For programmers, the most frightening thing is that the server is attacked for no reason. With the gradual increase of network malicious attacks, many websites are troubled. The most common malicious attacks are CC and DDoS attacks. What should we do if the server is attacked? How should we defend against DDoS attacks?
What if the server is attacked?
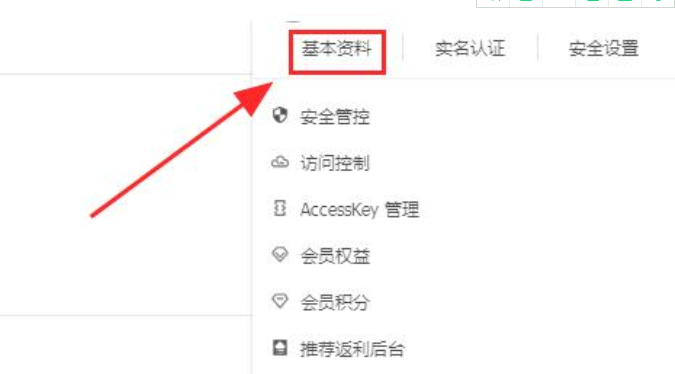
1. Log in to the ECS account management background and click Basic Settings.
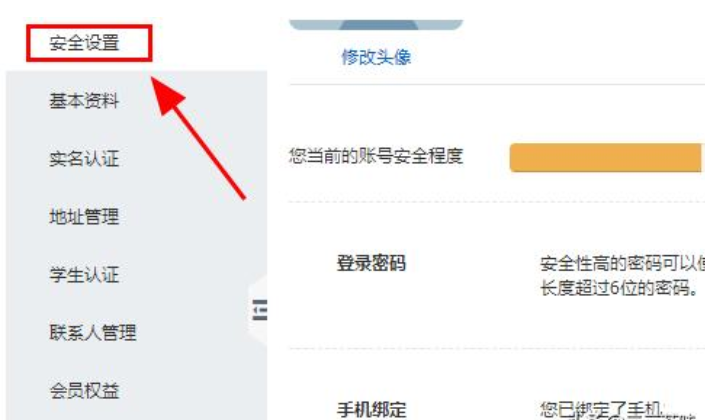
2. Click<Security Settings>in basic settings, and click the modification items behind login password, security issues, etc. to modify the account login password to prevent an attack account from logging into ECS.
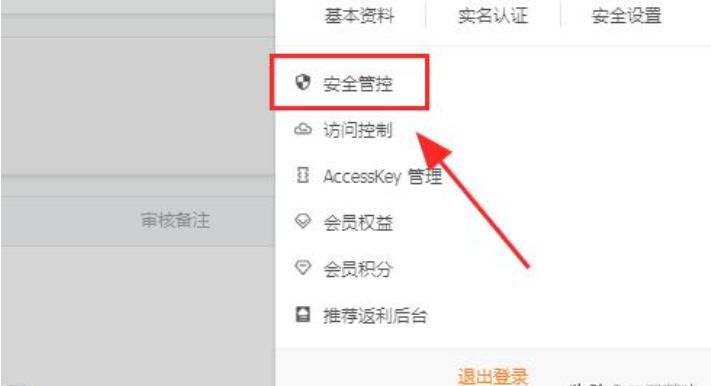
3. Click Security Control in the management menu.
4. Enter the ECS security management page, click and click Open Detection to detect viruses, trojans and other dangers.
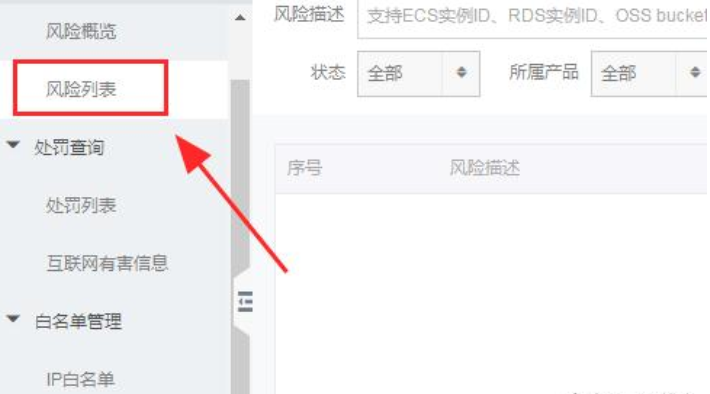
5. After testing, click the risk list on the right to process the detected viruses and trojans.
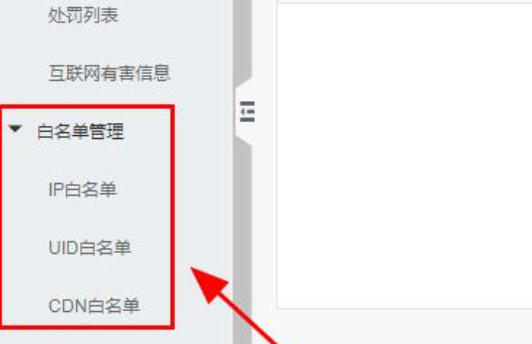
6. After processing, click<Whitelist Management>to add the IP address, CDN, etc. that allow viewing server information to the whitelist, and isolate the attacker's IP address.
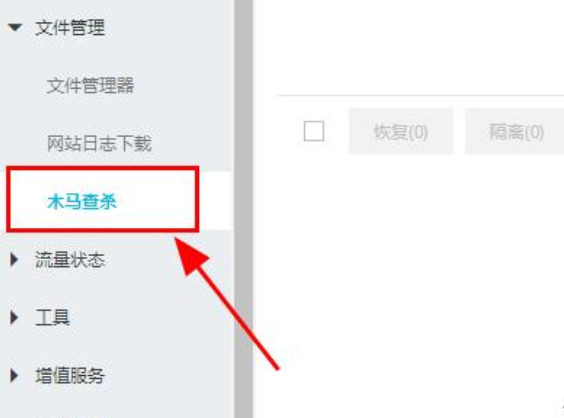
7. Then enter the cloud server management console, click<Trojan>Check and Kill to check and kill the server Trojan virus, and deal with the attack of the cloud service.
How should the server defend against DDoS attacks?
1. Ensure that all servers adopt the latest system and apply security patches. The Computer Emergency Response Coordination Center found that almost every DDoS attacked system has not been patched in time.
2. Ensure that the administrator checks all hosts, not just critical hosts.
3. Ensure that unused services such as FTP or NFS are deleted from the corresponding directory or file database of the server.
4. Ensure that all services running on Unix have TCP wrappers to restrict access to the host.
5. It is restricted to sharing with network files outside the firewall. This will give hackers a chance to intercept the system file and replace it with a Trojan horse. The file transfer function will be paralyzed.
6. Make sure you have an up-to-date network topology map on hand. This diagram should indicate the TCP/IP address, host, router and other network equipment in detail, and should also include the network boundary, the demilitarized zone (DMZ) and the internal security part of the network.
7. Run the port mapper or port scanner on the firewall. Most events are caused by improper firewall configuration, which makes DoS/DDoS attacks have a high success rate. Therefore, you must carefully check the privileged ports and non privileged ports.
It is common for network servers to be attacked in recent years. Although it is not surprising, once it happens, there will be losses, which is inevitable. Therefore, it is necessary to take precautions.