Compliance guidance
Upgrade the latest SDK
Please make sure that you have upgraded the Evoque security certification SDK to meet the new regulatory regulations Latest version 。
SDK Business Function Description
Access description : The Evoque security authentication SDK includes basic business functions and extended business functions.
basic function : Provides one click login function for developers to achieve one click login of end user accounts.
Extended functions : Provide the number verification and user account security verification functions for the development, realize the end user number verification, and verify the user account and behavior security.
Special Reminder : For extended business functions, you can turn off optional personal information collection (such as accurate location information, software list information) to realize the shutdown of extended functions (developers can use Aurora Android:《 SDK API Guide 》、iOS:《 SDK API Guide 》View interface description document).
Configuration description of SDK optional personal information
Access description : For the control of personal information collected by the Evoque security authentication SDK, developers can use the Evoque Android:《 SDK API Guide 》、iOS:《 SDK API Guide 》 。 Due to non collection of relevant information It will seriously affect the realization and effect of some functions of the Aurora security authentication SDK. We strongly recommend that you open , please make reasonable configuration according to the actual business needs.
Description of optional personal information of Evoque security certification SDK:
a. Device hardware information (including device model, device screen resolution, device hardware manufacturer, device product name): used to ensure the compatibility of the products and/or services provided on different devices, and detect the malicious forgery of devices;
b. Operating system information (including operating system version, system name, system language): used to ensure the compatibility of the products and/or services provided on different devices;
c. Precise location information : used to provide login reports by region and calibrate the regional distribution of data; Identification of abnormal equipment and other gang attacks/identification of geographical location forgery, protection of user account security, etc;
d. Software list information (including software list and software running list information): used to identify the user's application environment and determine the installed APP information, help you identify abnormal software and intercept the batch automatic operation of machine programs, protect the security of user accounts, etc.
SDK Personal Information Collection Frequency and Precision Description
Access description : We will collect personal information of users according to the minimum necessity of realizing business functions. In terms of collection frequency, the data collection of the Evoque security certification SDK is only triggered when the app calls the relevant functions. As for the frequency, the app developers cannot configure it by themselves, so we do not provide optional configuration methods and examples for the frequency; In terms of collection accuracy, it mainly involves positioning related functions, which are mainly controlled by permissions. The Aurora security authentication SDK allows App to control whether to apply for precise geographical location permissions or rough geographical location permissions through optional permissions. If you need to configure location permissions, please refer to the following“ Description of SDK application for system permissions ”Configure.
Description of SDK application for system permissions
Access description: For the system permissions that can be optionally applied for by the Evoque Security Certification SDK, you can refer to the relevant table below to learn more about the relationship between the relevant permissions and various business functions and their application timing. Since the relevant permissions will not be applied, their corresponding functions will be affected. You can reasonably configure them according to the actual needs of the business.
| Android operating system application permission list |
| jurisdiction |
Optional |
purpose |
| INTERNET |
Mandatory |
Allows applications to network for access to gateways and authentication servers. |
| ACCESS_NETWORK_STATE |
Mandatory |
Allows programs to access WiFi network status information, which is used to detect the security authentication environment, avoid data transmission in abnormal network conditions, and save traffic and power. |
| ACCESS_WIFI_STATE |
Mandatory |
Obtain the network status, determine whether to connect to wifi, and detect the security authentication environment. |
| CHANGE_NETWORK_STATE |
Mandatory |
It is allowed to obtain the permission of the program to change the network connection status, which is used to obtain the user's mobile phone number and realize the security authentication function. |
| CHANGE_WIFI_STATE |
Optional |
The access program is allowed to change the WIFI connection status, which is used to obtain the user's mobile phone number and realize the security authentication function. |
| ACCESS_COARSE_LOCATION |
Optional |
By obtaining rough location information, it provides developers with anti cheating functions and eliminates cheating devices. |
| ACCESS_FINE_LOCATION |
Optional |
By obtaining rough location information, it provides developers with anti cheating functions and eliminates cheating devices. |
| ACCESS_BACKGROUND_LOCATION |
Optional |
Background location permission for Android 10 and above devices. It provides developers with anti cheating functions and eliminates cheating devices. |
| READ_PHONE_STATE |
Optional |
It is used to assist in generating the unique device identifier of Aurora, identify the unique user, ensure the effective identification and quick response of one key authentication, and improve our anti fraud ability. |
| ACCESS_WIFI_STATE |
Optional |
It is used to assist in generating the unique device identifier of Aurora, identify the unique user, ensure the effective identification and quick response of one key authentication, and improve our anti fraud ability. |
| WRITE_EXTERNAL_STORAGE |
Optional |
It is used to assist in generating the unique device identifier of Aurora, identify the unique user, ensure the effective identification and quick response of one key authentication, and improve our anti fraud ability. |
| READ_EXTERNAL_STORAGE |
Optional |
It is used to assist in generating the unique device identifier of Aurora, identify the unique user, ensure the effective identification and quick response of one key authentication, and improve our anti fraud ability. |
| IOS operating system application permission list |
| jurisdiction |
Optional |
purpose |
| App Transport Security Settings |
Mandatory |
Since Unicom 5G number fetching requires HTTP requests, please add a sub project App Transport Security Settings in the project info.plist file, and then add a key: Allow Arbitrary Loads, whose value is YES. After modification, other operators can use one click login. |
| NSLocationWhenInUseUsageDescription |
Optional |
By obtaining location information, it provides developers with anti cheating functions and eliminates cheating devices. |
| NSLocationAlwaysAndWhenInUseUsageDescription |
Optional |
By obtaining location information, it provides developers with anti cheating functions and eliminates cheating devices. |
| NSUserTrackingUsageDescription |
Optional |
It is used to identify the unique user, ensure the effective identification and quick response of one click authentication, and improve our anti fraud ability. |
SDK permission control
Android required permission
- The following permissions are required. The following permissions must be configured to meet the basic authentication capability
<!-- Network permission, used to access the gateway and authentication server (required) --> <uses-permission android:name="android.permission.INTERNET" /> <!-- Allows programs to access WiFi network status information, which is used to detect the security authentication environment, avoid data transmission in abnormal network conditions, and save traffic and power (required) --> <uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/> <!-- Get the network status, determine whether to connect to wifi, and detect the security authentication environment (required) --> <uses-permission android:name="android.permission.ACCESS_WIFI_STATE" /> <!-- Allow to obtain the permission of the program to change the network connection status, which is used to obtain the user's mobile phone number and realize the security authentication function (required) --> <uses-permission android:name="android.permission.CHANGE_NETWORK_STATE" />
< uses-permission android:name = "android.permission.INTERNET" />
< uses-permission android:name = "android.permission.ACCESS_NETWORK_STATE" />
< uses-permission android:name = "android.permission.ACCESS_WIFI_STATE" />
< uses-permission android:name = "android.permission.CHANGE_NETWORK_STATE" />
This code block is displayed in the floating window
Android optional permissions
- By obtaining location information, it provides developers with anti cheating functions and eliminates cheating devices. It is recommended to integrate the following permissions (optional)
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION" /> <uses-permission android:name="android.permission.ACCESS_FINE_LOCATION" /> <uses-permission android:name="android.permission.ACCESS_BACKGROUND_LOCATION" />
< uses-permission android:name = "android.permission.ACCESS_COARSE_LOCATION" />
< uses-permission android:name = "android.permission.ACCESS_FINE_LOCATION" />
< uses-permission android:name = "android.permission.ACCESS_BACKGROUND_LOCATION" />
This code block is displayed in the floating window
It is allowed to obtain the permission of the program to change the network connection status, which is used to obtain the user's mobile phone number and realize the security authentication function. (Optional)
<uses-permission android:name="android.permission.CHANGE_NETWORK_STATE" />
< uses-permission android:name = "android.permission.CHANGE_NETWORK_STATE" />
This code block is displayed in the floating window
It is used to identify the unique user, ensure the effective identification and quick response of one click authentication, and improve our anti fraud ability. It is recommended to integrate the following permissions (optional)
<uses-permission android:name="android.permission.READ_PHONE_STATE" /> <uses-permission android:name="android.permission.ACCESS_WIFI_STATE" /> <!-- Allow programs to read and write to external storage --> <uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" /> <!-- Allow programs to read from external storage --> <uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE" />
< uses-permission android:name = "android.permission.READ_PHONE_STATE" />
< uses-permission android:name = "android.permission.ACCESS_WIFI_STATE" />
< uses-permission android:name = "android.permission.WRITE_EXTERNAL_STORAGE" />
< uses-permission android:name = "android.permission.READ_EXTERNAL_STORAGE" />
This code block is displayed in the floating window
IOS SDK permission control
IOS optional permissions
NSLocationWhenInUseUsageDescription//Access location information NSLocationAlwaysAndWhenInUseUsageDescription//Access location information NSUserTrackingUsageDescription//idfa Package Usage
NSLocationWhenInUseUsageDescription
NSLocationAlwaysAndWhenInUseUsageDescription
NSUserTrackingUsageDescription
This code block is displayed in the floating window
SDK privacy policy disclosure requirements and examples
Access description : After the developers integrate the Evoque security authentication SDK into the app, the normal operation of the Evoque security authentication SDK will collect necessary end-user information for one click login, number verification, and security verification services. According to the actual situation of the integrated Aurora security certification SDK, developers are requested to disclose the name of the Aurora security certification SDK, company name, type and purpose of personal information processing, collection method, privacy policy link and other contents in your App's privacy policy. Suggestion: Confirm the version and functional modules of the Aurora security certification SDK you access, and determine the data content interacting with the Aurora security certification SDK from the privacy policy; In your App's privacy policy, disclose the relevant information of the Evoque security certification SDK to the public in the form of text or list.
Disclosure examples (for reference only, please refer to the actual cooperation):
SDK name : Aurora Security Certification SDK
Third party subject : Shenzhen Hexunhuagu Information Technology Co., Ltd
SDK Usage : Provide APP users with one click login, number verification and security verification services
Process personal information type : device identifier (including IMEI, IDFA, Android ID, GAID, MAC, OAID, IMSI, MEID, UAID, ICCID), device hardware information (including device model, device screen resolution, device hardware manufacturer, device product name), operating system information (including operating system version, system name, system language) Network information (including network type, operator name, base station information, IP address, WiFi information, SSID, BSSID), precise location information, software list information (including software list and software operation list information).
Data processing mode : Through de identification, encrypted transmission and other security methods
Privacy Policy Link :《 AURORA Aurora Privacy Policy 》
Official website link : https://www.jiguang.cn
Description and example of the end user's consent mode
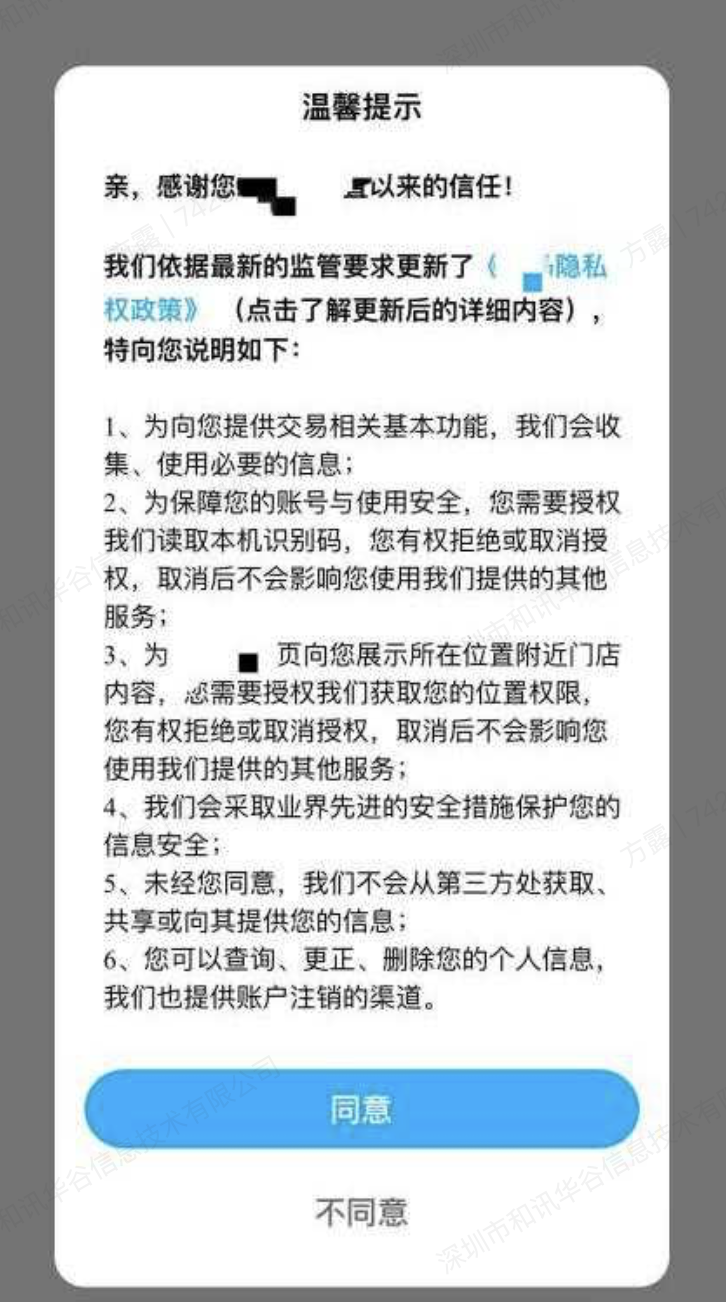
Access description : When the app runs for the first time, there should be a privacy pop-up window, in which the brief version of the privacy policy content should be publicized with a link to the full version of the privacy policy, and the end user should be explicitly prompted to read and choose whether to agree to the privacy policy; The privacy pop-up window shall provide a consent button and a refusal button, which shall be actively selected by the end user. If sensitive personal information is involved, you should obtain your end user's separate authorization consent. You can achieve the end user's authorization through a separate pop-up window, and display sensitive personal information in your Privacy Policy through bold font or other prominent signs.
Pop up window example of privacy policy authorization:
Example of sensitive personal information authorization pop-up window:
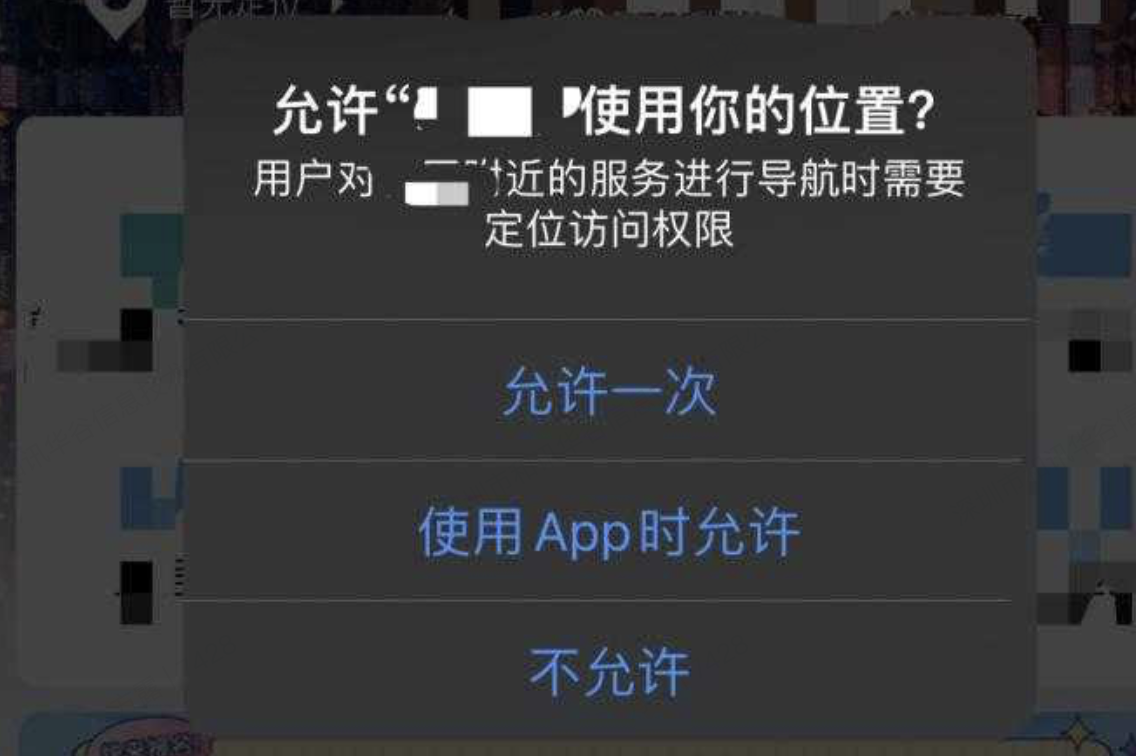
Example of disclosure of sensitive personal information privacy policy :“ Precise location information : used to provide login reports by region and calibrate the regional distribution of data; Identification of abnormal equipment and other gang attacks/identification of geographical location forgery, protection of user account security, etc. "
Description of End User's Exercise of Rights
Access description : After developers integrate the Evoque security authentication SDK in their apps, the normal operation of the Evoque security authentication SDK will collect necessary end-user information for one click login or extended function purposes. Developers should provide end users with the path or function to exercise the rights of personal information subject in accordance with relevant laws and regulations. If you need the cooperation of Evoque Security Certification SDK, please contact Evoque in a timely manner, and we will work with developers to properly address the demands of end users.
SDK Initialization and Business Function Call Timing
Access description : Please be sure to initialize the Aurora security authentication SDK after the user agrees to the privacy policy in your app. Before users agree to the privacy policy, avoid dynamically applying for sensitive device permissions involving users' personal information; Before users agree to the privacy policy, you should avoid collecting and reporting personal information privately.
Initialize SDK
Ensure that the initialization function JVerificationInterface. init() is called only after the user has read your Privacy Policy and obtained the user's authorization when the app is launched for the first time. At this time, the SDK will actually collect device information and report it. If the user has not read your Privacy Policy and obtained the user's authorization, or the user does not agree with your Privacy Policy, The initialization method JVerificationInterface. init() cannot be called. Please note that do not call any API methods of the SDK before calling initialization. For the initialization interface, please refer to the call interface documentation Android:《 SDK API Guide 》; iOS:《 SDK API Guide 》。
SDK business function interface call
After initializing the Aurora security authentication SDK, if you call the SDK business function interface (see the call interface documentation for details Android:《 SDK API Guide 》; iOS:《 SDK API Guide 》, it is deemed that you agree to enable the SDK business function, and at this time we will start to collect and report the user's personal information corresponding to the SDK business function of Evoque security certification; If you refuse to call, it may affect the effect of using the relevant business functions of the Aurora security authentication SDK.
Third party privacy policy disclosure reference
The Evoque security certification SDK also integrates third-party SDKs. Please add a description of the privacy policy for third-party SDKs in the Privacy Policy, as shown below:
China Mobile Certification
Type of personal information processed : network type, network address, operator type, local phone number information, SIM card status, mobile phone device type, mobile phone operating system, hardware manufacturer
Purpose and use : Quick login/number verification of the identification phone number of the user, problem query, analysis, risk control
Information processing mode : SDK self collection
Third party subject : China Mobile Internet Co., Ltd
Privacy Policy : https://wap.cmpassport.com/resources/html/contract2.html
China Unicom Certification
Type of personal information processed : network type, network address, operator type, local mobile phone number, mobile phone device type, mobile phone operating system, hardware manufacturer
Purpose and use : Quick login/business risk control for identifying the phone number of the user
Information processing mode : SDK self collection
Third party subject : China United Network Communications Co., Ltd
Privacy Policy : https://msv6.wosms.cn/html/oauth/protocol2.html
China Telecom Certification
Type of personal information processed : international mobile subscriber identity code, application process information, ANDROID_ID (optional, except for versions above V3.8.10), registered mobile phone number, local phone number, network connection type, network status information, network address, operator type, mobile phone device type, mobile phone device manufacturer, mobile phone operating system type and version
Purpose and use : Quick login/number verification and business risk control of the mobile phone number identifying the user
Information processing mode : SDK self collection
Third party subject : Tianyi Digital Life Technology Co., Ltd
Privacy Policy : https://e.189.cn/sdk/agreement/show.do?order=2&type=main&appKey=&hidetop=&isShowPre=&returnUrl=https%3A%2F%2Fe.189.cn
Volcano engine API
Type of personal information processed : Mobile phone number, IP
Purpose and purpose : Provide end-user risk identification service
Third party subject : Beijing Volcano Engine Technology Co., Ltd
Handling method : API interface
Privacy Policy : https://www.volcengine.com/docs/6504/166009
Please note that the third-party SDK may change the information processing due to version upgrade and other reasons. The specific information is subject to its official publicity. Please pay attention in time.
Application self starting switch control interface
Supported versions
Start supporting version: JCore v4.2.0
summary
This interface allows developers to control whether the SDK is allowed to self start. SDK self start is mainly used to enable users to complete authentication more timely and effectively, which helps improve application security and user experience. Developers can configure on demand.
Relevant personal information and processing purpose
Software list information (including software list and software operation list information): identify user application environment, improve application security and protect user account security.
Interface definition
public static void enableAutoWakeup(Context context, boolean enable);
public static void enableAutoWakeup (Context context, boolean enable) ;
This code block is displayed in the floating window
Parameter Description
- Context: application context
- Enable: Whether to enable auto start
instructions
- Before SDK initialization, configure the auto start switch through this interface
- SDK self startup status is enabled by default
For example:
//Authentication SDK initialization JVerificationInterface.init(); //Close SDK self startup JCollectionAuth.enableAutoWakeup(context, false);
JVerificationInterface. init (); JCollectionAuth.enableAutoWakeup(context, false );
This code block is displayed in the floating window
Privacy protection mechanism
If you have any questions, comments and suggestions on the permissions of the Aurora security certification SDK, or need the assistance of Aurora to turn off a certain permission collection capability, you can contact us through the following contact information:
- E-mail: support@jiguang.cn
- Tel: 400-888-2376
- Address: No. 6, Keji South 12th Road, High tech Industrial Park, Nanshan District, Shenzhen
You can also access Aurora official website The online customer service system will contact us, and we will provide you with advice and services in a timely manner to ensure the implementation and implementation of the privacy protection mechanism.