#If someone visits your website via IP or unknown domain name, you want to disable the display of any valid content, you can return 500 server { listen 80 default; server_name _; return 500; } #Open one or more real domain name configurations that you want to access. The settings are as follows: server { linten 80; server_name naibabiji.com; }
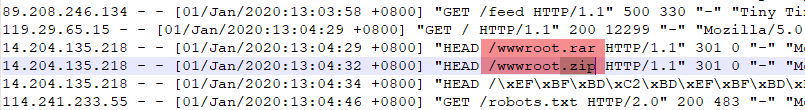
rewrite \.asp/?$ http://speedtest.tele2.net/50GB.zip permanent; rewrite \.zip/?$ http://speedtest.tele2.net/50GB.zip permanent; rewrite \.gz/?$ http://speedtest.tele2.net/50GB.zip permanent; rewrite \.7z/?$ http://speedtest.tele2.net/50GB.zip permanent; rewrite \.sql/?$ http://speedtest.tele2.net/50GB.zip permanent; rewrite \.rar/?$ http://speedtest.tele2.net/50GB.zip permanent; rewrite \.tar/?$ http://speedtest.tele2.net/50GB.zip permanent;
http://speedtest.tele2.net/1000GB.zip http://speedtest.tele2.net/100GB.zip http://speedtest.tele2.net/50GB.zip
location ~ \.(zip|rar|sql|bak|gz|7z)$ { return 444; }
444 No Response
HTTP server extension on Nginx. The server does not return any information to the client and closes the connection (helps prevent malware)
wget https://github.com/loveshell/ngx_lua_waf/archive/master.zip -O ngx_lua_waf.zip unzip ngx_lua_waf.zip mv ngx_lua_waf-master /usr/local/nginx/conf/waf
lua_package_path "/usr/local/nginx/conf/waf/?. lua"; lua_shared_dict limit 10m; init_by_lua_file /usr/local/nginx/conf/waf/init.lua;
access_by_lua_file /usr/local/nginx/conf/waf/waf.lua;
This is the 11th/20th article in the series: WordPress Security
-
How to use plug-ins to automatically back up WordPress websites _ website backups -
Share a case of foreign trade WordPress website being maliciously redirected -
Protect WordPress Website Security_Wordence Firewall Professional Edition Download -
10 excellent WordPress backup plug-ins recommended to prevent data loss -
4 malware scanning plug-ins officially recommended by WordPress -
Recommendations and selection of six popular WordPress security plug-ins in 2021 -
List of vulnerabilities in WordPress plug-ins in March -
Method of password free random email link login to WordPress website -
11 Useful WordPress Verification Plugins _Captcha Verification Code -
9 WordPress violent login protection plug-ins to protect website security -
Server security: add Nginx rules to prevent servers from being scanned by malicious robots -
WordPress website security log plug-in: WP Security Audit Log -
Troubleshooting for WordPress website being hacked and redirected to other websites -
Four WordPress require a password to access the website's plugin_password to view content -
WordPress security plug-in recommendation: Defender Security_malware scanning_firewall -
Methods for WordPress website to block access of specific robots and crawlers -
Do a good job of security protection to prevent WordPress website from being hacked -
Protect website security, manually update Nginx version to fix vulnerability (LNMP and pagoda panel) -
Hide WordPress background login address to improve security WPS Hide Login -
Using BackWPup to Back Up Your Website Database and Files Tutorial





