Application firewall
-
Product Overview -
Product Functions -
Product advantages -
Application scenarios -
Related products
Product Overview
The web security protection provided for users can effectively protect against various web attacks, help users customize access rules, and improve the security of websites and other businesses. The original new WAF technical architecture system can flexibly deploy WAF instances at various web service portals, avoiding the embarrassment of hackers bypassing the agent to attack the source station under the traditional cloud WAF architecture. The integration of cloud security big data capabilities also enables WAF to help customers improve website security and availability more effectively and quickly.
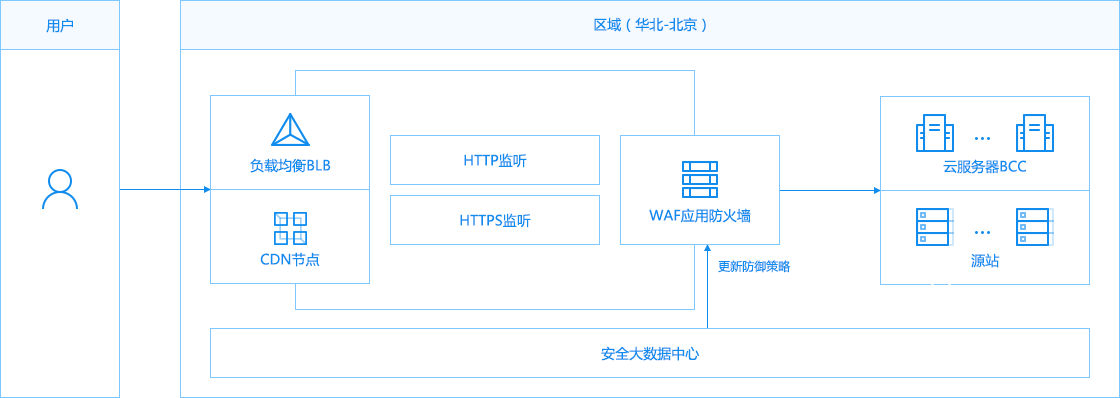
Product Functions
Protect against common web attack threats It provides HTTP/HTTPS services with SQL injection, XSS cross site, web shell upload, unauthorized access and other web service attack protection functions. Quick update of high-risk 0day vulnerabilities Security operation experts will quickly obtain various 0day vulnerability information, timely update the rule base of the Web application firewall, and reduce the impact of 0day vulnerability attacks. Support bypass observation mode Set the bypass observation mode to record attacks without blocking them. Customers can easily evaluate the operation of various rules such as the general definition in the actual business. Accurate access control Users can combine and match multiple HTTP fields to form their own business and other customized rules, which support simple logic syntax.
Product advantages
Unique innovative cloud architecture
Easier to use
The rules and policies are accurate and effective
Event traceability
Application scenarios
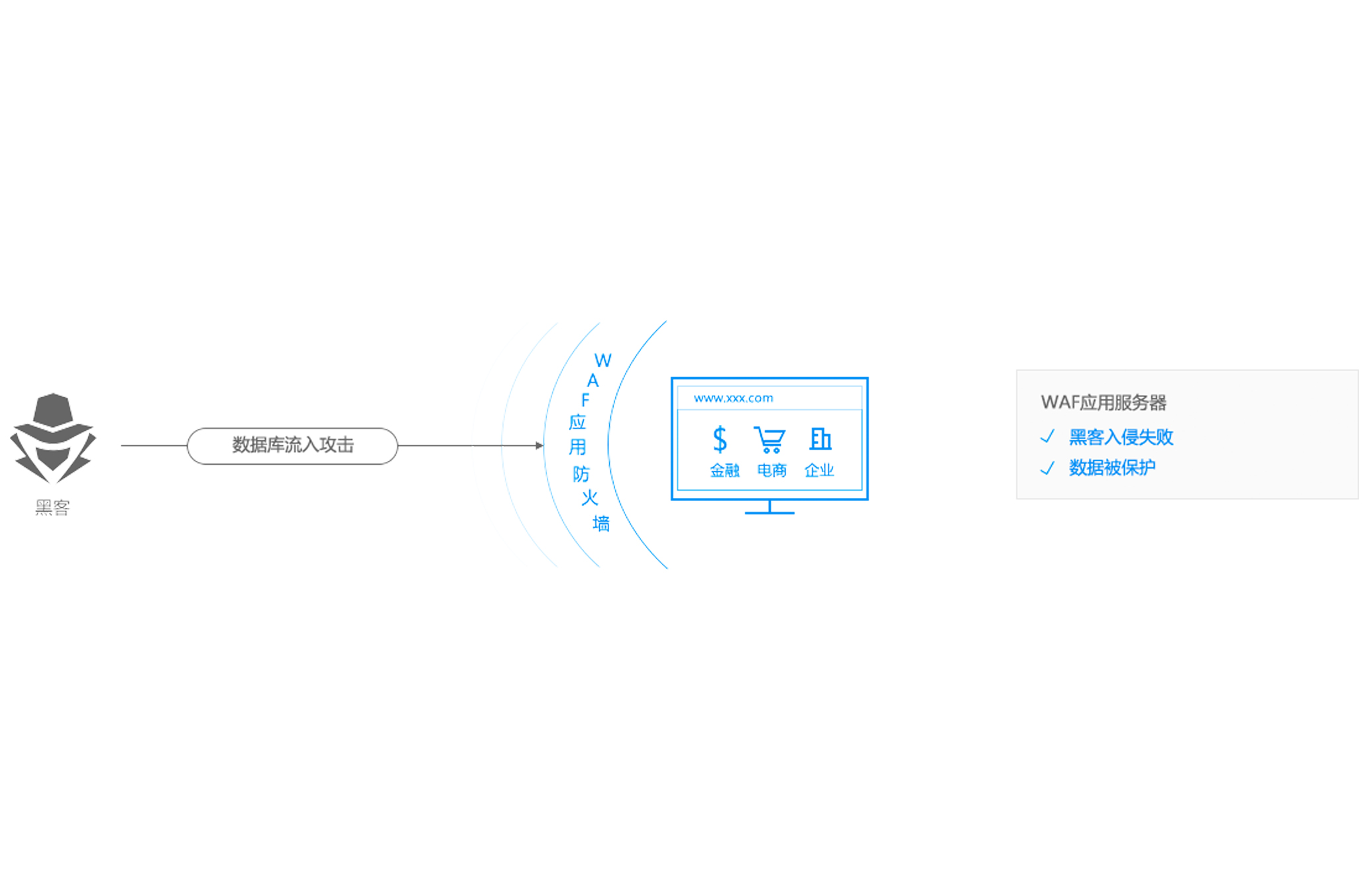
Anti data theft
Application value