Today, when information security is becoming more and more important, enterprises pay more and more attention to business related data and regard it as the lifeline of enterprises. Yunxin has specially built a set of Privatization scheme , and has been operating stably in many leading enterprises in the industry, becoming a booster for the internal development of enterprises.
This article will explain why enterprises want to do privatization, the architecture of cloud trust privatization, and the deployment, operation and maintenance of cloud trust privatization Privatization of Yunxin Implementation and advantages of.
More technical dry goods, please follow the "Netease Yunxin" public account>>>
Why privatization
Compared with public cloud, privatization has the following advantages:
1. Enterprises have practical and effective control over data and security
Privatization is deployed in the firewall of the enterprise data center, or in a secure host hosting place, without contact with the outside world. All nodes are autonomous and controllable.
2. Controllable service quality
The SLA of the whole service is related to the enterprise's own data center. There is basically no network delay in accessing private services within the enterprise. The SLA is more stable and reliable, and the service experience is better.
3. Make full use of existing hardware resources
The privatization of Yunxin can reuse the existing hardware resources of enterprises. For example, MySQL can be reused for the underlying database and F5 can be reused for load balancing to avoid resource waste and save enterprise costs.
4. Effective interaction with existing systems
Within an enterprise, there will be existing business systems. In the privatization of Yunxin, it can be effectively integrated with common systems of enterprises such as OA and monitoring.
understand Netease Yunxin Private Cloud >>>
Business architecture and security
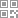
As shown in the figure above, cloud trust privatization is mainly divided into three parts
1. NIM-API server api, used for third-party server calls, can realize message broadcasting, system notification, user addition, deletion and modification and other functions. When calling the server API, you need to specify appkey and secret, and mix encryption to generate specific md5. The server can execute after passing the verification. When the management user has security problems such as secret leakage, you can reset the corresponding secret on the server to effectively avoid illegal API calls.
2. NIM-SDK client SDK, as long as the client integrates the Yunxin privatization SDK, it can use all the functions of Yunxin privatization. The client and the server will then establish a long TCP four layer connection. The interaction content is the private binary transmission protocol of Yunxin, which can ensure stable and secure data transmission and interaction.
3. The management platform Yunxin privatization provides a separate management console. On the management console, enterprise users can dynamically add and modify applications, add service nodes, adjust the configuration related to Yunxin, interface frequency control, and view a series of operational data.
Network architecture
The internal enterprise is generally divided into internal and external networks (DMZ is the internal and external network buffer zone, which is common in enterprises with high security requirements such as banks and military industries). The privatization of Yunxin supports internal network deployment, and IM and audio and video support internal and external network interworking. The network topology is as follows
1. The internal and external network client IM of Yunxin uses different entrances to connect the same set of service clusters, realizing the internal and external network interworking
2. The private audio and video server address of Yunxin sends IM signaling, and the audio and video server cluster will judge the network environment of the client according to the real IP address of the client, and specifically down the intranet or internet address of the audio and video server. This function requires the F5 device (SLB/NGINX in fact) in the figure above to enable the IP transparent transmission function. The audio and video function uses the udp four layer protocol, and the related udp ports need to be opened on the firewall
Installation, operation and maintenance
1. At present, there are many modules involved in the Yunxin product itself. The technical architecture and programming language are different, and the environment and network on which it depends are also different. Therefore, we use docker in the privatization of Yunxin to realize the encapsulation of each module and the isolation of runtime resources. Each service is an independent docker image. On the host, use the supervisor to monitor each docker service. When a service is abnormal, the supervisor will automatically pull up the service again; In the docker image, the supervisor is also used to monitor the business.
2. At the monitoring alarm level, the ELK monitoring platform adopted by the privatization of Yunxin formats and stores logs for users to query and analyze. The elastalert used for alarm can dynamically adjust the alarm rules. When an alarm is triggered, smtp is used to send an alarm email.
For more technical goods, please follow the "Netease Yunxin" public account.
Invite your friends to use Netease Yunxin. If your friends place an order successfully, they can get 1000 yuan of Netease koala/strictly selected threshold free cash coupon, Click to recommend now >>
Learn about Netease Yunxin, communication and video cloud services from Netease core architecture>>
NetEaseYunXin is a PaaS service product integrating NetEase's 20 years of IM and audio and video technology. The communication and video cloud services from NetEase's core technology architecture are stable, easy to use, and have comprehensive functions. It is committed to providing the world's leading technical capabilities and scenario based solutions. Developers can quickly realize functions including IM, audio and video call, live broadcast, on-demand, interactive whiteboard, SMS, etc. by integrating the client SDK and the cloud OPEN API.