As long as it is published on the network, no information can guarantee security. Give me a express bill to restore 99% of you.
When you open your mobile phone, there are only a few apps in common use, such as a letter, a blog, a treasure, a payment, and a cloud music.
They hold positions in different fields under the name of each family, seemingly unrelated, and also have password gatekeepers.
After all, I haven't disclosed my personal information about my identity in the virtual world. What can be unsafe?
Is that true? Use an ordinary express bill today to see how many percent of you can be restored.
Let's see a netizen's self description:
1: I got a complete express bill from my little partner.

From this express bill, we can quickly give the preliminary impression of the characters: XX Rui XX, a student of XX College of XX University in Jilin Province, bought stationery.
The information you can get from the express bill is:
Mobile phone number............ √
Name (authenticity undetermined)?
Address (identifiable region+occupation)............ √
Purchase items............ √
2: As long as there is a mobile phone number, this person is basically in a "streaking" state in the Internet world.
Open the transfer function of a treasure, enter the mobile phone number, and the real name will be exposed.
Because it is searched by mobile phone number, the corresponding second account displays another mobile phone number, and the name is also different from that on the express bill.
They have the same account and different mobile phone numbers. It is speculated that they may be family members.
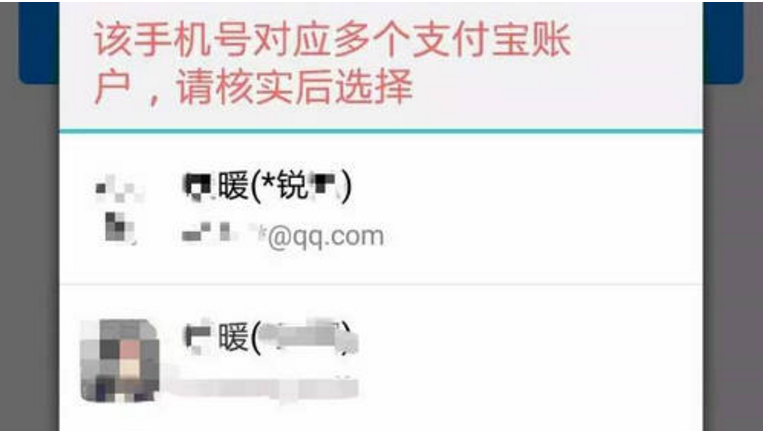
As a result, you can easily get another phone number closely related to the owner.
To tell the truth, the information protection done by a treasure is not up to standard. The whole name is completely exposed. It is almost useless if it is used.
At this point, we got an important message: nickname. This information will be of great use in social media research.
The information you can get from a treasure is:
Mobile phone number............ √
Real name............ √
Nickname............ √
3: No matter which search engine, as long as you simply input keywords, you can get a lot of information.
After basic exclusion, I searched with "name+school" and got more information about XNuan

Silly children write so detailed information...
School association+position............ √
Grade+major............ √
4: First, save the mobile phone number in the mobile phone. Through direct search or mobile phone contact, you can quickly search the social account bound to the mobile phone.
By default, "I can be searched by phone number" in social media applications is enabled.

All on by default
Now, we have basically entered the social circle of XNuan.
With QQ number, you can easily enter QQ space. For those who have been online for a long time, QQ space is a Pandora's box loaded with "black history".
When I was young and ignorant, who hasn't written a few articles about nostalgia
What's more, many people regard QQ space as a place to record their major events and growth trajectory (especially the post-90s and post-00s generation)
Unconsciously reveal key information related to your identity.
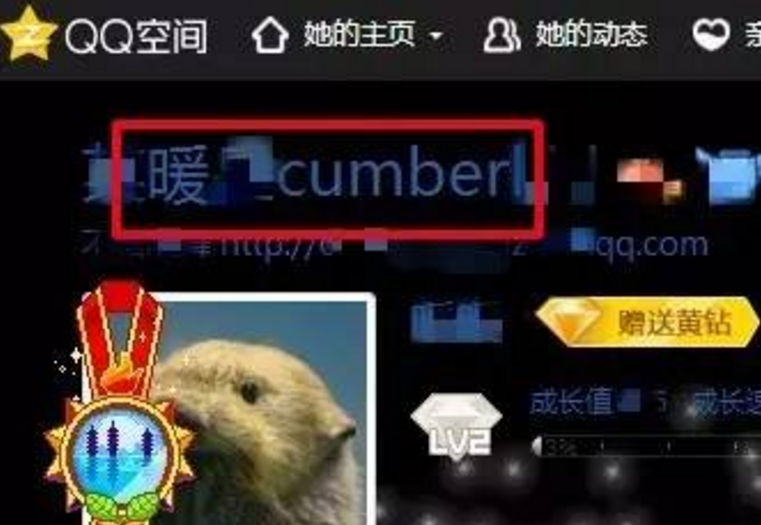
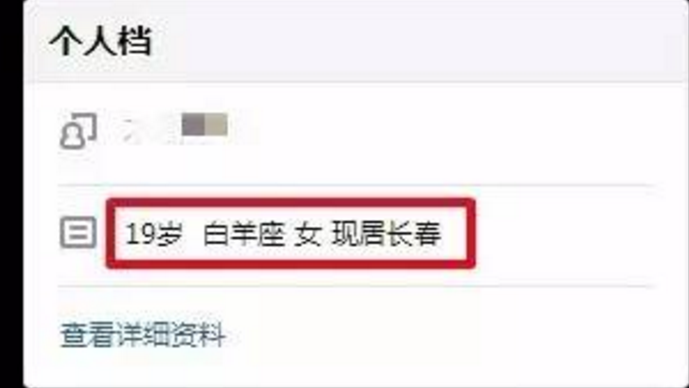
Even if it is better to keep your information confidential, you can still get information about school, residence, age, habits, interests, etc. through visitor records and likes.
Looking around at the photo album, I found that most of the photos in the album were about the book, and I often posted my hand accounts, film ticket stubs, and participated in the translation work of the subtitle group.
At this point, the identity of the student XNuan began to be clear:
Gender............ √
Mobile phone model............ √
Idol scroll (useful later)............ √
Hobbies............ √
Mobile phone model............ √
The same goes for WeChat.
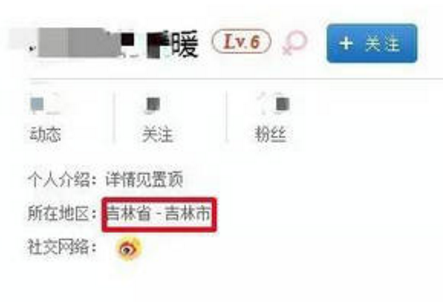
5: Next, combined with the information obtained above, try to find this person on other APPs.
In order to facilitate the presentation, I selected several popular communities among college students: a blog, a cloud music, and a petal.
6: The last step is to use technical means to find out that she has also registered the following websites with her mobile phone number
Recent videos............ √
Recent video posts...... √
Recently booked hotel............ √
Tell me, is there anything you want to search but can't find? (Stalker)
After I had done the manual human flesh once, I felt that privacy exposure was no longer an unreachable news headline
So I expressed my eagerness to "pay attention to the protection of online privacy" with my friends around me
However, I got such a reply: "Well, I'm not a big shot. Will someone search me like this..."
Well, let's imagine that if this "little guy" X Nuan receives a phone call one day:
Hello, Xu Rui? I am the new academic assistant of XXX College of XXX University. Now the school wants to select some sophomores who like movies
To participate in a film festival contest held by the school, we know that you have contacted the new media before, and it is also the teacher of the school newspaper who recommended you to us
If you are willing to come, would you like to add a group first and then we can communicate specifically? You may have to pay a little training fee, just a few movie tickets
Wow, it's scary to think about it.
Repeated in the news
"Call the parents to claim that the child is seriously ill, and can accurately tell the school class and other information"
"Three weeks after the birth of a baby, there are WeChat friends who want to pass the promotion of mother and baby products."
"After paying the down payment for the house, the decoration company called her mother-in-law's home"
In fact, it is not so far away from you.
Heartfelt Presenting [Defence]
For the first time, improving self defense awareness is the basic way to protect your privacy and security.
Think carefully about what information you don't want others to know and how you can get it?
Generally, it is your most commonly used account, your mobile phone number, your address, ID card, etc.
Sort out how many accounts you have registered on different platforms, whether you remember your password, and how long you haven't logged in.
Try to find out how many things through your mobile phone number, email account, and commonly used nickname. Then we should follow the principle of "deleting when you can, and hiding when you can".
The information protection of QQ/a letter/a blog is relatively simple, which is nothing more than adding permissions, relevance, space and deleting dynamics.
If you do a good job in the first step, it will be safe as long as you turn off the phone address book association.
In this way, even if you know your mobile phone number, you can't search common social accounts through association.
Don't use a nickname all over the network. It's easy for others to search your number when they know your nickname.
Don't use one password for the whole network, so if any website is taken off the database, all websites you register are in danger.
The most important thing is to delete or add permissions to the real information you publish on the network.
If you are in need of work, you must disclose your personal information, or you just want to make friends.
It is completely possible to forge a new identity, but it is better not to have any possible connection with your real identity.
Social software can't be completely avoided in modern society. People should not feel that their information will be safe as long as they don't add strangers.
Remember this sentence: as long as it is published on the network, no information can guarantee security.
Excerpt from a website, please leave a message to inform if infringement occurs.













