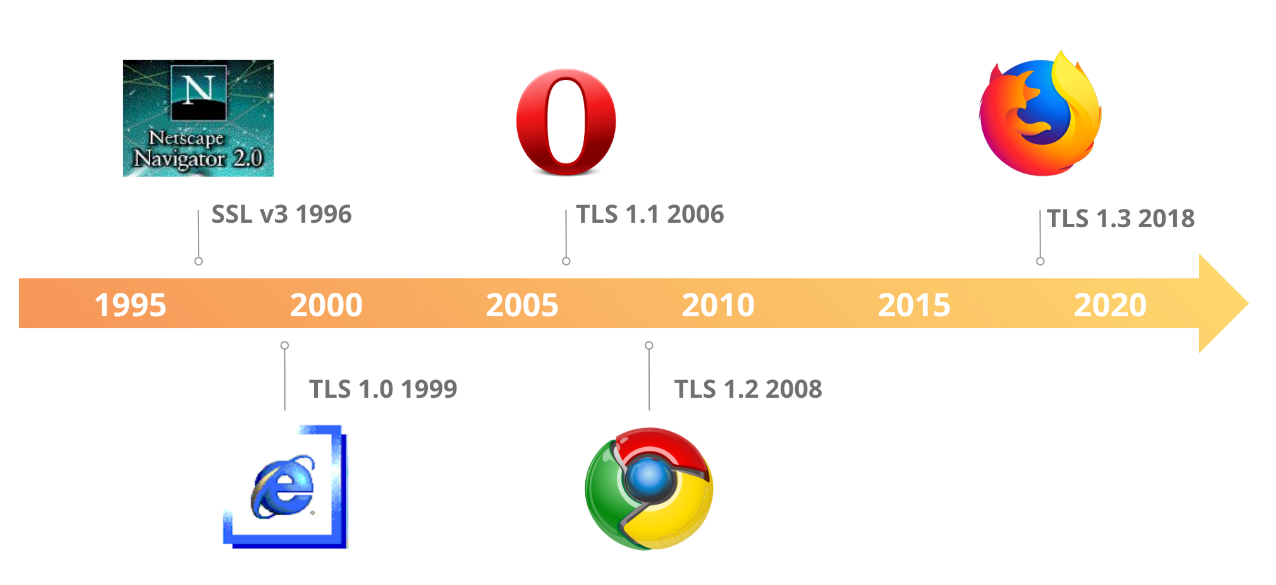
At Yahoo, our users receive and send billions of emails every day. For our hundreds of millions of users around the world, we are committed to making Yahoo Mail easier to use, more personalized, and more secure. In order to meet the requirements of protecting user data, recently, our security team