Security is the primary consideration of virtual hosts, because only secure virtual hosts can ensure the normal and stable operation of the supported sites? Is your virtual hosting scheme secure enough?
Can your virtual host scheme monitor servers throughout the process?
Can your virtual hosting scheme prevent spam?
Can your virtual host scheme set a firewall to strictly control data flow?
Your virtual host scheme supports Fail2ban Does it prevent violent attacks?
Does your virtual host scheme have complete backup and recovery functions?
If you use the next-generation virtual host solution, the answer above will be yes, because it is equipped with a professional, versatile management system - Plesk , which guarantees the absolute security of the virtual host.
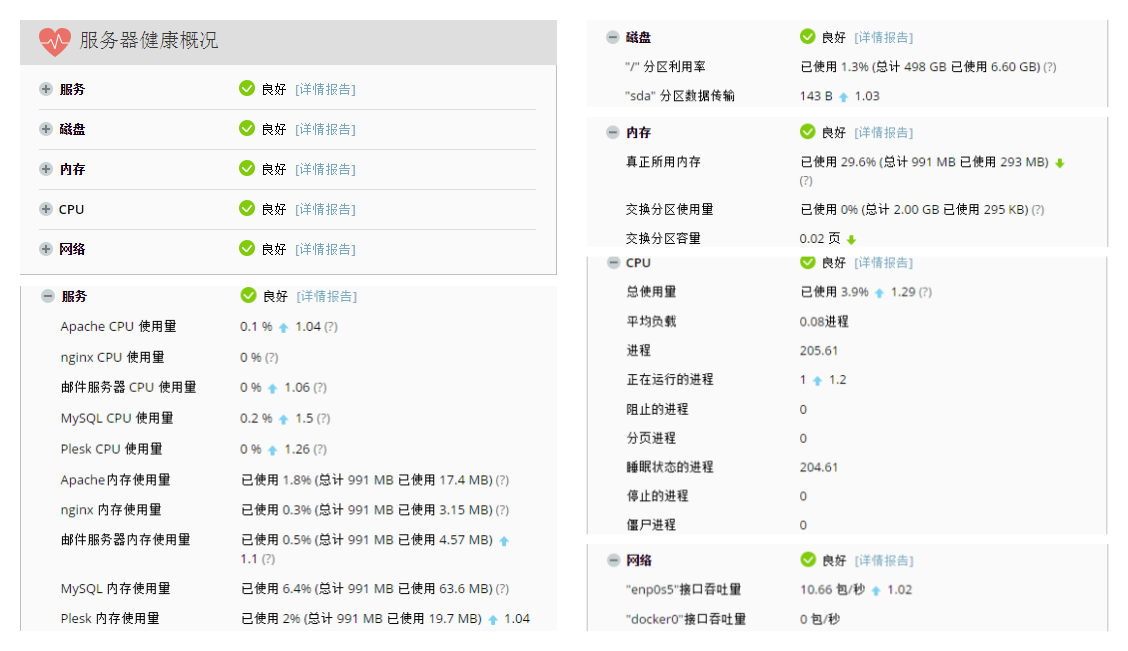
Whole process monitoring server
Next generation virtual host configuration Plesk The host panel, which has a built-in server health monitor, can monitor all aspects of the server (including services, disks, memory CPU And network) 7x24 It will monitor around the clock and analyze the current status of each project (as shown in the figure below). If any abnormality is found, it will be reported immediately. In addition, Plesk It also supports viewing server related information through the mobile terminal and performing some necessary operations.
Comprehensive prevention and control of spam
adopt Plesk Enable DMARC 、 DKIM 、 SPF 、 DNS blackhole lists Such strategies prevent and control spam at all levels. You can set a score to adjust the sensitivity of the spam filter to determine spam, and then deal with spam by marking spam, deleting spam, and moving spam to the spam folder. More importantly, black and white grey lists can also be enabled at the server level to curb the spread of spam at the source. Plesk Also supports popular SpamAssassin Function authority to prevent and control spam.

Strictly control data flow
Plesk It supports enabling or disabling the firewall as required and making corresponding settings to control the incoming and outgoing of each data flow, effectively ensuring the security of the network. stay Plesk After enabling firewall management, you can customize Plesk Firewall rules to allow or deny certain IP Access to address or network information can effectively control the channel of information exchange, fundamentally block the intrusion of some networks with potential security risks, and achieve basic security prevention and control.

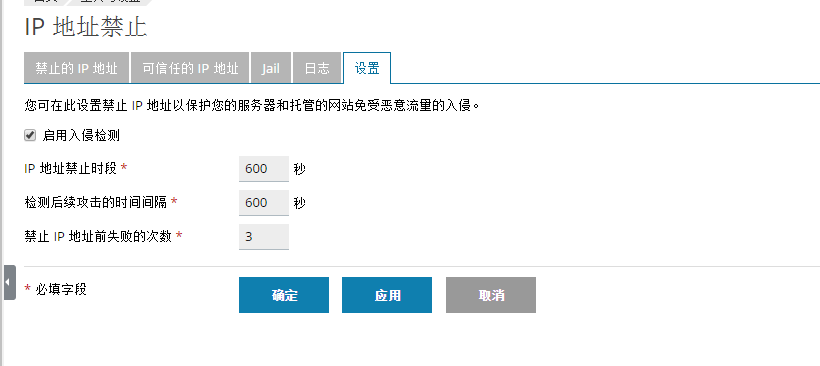
Strictly block malicious traffic
Plesk support Fail2ban Function, which can automatically prevent malicious traffic generated on your server IP Address and network to block violent attacks. Plesk Support for prohibited IP Address, trusted IP Address Jails (including activation, deactivation and addition of new Jails And add new Jails Filters), logs, and related settings( IP Address prohibition period, time interval for detecting subsequent attacks, prohibition IP Address).
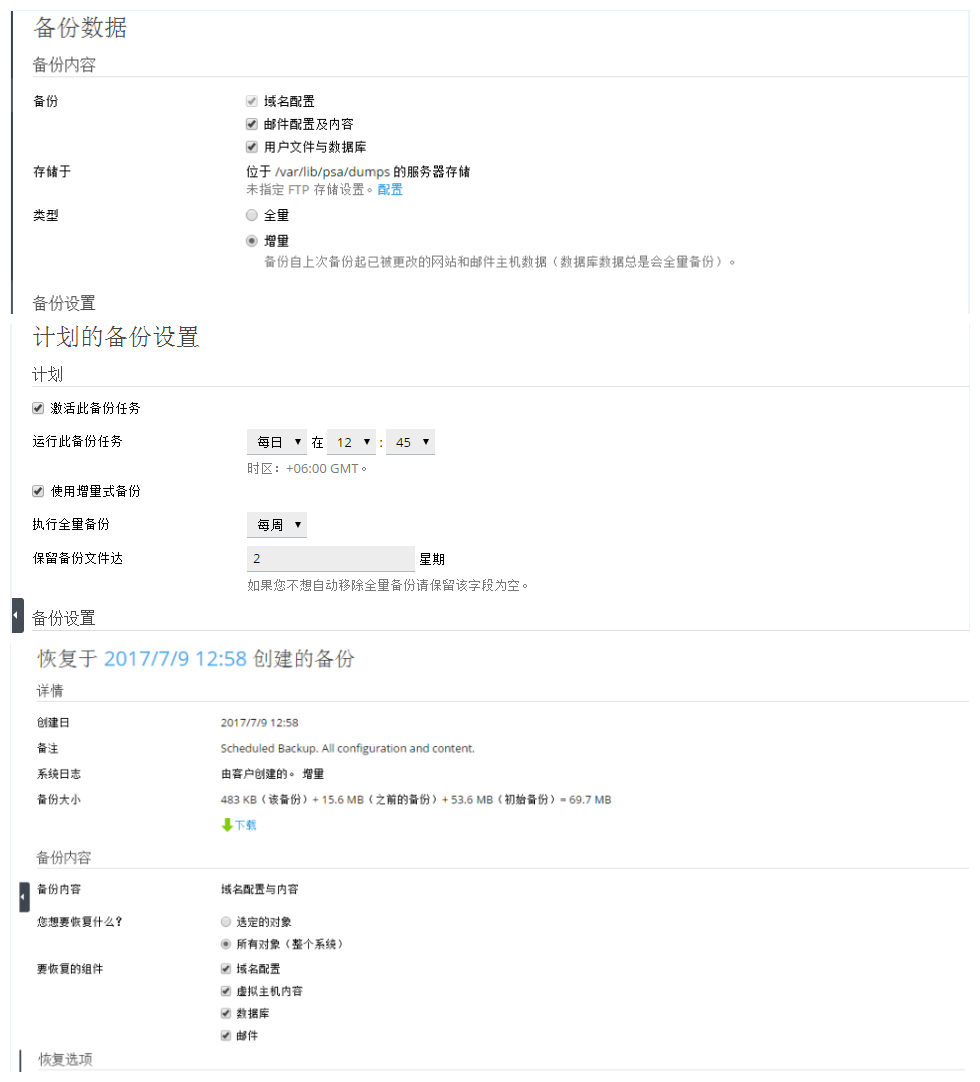
Perfect backup and recovery
Plesk The built-in backup manager supports the backup of data on a single subscription, a single account, and the entire server. Plesk It supports full backup and incremental backup. The first full backup and subsequent incremental backup can not only ensure the continuity and integrity of data, but also save time and space. Plesk support Plesk Servers and FTP Remote server dual storage , Double guarantees. adopt Plesk The backup can also be scheduled and set up in advance. The backup manager will back up on time as required. To restore the backup, select the content to restore and click Restore.
Only the next generation of virtual host that is well protected and controlled in an all-round way can be your trusted and safe virtual host.











