In WordPress 4.7.0 and 4.7.1, there is an unauthorized vulnerability in the REST API. In the past two days, hackers have used REST API vulnerabilities to launch attacks on WordPress websites and edited 1.5 million pages with 39000 domain names. The vulnerability allows an attacker to send a simple HTTP request, bypass the authentication system, and edit the title and content of WordPress web pages. It only affects WordPress v4.7.0 and 4.7.1. The security company Sucuri reported on Monday that 67000 WordPress pages have been altered by this method, but the number of pages edited in the past two days has exploded, and attacks continue. The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
This vulnerability has been fixed in WordPress v4.7.2 released last month, which does not prevent the site from being tampered with by hackers. The corrupt fish reminds webmasters to backup and upgrade Wordpress to the latest version as soon as possible. The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
WordPress REST API The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
First, let's briefly introduce the use of REST API. The introduction given by Wordpress Think Tank is as follows: The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
WordPress is moving towards becoming a full stack application framework, and we need new APIs. So the WordPress JSON REST API project was born. The purpose of this project is to create a framework that is easy to use, easy to understand, and well tested to create these APIs. At the same time, it also creates APIs for the WordPress core. The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
This plug-in (WordPress JSON REST API (WP API)) provides an easy-to-use REST API, allowing us to obtain simple and convenient JSON format data through HTTP, including users, articles, classifications, etc. Obtaining or updating data is very simple. You only need to send an HTTP request. The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
Please refer to REST API Handbook for details The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
https://developer.wordpress.org/rest-api/ The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
WordPress 4.7.1 Ultra vires Vulnerability Analysis The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
Before using the API to operate the article, you need to authorize the operation. There are three authorization methods: cookie, oauth, and simple authentication. If you modify the article directly through the API without authorization, a 401 will be returned, as shown in the following figure The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
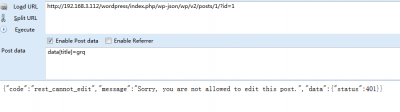 The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
If you want to successfully exploit the vulnerability, you must bypass the permission management, that is, bypass the update_item_permissions_check() module to make its final return true. The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
If the url we input is in this form The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
http://192.168.3.112/wordpress/index.php/wp-json/wp/v2/posts/1/?id=1grq The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
The return value of the get_post() function must be null, which will make the $post value null. Looking back at the update_item_permissions_check() function, the return value of the update_item_permissions_check() function is actually true! The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
WordPress 4.7.1 unauthorized vulnerability exploitation The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
At present, some researchers have given corresponding poc on GitHub. The link is as follows The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
https://gist.github.com/leonjza/2244eb15510a0687ed93160c623762ab The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
WordPress 4.7.1 Ultra vires Vulnerability Patch The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
The unauthorized vulnerability of WordPress 4.7.1 has not been avoided. Please upgrade to WordPress 4.7.2 as soon as possible. Wordpress has completely fixed this vulnerability in version 4.7.2. If get_post() determines that the result of $post is false, it returns $post directly to prevent $post from entering the lower level if to bypass the permission check. The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
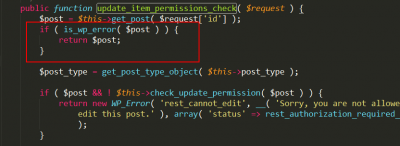 The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html
The article originates from the fallen fish- https://www.duoluodeyu.com/2409.html