concept
SSH tunnels can be roughly divided into three types: local port forwarding, remote port forwarding, and dynamic port forwarding. This article will let you thoroughly understand the command expressions of these three forwarding, so that you can flexibly use them to solve various special situations in life.
If you are using tools such as mobaxterm, xshell, secureCRT, and putty, you can use them by simply configuring the visual interface directly. If you do not use tools, you can directly tunnel through commands through this tutorial.
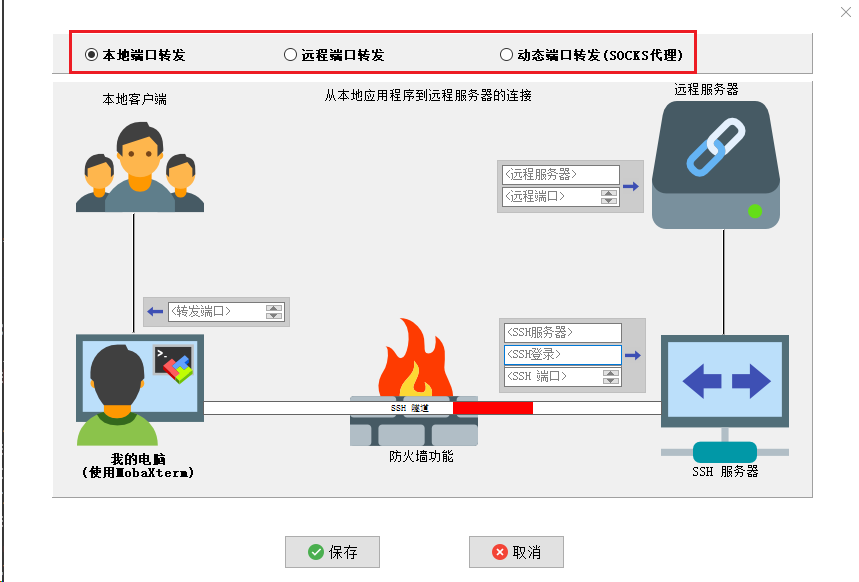
Application scenarios
For some enterprises or individuals, only ssh is allowed to log in to the bastion machine or the machine allowed by the firewall to access some internal services for security. It is mainly used to encrypt the communication data between the SSH client end and the SSH server end, and break through the firewall restrictions to complete some TCP connections that could not be established before.
For example, an Internet user needs to access the company's intranet server. The server does not provide external services, but for management needs, an ssh mapping port is opened on the firewall to manage the intranet server. Access to other services on the intranet server cannot be directly accessed. Some existing requirements:
1. A web service that needs to access the intranet server;
2. Access other web services of the intranet through the intranet server;
3. You need to hang an intranet port proxy for use. For example, the SOCK5 proxy traffic used by chat tools is handed over to an agent in the intranet for processing (self compensation).
4. A local temporary web service needs to be temporarily accessed through vps.
5. Break through the firewall to achieve the effect of intranet penetration.
Details of forwarding three ssh secure tunnel ports
1. Local port forwarding
The connection is forwarded from the client host to the SSH server host, and then to the target host port.
Syntax:
Ssh - g - N - L - f [local port]: [remote IP]: [remote port] [ssh account] @ [ssh service IP] - p [ssh service port]
Take a chestnut:
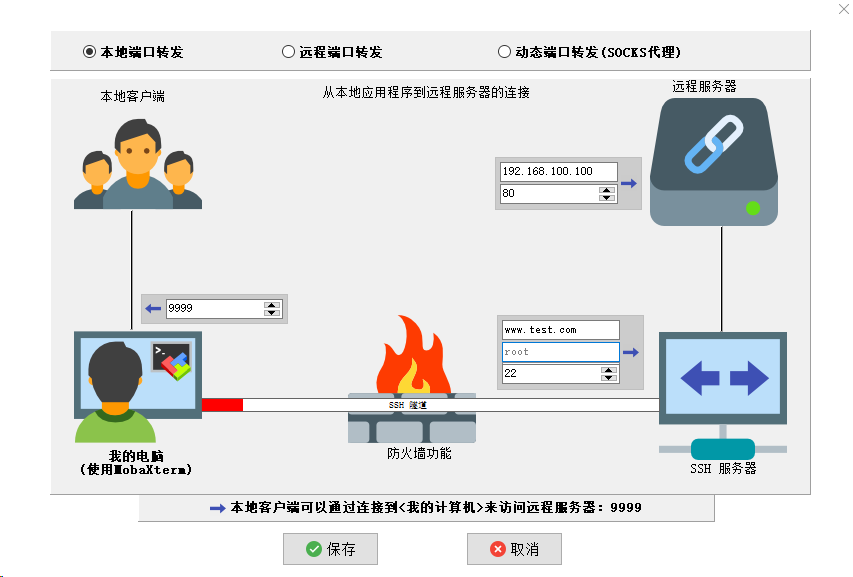
ssh -g -N -L -f 9999:192.168.100.100:80 root@www.test.com -p 22
After entering the command, you can enter the ssh connection password. The above command means, Access the Http://Local IP: 9999 Can directly access the remote machine's http://192.168.100.100:80 The web service.
Parameter description:
-g: Opening the gateway means that all local IP addresses can be accessed;
-N: It means that after the tunnel is created, it is not connected to the ssh server. After the connection, the interface will be blocked directly. If you want to establish the tunnel and connect to the ssh server, you can directly cancel this parameter;
-50: Indicates local, local port forwarding;
-f: It means running in the background. Note that running in the background can only be ended by killing the process
9999:192.168.100.100:80: This indicates [local port 8888]: [remote IP 192.168.100.100]: [80];
root@www.test.com -P 22: Use the root user to connect to the ssh service at www.test.com. The ssh port is 22. If you are not on port 22, you need to modify it;
The above command implements the same functions as mobaxterm:
2. Remote port forwarding
Forwards ports from the server host to the client host, and then to the target host port.
Syntax:
Ssh - g - N - R - f [remote port]: [target machine IP]: [target machine port] [ssh account] @ [ssh service IP] - p [ssh service port]
Take a chestnut:
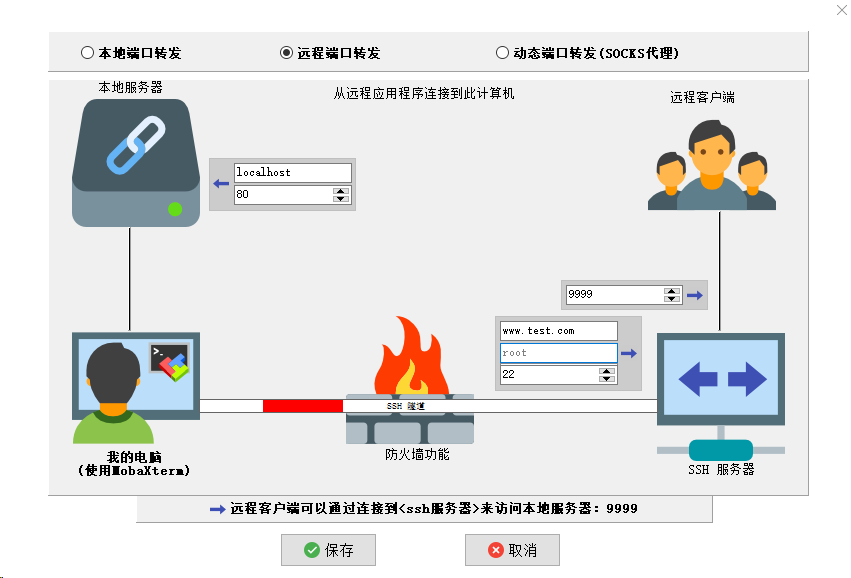
ssh -g -N -R -f 9999:localhost:80 root@www.test.com -p 22
After entering the command, you can enter the ssh connection password. The above command means, Accessing port 9999 of the machine where ssh is located is equivalent to accessing the web service of the target machine's localhost: 80 . Note here that the default ssh will only bind to the 127.0.0.1 switchback address. If you need to bind to all IPs, you need to open them in the sshd configuration file of the remote machine GatewayPorts:on 。
Parameter description:
-g: Opening the gateway means that all local IP addresses can be accessed;
-N: It means that after the tunnel is created, it is not connected to the ssh server. After the connection, the interface will be blocked directly. If you want to establish the tunnel and connect to the ssh server, you can directly cancel this parameter;
-R: Represents remote, which is forwarded by the remote port;
-f: It means running in the background. Note that running in the background can only be ended by killing the process
9999: localhost: 80: This indicates [remote port 9999]: [target IP localhost]: [80];
root@www.test.com -P 22: Use the root user to connect to the ssh service at www.test.com. The ssh port is 22. If you are not on port 22, you need to modify it;
The above command implements the same functions as mobaxterm:
3. Dynamic port forwarding (SOCKS proxy)
Create a SOCKS proxy server that allows communication across multiple ports.
Both local port forwarding and remote port forwarding map a fixed host and its port to the local or remote forwarding port, that is, the application layer protocol represented by the local or remote forwarding port and the target port is a one-to-one relationship. If you need to talk about a chat software, all traffic proxies are handed over to ssh If the remote server is transferring, the ports required by the mapping software one by one are more troublesome. Then we can use the third method of dynamic port forwarding. SSH automatically judges the requests of different protocols for different processing.
Syntax:
Ssh - g - N - D - f [local listening port] [ssh account] @ [ssh service IP] - p [ssh service port]
Take a chestnut:
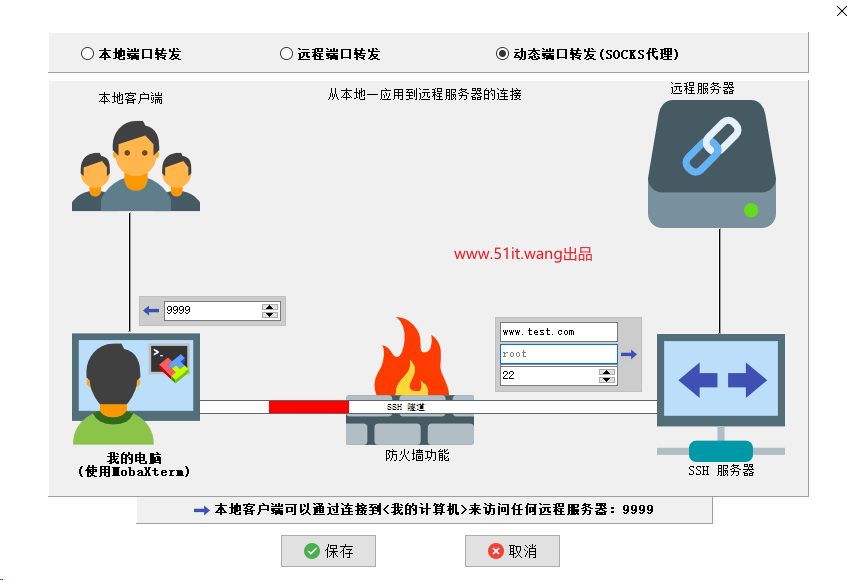
ssh -g -N -D -f 9999 root@www.test.com -p 22
After entering the command, you will be asked to enter the ssh connection password. The above command means that a socks port 9999 will be opened locally for listening. As long as the traffic on this port is proxied, it will be forwarded to the ssh remote server for passing.
When using the proxy, the client needs to set the proxy manually. For example, QQ, WeChat, and tg have corresponding locations to set the proxy. Please explore more interesting things by yourself.
The above command implements the same functions as mobaxterm:
summary
Common parameters and their meanings when creating tunnels are as follows:
"- L option": it means to use local port forwarding to create an ssh tunnel
"- R option": it means to use remote port forwarding to create an ssh tunnel
"- D option": it means to use dynamic port forwarding to create an ssh tunnel
"- N option": it means that you will not connect to the sshServer after creating the tunnel. It is usually used with the "- f" option
"- f option": indicates running the ssh tunnel in the background, usually used with the "- N" option
"- g option": means that the forwarding port corresponding to the ssh tunnel will listen to all IP addresses of the host. If the "- g option" is not used, the forwarding port will only listen to the local loopback address of the host by default. "- g option" means that the gateway mode is enabled. In remote port forwarding, the gateway function cannot be enabled, but only by modifying the GatewayPorts:on The parameter is used to bind all IP addresses.
1. Create local port forwarding command reference:
Ssh - g - N - L - f [local port]: [remote IP]: [remote port] [ssh account] @ [ssh service IP] - p [ssh service port]
2. Create remote port forwarding command reference:
Ssh - g - N - R - f [remote port]: [target machine IP]: [target machine port] [ssh account] @ [ssh service IP] - p [ssh service port]
3. Create dynamic port forwarding command reference:
Ssh - g - N - D - f [local listening port] [ssh account] @ [ssh service IP] - p [ssh service port]
Reference article
SSH tunnel: detailed explanation of port forwarding function
SSH Tunnel Concise Tutorial
Three application scenarios of ssh tunnel and forwarding technology
How to configure SSH port forwarding
SSH port forwarding: ssh tunnel
My blog will be synchronized to the Tencent Cloud Developer Community, inviting everyone to join us: https://cloud.tencent.com/developer/support-plan?invite_code=3vtuwevgbfms4



