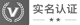
Recently, Microsoft announced the "worm type" pre authorized remote code execution vulnerability found in Server Message Block 3.0 (SMBv3). At present, the detailed official patch for this vulnerability has not been released by Microsoft.
The vulnerability is caused by an error in the SMBv3 protocol when processing malicious compressed packets, which can allow remote and unauthenticated attackers to execute arbitrary code on the target system.
Although Microsoft did not issue more detailed vulnerability recommendations, some security vendors who learned the vulnerability information earlier in Microsoft's proactive protection plan released detailed information about CVE-2020-0796 security vulnerabilities.
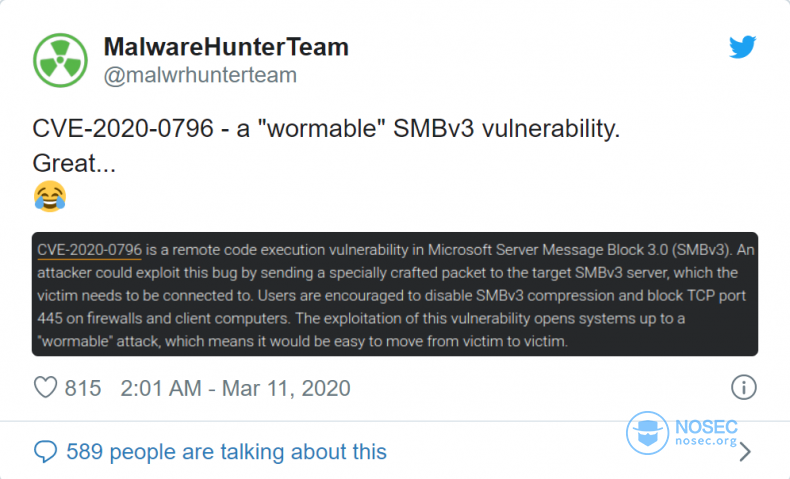
Windows 10 on the desktop and server side is affected
According to Fortinet's security report, Windows 10 Version 1903, Windows Server Version 1903 (Server Core installation), Windows 10 Version 1909, And Windows Server Version 1909 (Server Core installation) are affected by this vulnerability. However, it is worth noting that Windows 8 and Windows Server 2012, which introduced SMBv3, may also be affected.
Cisco Talos said in the Microsoft patch report on Tuesday: "An attacker can exploit this vulnerability by sending a special packet to the target SMBv3 service."

Microsoft also issued a security recommendation, which details how to disable SMBv3 compression to protect servers from attacks.
You can disable compression of the SMBv3 service (without restarting) by using the following PowerShell command:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" DisableCompression -Type DWORD -Value 1 -Force
In addition, you can also prevent attacks by preventing SMB traffic from flowing to the Internet.