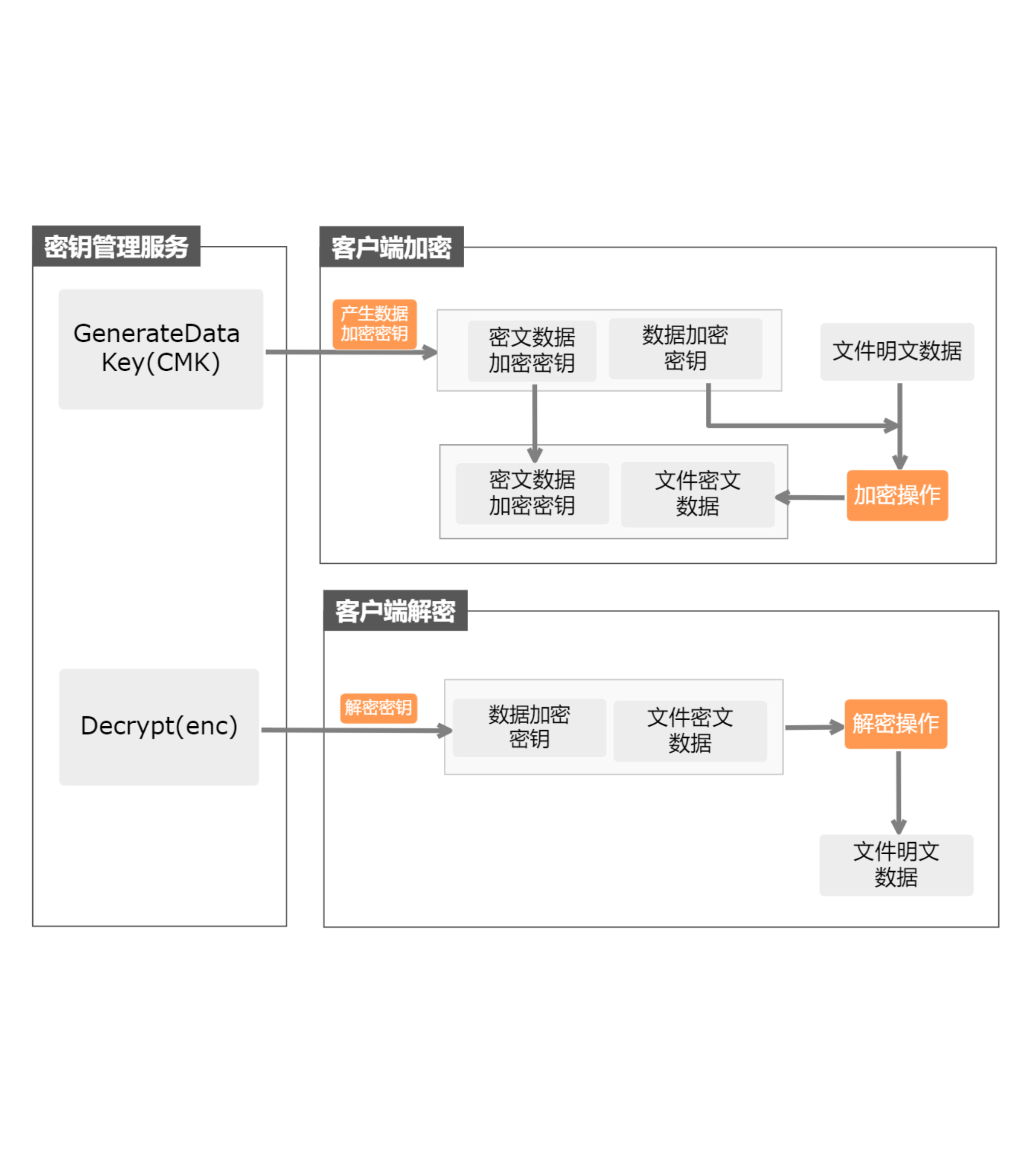
Extensive cloud product integration
The key management service is widely integrated with AliCloud products such as ECS, cloud database, object storage, and file storage. You can use the key in the key management service to encrypt the data in these products, help you protect sensitive data assets, and enhance the default security capabilities of cloud products.