What is the role of anti-virus software? I often have such questions. Antivirus? Blocking and binding? Game acceleration? Software Assistant? Advertising push? For me, the last three items always make me sneer at some manufacturers.
"Focus, purity, more security" is the slogan given by the Huorong development team on the official website, which also makes me believe it Lightweight, no jamming, high technology Reasons. But the hard work and trouble of the last two weeks finally made me uninstall the tinder software that I have used for more than two years and change back to a big number company.
Light and useless?
The most important function of an anti-virus software is "anti-virus". Unfortunately, I was disappointed by the tinder that I had been lying under the taskbar for two years, and I suffered some losses as a result.
Problem recurrence
There was no record of this event two weeks ago. At this time, only Simulated reproduction Question.
First, I installed the latest version of tinder security software (2017.12.07/sysdiag-full-4.0.44.2).

The reason is that I accidentally deleted the project backup file due to some bug handling errors. The solution is simple: I did not continue to write data to the partition after the error occurred, and data recovery is theoretically feasible. I happened to see the "Power Data Recovery 7.0" recommended by Brother Duck on Bluedot, and I downloaded a copy of it.
although When the download is completed, the tinder file monitoring does not report the virus , but according to the usual usage habits, I still open the velvet and Manual scanning The file, Firevelvet, tells me that this thing is safe and has no problems.
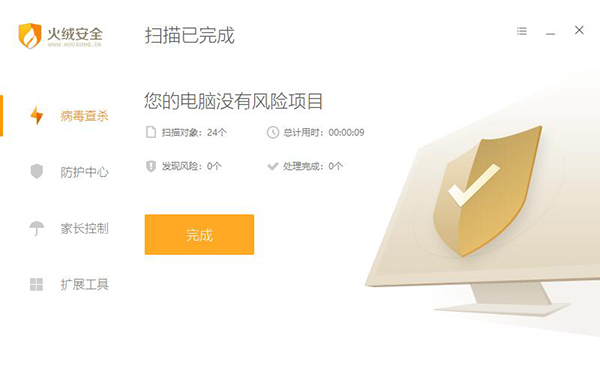
This software passed the detection of tinder. Because I have great trust in tinder, the next step is to decompress it. Yes, the tinder did not report poison during operation.
PS: Since I can't do another poison test with the real machine, there is no diagram for this step.
The file recovery software finally failed to scan the recoverable files, so there is no way to do it. I rewrite the lost script overnight so as not to delay the progress of the project.
The climax came. Three days later, I copied part of the project to the mobile hard disk for testing as planned. Once the hard disk is plugged in, Windows Defender will report virus crazily , prompt that the notification bar is filled instantly. The test made a quick decision and pulled down the hard disk. I wonder why I reported the drug? Test: "(# insidious)".
When I returned to my work station, I turned off the tinder software in the lower right corner and started Windows Defender. In an instant, crazy virus prompts poured out. System32、Program、Document……, Almost all directories are reported to be infected, and a large number of dlls and exes are infected.
I still remember my dear tinder telling me: Honey, I scanned it, and it's OK if I'm here~
At this time, the computer was terminally ill. Windows Defender failed to scan and delete the virus for many times. The virus was still infecting exe and dll. After four hours of rescue failed, I backed up the uninfected work data, completely formatted and reinstalled the Windows operating system. At this time, the four mobile hard disks (1T, 500G, 500G, 320G) and two U disks (32G, 16G) I used to save data are still waiting for processing.
This is the result of a large number of scans of this file
Because there are too many data to be processed, it took me two weeks to process them. In this process, I used Windows Defender, Big Digital Family Bucket, Little Red Umbrella and Kaspersky to scan and clean them twice. After confirming that there were no problems, I finally resumed my normal work.
The following figure shows some strange things in the second scan of some logs of my personal data disk by large numbers.
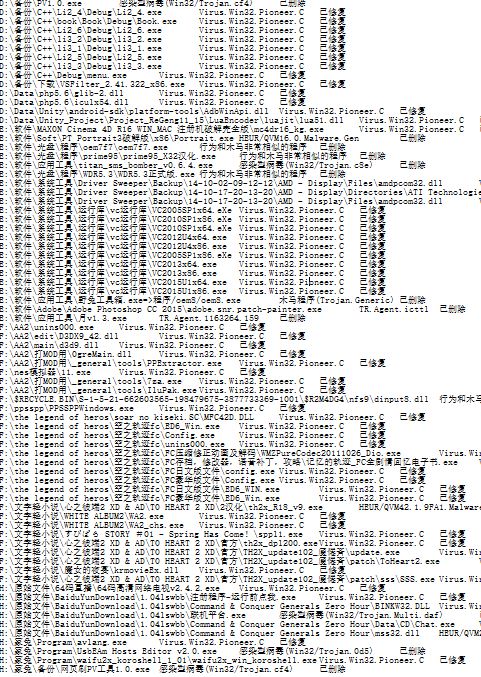
I made a special check afterwards, As early as 2012 The contaminated software was discovered and reported by Kafan Forum. At that time, Tencent's computer steward even published an article entitled《 Multiple download websites of Trojan latent data recovery software were shot 》Security announcements for. As a friendly reminder, it is now 2017 。
Postscript
Through this incident, I have come to the conclusion that tinder is not reliable.
Although Zhihu er people hold this software as high as God, my experience proves that the belief of some tinder brains is a joke. Yes, it refers to myself who installs tinder on all computers in my family.
I am still trying to recover from the storm, and the data lost before has not been completely recovered. However, looking at the two 360 icons lying quietly in the lower right corner, I felt a sense of peace. (PS: 360 Please give me the advertising fee)
Supplementary Notes (September 19, 2018)
This article has been published for nearly 10 months, and I have received many comments.
I will hang some tinder brain powder here without naming names, or the water army that tinder paid for.
-
“ You can't say that it's not good at a certain exam, just that it's not good at learning. ”
Reply: First of all, I have to praise your writing style: it is not easy to use the rhetoric of "analogy". Secondly, it took 5 years for a person to kill the virus, but he didn't learn how to kill the virus. His learning ability is really strong.
-
“ Do you know its principle? Do you know the bottom of it? You have no right to call it garbage. ”
Reply: I can't refrigerate yet, but Gree's air conditioner is really rubbish. Besides, I have already caused losses, but I stopped losing in time.
-
“ If you don't understand anything, just spray it. It's no wonder that anti-virus software can identify any virus for the time being. The focus of anti-virus special diagnosis of various anti-virus software is different. Viruses are specially designed for your anti-virus software to avoid killing. 360 is also a urine type. How many times have you been exempted from killing. ”
Reply: 12 years of virus, 5 years of time, still "temporarily unrecognized", you really understand. According to your statement, we can infer that this vulnerability has not been repaired in 5 years. In this way, I think it's really reliable.
I am willing to accept any objection, because people always have different ideas. However, you dare not leave your real name and email address. According to the regulations on recording user identity in the Regulations on the Management of Internet Post Comment Service, your comments cannot be displayed at the front desk.






