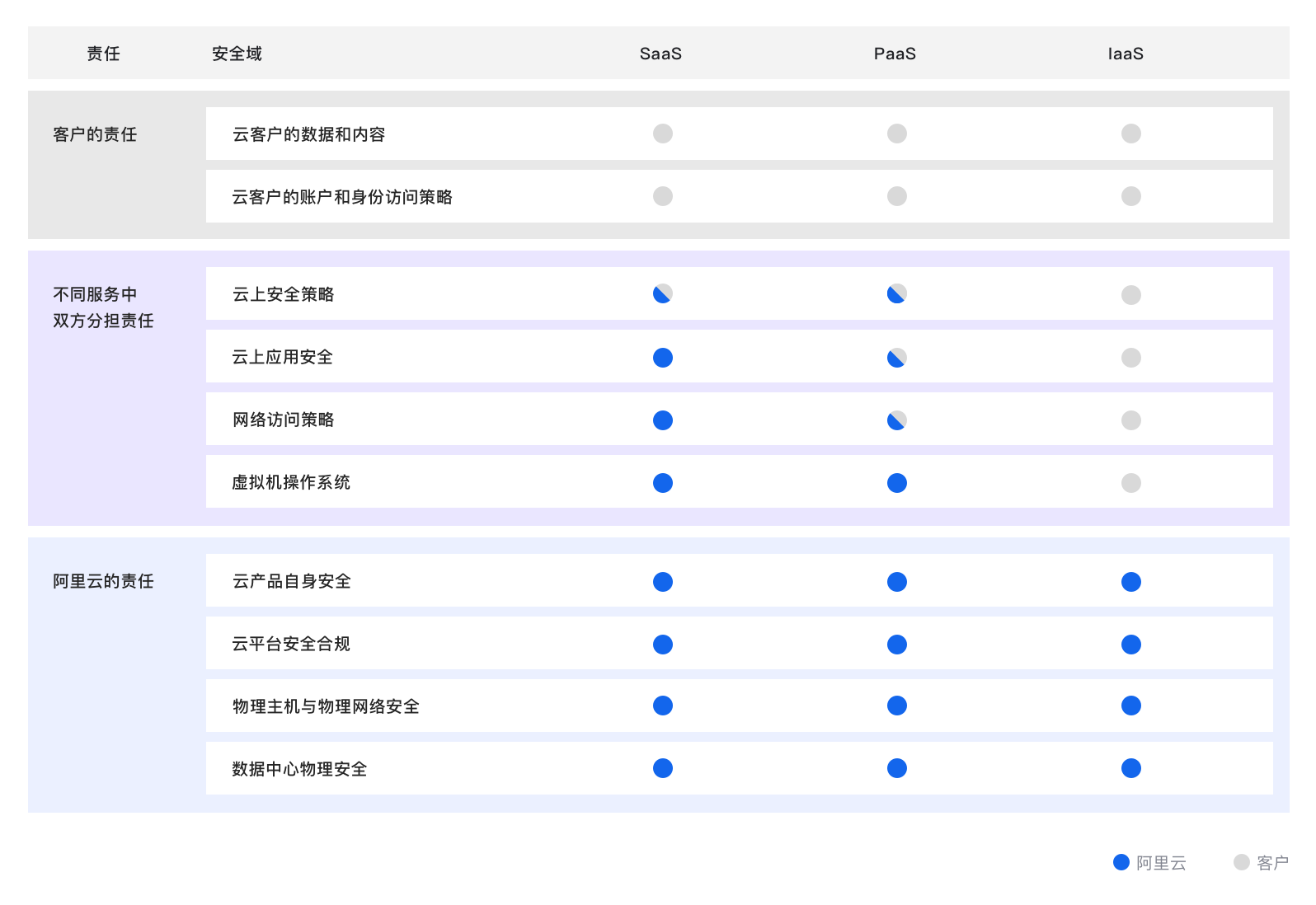
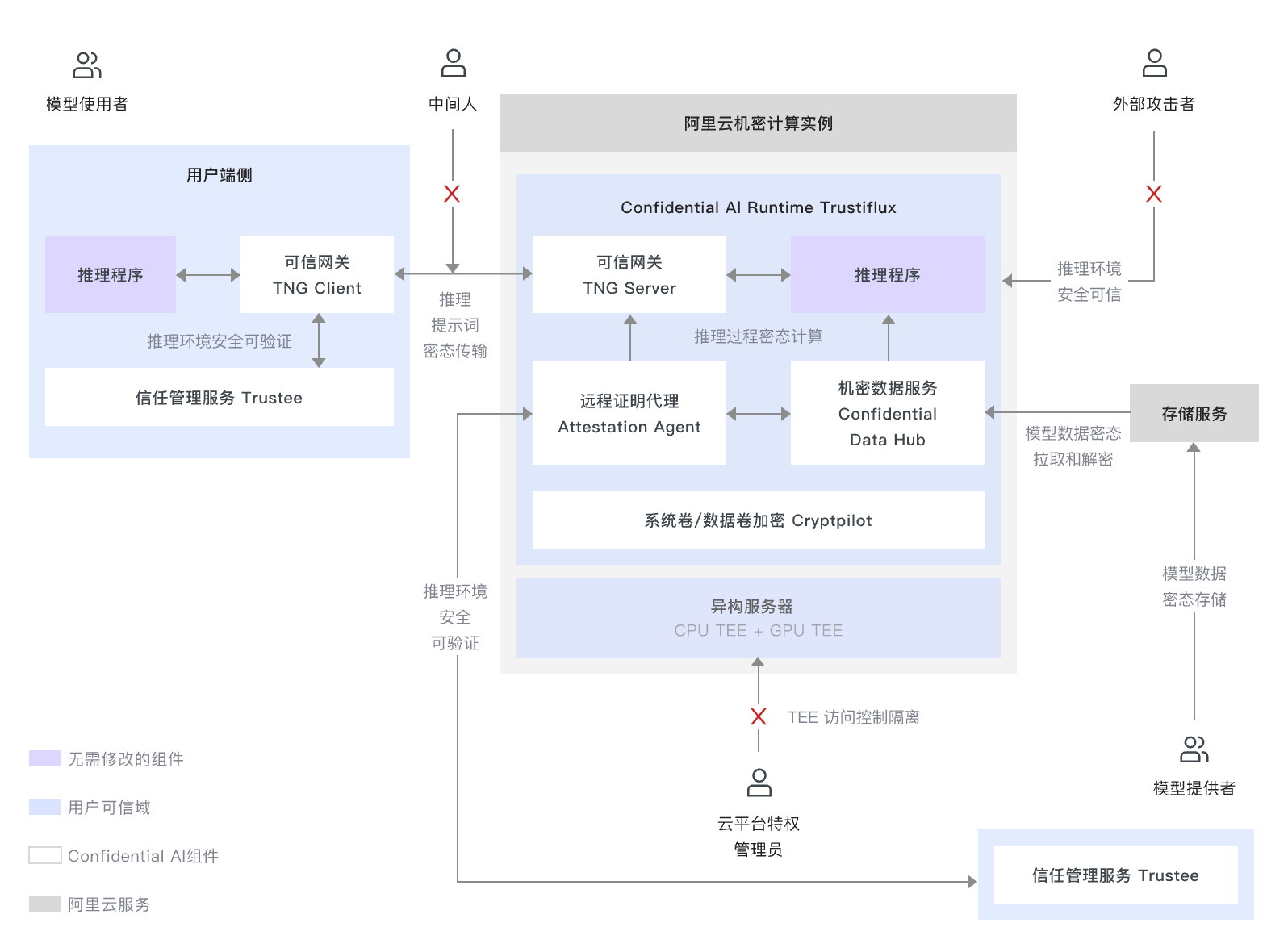
Security Compliance
One of the cloud service providers with the most comprehensive compliance qualifications in Asia Pacific, it ensures the business safety of thousands of customers online from four aspects: infrastructure security, kernel platform security, system service security, and cloud security products. It has an authoritative and recognized native security capability. According to the Gartner report in 2021, the security capability ranks first in the world.