Understand the essence of https principle in plain English
I believe many people are not clear about the process of https, but only know that https It is secure encryption. The underlying principle and process are not clear
The author was also right https The process is not clear, and the most annoying thing is that every time you interview, the interviewer is likely to ask you this question
Every time the answer is wrong or the interviewers are not satisfied with the answer, but they still don't really understand
actually https The principle and process of is not so complicated, but some articles do not explain clearly. If you read too many articles like this, you will be confused.
Understanding https Before the principle process, let's learn about encryption
I Encryption knowledge
Encryption can be divided into the following three modes according to the encryption mode
1.1 One way encryption
It is also called irreversible encryption. The encryption of plaintext generates a ciphertext, and the corresponding plaintext cannot be solved through the ciphertext
It is generally used to generate message digest, key encryption, etc. Common one-way encryption includes:
- MD5: I believe everyone is familiar with this. One plaintext corresponds to a unique ciphertext after MD5
- SHA: including sha192 and sha256
characteristic:
- Irreversible
- Same input, same output
1.2 Symmetrical encryption
Symmetric encryption: use a key to encrypt the plaintext. Similarly, the same key can also decrypt the ciphertext
That is to say, encryption and decryption can use the same key
This encryption method is symmetric encryption
Common symmetric encryption methods include:
characteristic:
- The encryption party and the decryption party use the same key
- The speed of encryption and decryption is fast
1.3 Asymmetric encryption
As we know, symmetric encryption uses the same key. On the contrary, asymmetric encryption uses the public key and private key for encryption and decryption
You can use the private key for encryption and the public key for decryption. Similarly, you can also use the public key for encryption and the private key for decryption
Common asymmetric encryption methods include:
What we usually use most is RSA
characteristic:
- Use two keys for encryption and decryption, namely public key and private key
- Public key encryption Private key decryption, private key encryption Public key can decrypt
- Encryption or decryption is very slow
- Private key and public key are paired
II. Summary of encryption knowledge
**One way encryption: * * Irreversible. As long as the input content is the same, the output ciphertext must be the same. If there is any modification, the generated ciphertext will be different
**Symmetric encryption: * * The encryption and decryption use the same key, which is very fast
Asymmetric encryption: Use public key and private key for encryption and decryption, public key encryption private key solution, private key encryption public key solution. The process of encryption and decryption is very slow
A public key is something that can be disclosed to others
The so-called private key is not allowed to be disclosed to others, but is privately reserved.
Note: The above contents are purely encryption knowledge, and https It doesn't matter. Let's begin our explanation https Process. Let's first look at a demand
Once this requirement is solved, we will understand https The process of.
Start with a requirement
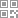
Suppose there is such a demand: Xiaoming and Xiaohua need to communicate. As boys and girls write love letters, they certainly don't want others to see them, so they need safe communication.
Question 1 : How can Xiao Ming safely transmit the content to Xiao Hua?
Through the study of the above encryption knowledge, it is easy for us to think that the communication content should be encrypted
The answer is right. Just encrypt the communication content.
Question 2: Which encryption method is used for encryption?
One way encryption is definitely not good. Xiaohua can't solve the letter after receiving it. This love can't be talked about
Symmetrical encryption can , Xiaohua can solve the content as long as she has the key
Asymmetric encryption can also be used Xiaoming uses his private key for encryption. Xiaohua can get Xiaoming's public key and also solve the content
Question 3: Symmetric encryption and asymmetric encryption can be used. Which one should be used?
Through the study of the above encryption knowledge, we know that
Fast symmetric encryption, slow asymmetric encryption
So for Xiao Ming and Xiao Hua, they often talk for hours, and there are a lot of data
If asymmetric encryption is used, it will be very frustrating, because encryption and decryption are also slow. These two people will certainly not use asymmetric encryption. If I were you, I would not use asymmetric encryption.
The answer is to use symmetric encryption Because the encryption is fast, Xiaoming and Xiaohua all hold the same key, and both parties can decrypt the letter sent by each other.
Conclusion: Xiaoming and Xiaohua communicate using symmetric encryption. If the key is S , both parties use the same key S Encrypt and decrypt
In this way, Xiaoming and Xiaohua can communicate happily, and the content is encrypted. The speed of encryption and decryption is also very fast, which is beautiful.
But there is a hidden danger, that is, the key S , was accidentally intercepted by Lao Wang during the transmission
The result is that Xiao Ming, Xiao Hua and Lao Wang all have the same key S Has
Then, there is no secret between Xiaoming and Xiaohua. Lao Wang can read all the letters they send, encrypt them after reading, and send them to Xiaohua. That's enough.
 Then how to solve
Then how to solve Key S How about being intercepted by others during transmission?
Some people say, yes Symmetric encryption Mode pair Key S After encryption and transmission Key S1 There is also a risk of being intercepted
Then encrypt S1 and transmit it ..., so there is no end. It must be impossible.
The above method must not work. The problem now is: how does Xiao Ming put Key S Pass it to Xiaohua safely. Is this the same as the previous question I How can Xiaoming safely transmit the content to Xiaohua? similar
Therefore, Xiaoming and Xiaohua need to use Symmetric encryption Encrypt and transmit the message content
Then we must first solve a problem: how can Xiao Ming safely handle Key S Transfer to Xiaohua?
Question 4: How can Xiao Ming safely handle Key S Transfer to Xiaohua?
If Key S If the transmission process of is not secure, the subsequent communication is not secure. Otherwise, how to Key S If it can be safely transmitted to Xiaohua, the subsequent communication is secure.
If this is a job that the leader has given us, how can we solve it by using the encryption knowledge we have learned?
Through the study of the above encryption knowledge, is there a secure encryption transmission mode as follows
-
Xiaoming uses asymmetric encryption to communicate. First, Xiaoming generates a pair of private keys and public keys. For convenience, they are called privateKey , publicKey
-
Xiao Ming publicKey Give Xiaohua
-
Method 1: Xiao Ming uses his own privateKey , Yes Key S Encrypted, encrypted ciphertext S0 Transmission to floret, for floret publicKey yes S0 Declassified Key S
-
**Method 2: * * for small flower publicKey yes Key S Encrypted, encrypted ciphertext S0 Transmit to Xiao Ming for Xiao Ming's use privatekey yes S0 Declassified Key S
Above, method one is not feasible, because Xiao Ming's publicKey It is open and can be downloaded by anyone, that is to say, Lao Wang also has Xiao Ming publicKey , or S0 Decrypt it Key S
Method 2 is feasible because privateKey Only Xiaoming has it. Xiaohua uses Xiaoming's public key to encrypt it. Only Xiaoming can unlock it. Nobody else can
So the above solution is:
use Asymmetric encryption Way, right Key S Encrypt and transmit
Some people say, no, Asymmetric encryption The performance is poor. Encryption and decryption are very slow. Otherwise, Xiaoming and Xiaohua can use it directly at the beginning Asymmetric encryption Just communicate
That's right, but we only use Asymmetric encryption yes Key S Encrypt, the data volume is very small, and Key S After safe transmission to the other party
Symmetrical encryption is directly used for subsequent communication, which is more efficient. Asymmetric encryption is just to negotiate how to transmit safely Key S After this phase is completed, it is no longer needed.
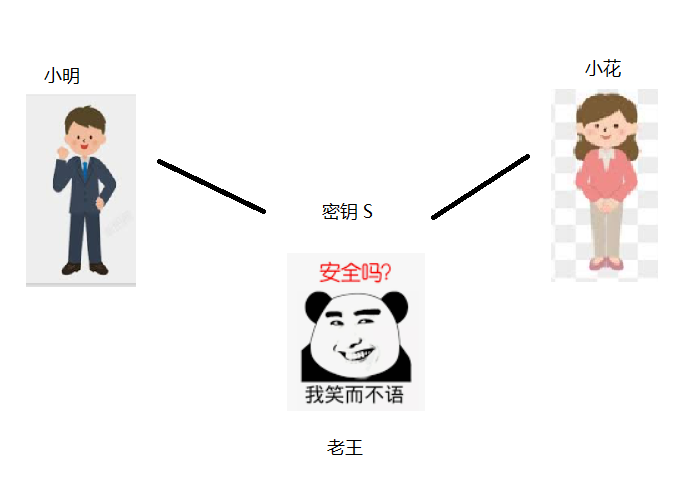
It can be seen from the above that asymmetric encryption has such characteristics
As long as I get the public key of whoever I communicate with, it is safe
For example, if you have a pair of private keys and public keys, I just need to get your public key, and then use your public key to encrypt the transmission content. Only you can unlock it, because only you have the private key
As follows:
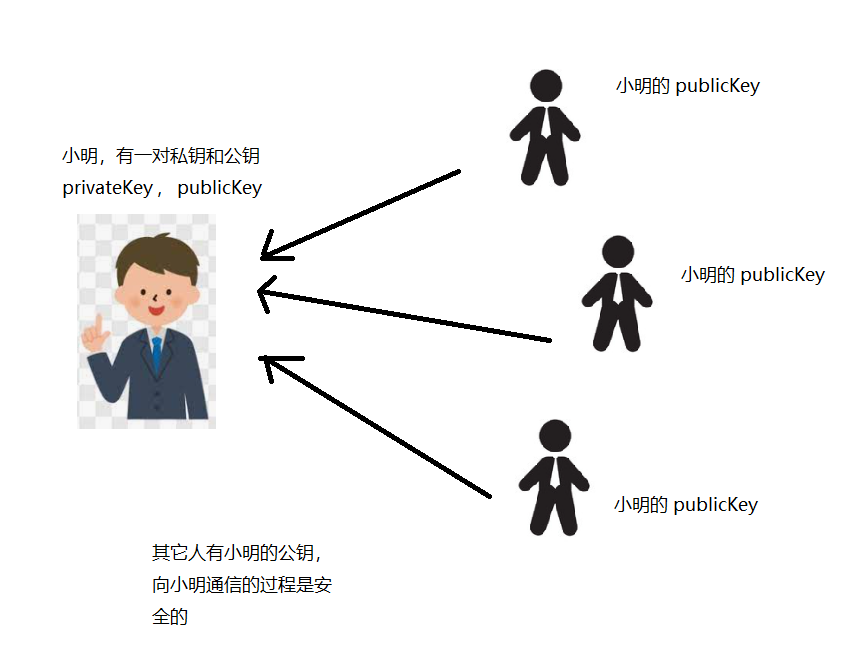 Conversely, Xiao Ming uses his private key to encrypt, while others use Xiao Ming's public key to decrypt. What is the role of this process?
Conversely, Xiao Ming uses his private key to encrypt, while others use Xiao Ming's public key to decrypt. What is the role of this process?
The answer is: identity verification.
As long as Xiao Ming encrypts with his private key, if others can unlock it with Xiao Ming's public key, it proves that this letter must and must be written by Xiao Ming
For example, you need to send a notice, but you must make sure that the notice is sent by you, in order to prevent others from altering it in the middle (for example, the ancient fake imperial edict was not properly verified)
You can use your private key to encrypt the notice. If others want to see it, they can download your public key and decrypt it. It means that the notice must be sent by you.
Because if someone else alters in the middle, but does not have your private key to re encrypt, it will not work.
Conclusion: Through the above description, we have solved several problems through the following processes.
- Xiaoming and Xiaohua use encryption to encrypt the content for secure communication
- Compare and contrast, you can only choose
Symmetric encryption This encryption mode is used to encrypt and transmit the content
- But symmetric encryption
Key S The transmission process is insecure and easy to be stolen by Lao Wang. What should we do
- Xiaoming thought of it
Asymmetric encryption Then a pair of private keys and public keys are generated and given to Xiaohua
- Xiaohua uses the public key to
Key S Encrypt and send it to Xiao Ming
- Because it is encrypted with Xiaoming's public key, and because only Xiaoming has the private key, only Xiaoming can decrypt it. Even if Lao Wang intercepted the ciphertext in this process, he could not decrypt it
- In this way, Xiao Ming decrypted it with his private key
Key S
- At this time, Xiaoming and Xiaohua use symmetric encryption,
Key S , have a pleasant communication, such as discussing the amount of betrothal gifts, where to hold the banquet and where to spend the honeymoon
- In this way, the communication process is safe.
The above process is perfect, but the way is high and the devil is high. Lao Wang is very clever, and he has another idea
Since you two use Asymmetric encryption If I can't decrypt the ciphertext after intercepting it, I'll change it.
If Xiaohua has a problem in obtaining Xiaoming's public key, for example, what Xiaohua obtained is not Xiaoming's public key, and what about Lao Wang's public key (Xiaohua still thinks Xiaoming's public key is)
What will happen? First, take a look at the following figure (the so-called man in the middle attack)
 According to the above figure, Lao Wang, also known as the man in the middle, is the man in the middle attack. The process is as follows:
According to the above figure, Lao Wang, also known as the man in the middle, is the man in the middle attack. The process is as follows:
-
In the process of obtaining Xiaoming's public key, Xiaohua was given the package by Lao Wang and became her own public key, which was sent to Xiaohua
-
Xiaohua mistakenly thinks that the public key in her hand is Xiaoming's (in fact, it is Lao Wang's public key), so she uses Lao Wang's public key to Key S Encrypt to get Ciphertext S0
-
Ciphertext S0 In the process of sending it to Xiao Ming, Lao Wang intercepted it, and Lao Wang decrypted it with his private key Key S
-
Lao Wang got Key S After that, back up a copy yourself, and then Key S , use Xiao Ming's public key to encrypt, and get Cryptogram S1 , sent to Xiao Ming
-
Xiao Ming gets Cryptogram S1 After decryption, use your own private key to get Key S
-
Later, Xiaoming and Xiaohua will use symmetric encryption, Key S Communicated
-
They thought it was safe. In fact, Lao Wang had already read the content of the communication. Still unsafe
Ah ah ah, it's crazy. For the sake of communication security, we encrypt, but the encrypted key transmission is not secure
For the security of key transmission, we produced a private key public key pair, gave the public key to Xiaohua, and Xiaohua encrypted the key with the public key for retransmission
In this way, only Xiao Ming can decrypt. Unexpectedly, the public key transmission is unsafe.
It's hard to fall in love, Lao Wang. What are you doing...
If something goes wrong, it must be solved. Now it is the process of transferring the public key, and it is not safe
This and the above questions How to transmit the content of the letter to the other party safely? as well as How to securely transmit the key to the other party? Is similar
Now the question is: How to securely transmit the public key to the other party?
I feel that I have entered an endless cycle, no matter how Content of the letter Secure transmission, or secret key Secure transmission, or Public key security Secure transmission
They are similar in nature, but the transmission is different and the methods used are different
Question 5: How does Xiao Ming safely transfer his public key to Xiao Hua
We can know from the problems we solved above
- How to safely transmit the communication content to the other party?
Solution: We use symmetric encryption to communicate
-
How to safely handle Key S Secure transmission to the other party?
Solution: Asymmetric encryption is adopted, and Xiao Ming gives his public key to Xiao Hua
Xiaohua uses Xiaoming's public key pair Key S Encrypt and send it to Xiao Ming, who decrypts it with his private key
Only Xiao Ming can decrypt this process, so it is safe
Now the new question is: How can the public key be transmitted to each other safely?
Do you want to use symmetric or asymmetric encryption? None of them are right. This is no longer feasible.
Imagine that in life, we have a contradiction and a problem. Who do we trust most? It must be the government
Now I download the public key from Xiao Ming is unreliable and unsafe
Who should I trust? Whose public key is Xiao Ming's real public key?
Therefore, we also set up an organization that we all believe in. Anyway, I believe in this organization unconditionally. This is the rule.
Let's name this organization CA mechanism
Well, now we leave the problem to CA, whether Xiaohua, Xiaoli or Xiaomei, as long as we get Xiaoming's public key, we will get it from CA
Where did CA get Xiao Ming's public key? It must be from Xiao Ming. For Xiao Ming, I have already given my public key to your CA, and your CA organization must ensure the safe transmission to others
This CA is also unlucky. All the work you can't do is left to me. It's not me and Xiaohua falling in love...
Complaints are complaints. How does CA solve them?
The answer is digital certificate , how come another name comes out, digital certificate What kind of ghost is it? Is it already dizzy? Don't worry. It's dizzy at this time. Turn back and look at the front
Have a look several times, and don't forget that the author has seen N many times, asked himself questions, and tried to solve them himself, only then did he understand the process.
Let's start with a conclusion: Digital certificate is to solve the problem of public key transmission
Repeat the important event three times: Digital certificate is to solve the problem of public key transmission , Digital certificate is to solve the problem of public key transmission , Digital certificate is to solve the problem of public key transmission
Before talking about digital certificates, let's solve this problem
Question 6: During the transmission of letters, how to ensure that the content is not tampered with, that is, the integrity of the information?
Combined with the encryption knowledge we learned earlier, we can use the one-way encryption algorithm. Let's take the md5 encryption algorithm as an example
-
After Xiaoming writes a letter to Xiaohua, he uses MD5 to encrypt the content of the letter to get a unique string. We call this string summary
-
Xiao Ming writes the one-way encryption algorithm md5 at the bottom of the letter and the summary of the message content calculated by md5, and sends it to Xiao Hua
-
After Xiaohua receives the letter, she sees the md5 algorithm at the bottom of the letter, so she encrypts the message content with md5 algorithm to get a new summary
-
Xiaohua compares the new abstract with the one attached at the bottom of the letter. If it is equal, it means that the letter has not been corrected
-
If it is not equal, it means that the content of the letter has been corrected by others.
This process is shown in the figure below.

But even the above process is problematic. What if Lao Wang appears again
- First, Lao Wang got the letter and changed it
- Lao Wang used the md5 algorithm to re send the message content to md5 to get a new encryption string
- Old Five put the new encryption string at the bottom of the letter and sent it to Xiaohua
- At this time, Xiaohua cannot tell whether the letter has been tampered with after receiving it.
As shown in the figure below:

Therefore, the integrity of the content cannot be guaranteed by simply using one-way encryption algorithms to generate abstracts
So how can we ensure the integrity of the letter and not be tampered with?
The answer is, sign
Another noun comes out, signature. There are too many nouns in this article.
From the previous study, we know that asymmetric encryption has two functions, one of which is identity authentication
Let's change the above example:
- Xiao Ming uses md5 to calculate the content of the letter to get a string, which we call summary
- Xiao Ming encrypts the digest with his private key to get another string, which we call signature
- Send the md5, summary and signature to Xiaohua
- Xiaohua decrypts the signature with Xiaoming's public key to get the summary of the letter. If it is d1
- Xiaohua uses md5 to calculate the content of the letter to get a summary of the letter. If it is d2
- Compare whether d1 and d2 are equal, which means that the content of the letter has not been tampered with
- D1 and d2 are not equal, indicating that the content of the letter has been tampered with.
At this point, the process is safe
If Lao Wang intercepts the letter again, Lao Wang can modify the content of the letter and use md5 to calculate a new summary again
But Lao Wang can't change his signature. Because the signature is encrypted with Xiao Ming's private key, even if Lao Wang can decrypt it
Lao Wang can't generate a new signature because only Xiao Ming has his own private key.
And Xiaohua decrypts the signature with Xiaoming's public key after receiving the letter. If Lao Wang encrypts the digest with his private key to generate a new signature
Xiaohua cannot decrypt with Xiaoming's public key.
At this time, we will define the temporary concept
abstract : md5 (or other one-way encryption algorithms). The string encrypted by the content is called the digest
autograph : Xiao Ming encrypts the digest with the private key and encrypts the signature string, which is called signature
Signature verification Xiaohua uses Xiaoming's public key to decrypt the signature. The comparison between the decrypted abstract and the original is called signature verification
Question 7: How did digital certificates come into being?
The digital certificate is issued by the CA organization. First, if Xiao Ming wants to have a digital certificate, he needs to apply to the CA organization
CA will issue Xiaoming a digital certificate, which contains
- Public key: Xiao Ming's public key
- Issued by: CA (Certificate Authority)
- Validity period: the service life of the certificate
- Digest algorithm: the specified digest algorithm used to calculate the certificate digest
- Fingerprint: the summary of the certificate to ensure the integrity of the certificate
- Signature algorithm: used to generate signatures to ensure that the certificate is issued by the CA
- Serial number: the unique identifier of the certificate
Knowing the contents of the certificate, let's understand how the certificate is generated?
-
Write Xiaoming's public key, issuer, validity period, digest algorithm and hash algorithm into the certificate
-
CA calculates the digest of the whole certificate according to the specified hash algorithm in the certificate, that is, digest
-
According to the signature algorithm and the summary calculated in the previous step, CA uses its own private key Encrypt the digest to generate the signature of the CA, that is, signature
-
Finally, publish the summary, signature and basic information of the certificate together to get Xiao Ming's certificate
Question 8: The role of digital certificates
From the above, we know that digital certificates solve the problem of public key transmission. At the same time, we know that digital certificates are just files
Since digital certificates are used to solve the secure transmission of public keys, how to solve the transmission problem
Now that Xiao Ming has his own certificate, we will not publicly transfer the public key, just transfer the certificate
So, Xiao Ming and Xiao Hua need secure communication now. What is the process? as follows
-
Xiaoming sends his digital certificate to Xiaohua
-
Worried about the certificate being swapped by Lao Wang, Xiaohua needs to verify the certificate. What does it verify?
-
In fact, it is to verify whether the number is issued by the CA organization or not. We believe that the transmission is unsafe.
-
Verifying whether the digital certificate is issued by the CA requires CA's public key 。。。 (Why do you need the CA's public key? Because the signature on the certificate is encrypted by the CA's private key. Only the CA's public key can decrypt it.)
Ah ah, I can't stand it. Why do I need a public key after a long time? We talked about digital certificates for a long time, just to transmit public keys
Therefore, the following description would be better
Verifying whether digital certificates are issued frequently by CA requires CA's digital certificate (because there is CA's public key in it)
-
Where can we find CA's digital certificate? From the above description, we know that if we need a digital certificate, we can apply to the CA and the CA will issue it to us.
-
So where did CA get its own digital certificate? The answer is that it is also issued to us by ourselves, so where do we get it?
-
If you download it from the Internet or from other servers, it may be swapped and unsafe.
-
This is really a sad story, but today Gofei Rabbit wants to finish this story.
-
It is not safe to download digital certificates from the Internet or from other servers. So what is safe?
-
The answer is: When your computer installs the operating system, there are already many CA digital certificates built into the operating system
-
That is to say, as long as you have installed the operating system, whether it is Windows, Linux, or Mac, or the computer you just bought, it already has the digital certificate of CA organization
-
It can be believed that this is the digital certificate of the real CA organization, without any fake. (Unless you install a pirated operating system, we try to use a genuine operating system)
The above process is really complicated. Brother Rabbit took a long time to figure it out. He knew that this interview would hurt many people. In fact https It doesn't matter if I don't know the process
It doesn't affect your code writing, but those interviewers love to ask questions, as if they can understand the process. It's not good to ask about design patterns.
But then again, Brother Rabbit is writing his own HelloWorld Technology Community Configure https Digital certificate, it's really hard to do without understanding these
It's not easy to write an article, especially this article. I spent a lot of energy to make it easier to understand. If you can see this, please pay attention
Especially to help promote Brother Rabbit HelloWorld Technology Community , one world, one line of code, our domain name is: www.helloworld.net
-
Our computers are born with CA digital certificates, and they are real. Born. God made it
Then we can distinguish the authenticity of digital certificates.
Question 9: Verification of digital certificates
It can be seen from the above:
Xiaohua receives Xiaoming's digital certificate. First, verify the digital certificate, that is, whether it is issued by the CA
Since our operating system has built-in digital certificates of all CA organizations, we can verify the digital certificates
Before talking about the process, let's briefly review the previous summary and signature
Abstract=md5 (certificate content): a one-way encryption algorithm, such as md5, encrypts the entire content of the certificate to obtain a summary, also known as the certificate fingerprint
Signature=privateKey (digest): the private key encrypts the digest of the previous step to generate a signature
The verification process of digital certificate is as follows:
- Xiaohua uses the digital certificate of the built-in CA to obtain the public key of the CA
- The digital certificate sent by Xiaoming, if we call it C, Xiaohua decrypts the signature in the C certificate with the public key of CA, and gets the abstract D
- Xiaohua calculates the whole content of the certificate with md5 according to the digest algorithm in the C certificate to get the digest D1
- Whether floret comparison abstract D and abstract D1 are equal
- If D==D1, this certificate is issued by CA
- If D!=D1, this certificate is not issued by CA, which is risky and unsafe
If the certificate is verified, it means that the certificate is indeed issued by the CA. At this time, Xiaohua can get Xiaoming's public key from the digital certificate
When Xiao Ming applies for a digital certificate, the owner of the digital certificate is Xiao Ming, and the CA will verify Xiao Ming's identity, so Xiao Ming's public key in the digital certificate is true
So far, we have finally completed one thing: Xiao Ming correctly and securely transferred his public key to Xiao Hua
The establishment of this matter will make our work much easier. Next, let's take a look at the specific transmission process
Question 10: Complete transmission process
Now let's take a look at Xiaoming's communication with Xiaohua again. It's different from the previous one. Let's take a look:
- Xiao Ming attaches the summary algorithm to the bottom of the letter after writing. If it is MD5, the summary calculated through MD5
- Xiao Ming encrypts the summary in the previous step with his private key to get the signature
- Xiao Ming attaches the abstract algorithm, abstract and signature to the bottom of the letter, and then sends his digital certificate to Xiao Hua together
- After receiving the letter, Xiaohua first uses her own CA digital certificate to obtain the CA public key, and then uses the CA public key to verify the digital certificate (that is, the process described above)
- After the digital certificate is verified, it indicates that the certificate is issued by the CA and has not been tampered with
- Xiaohua got Xiaoming's public key from the certificate
- With Xiao Ming's public key, the next step is to verify the message content
The verification process for the content of the letter is as follows (we actually talked about it before)
- Xiaohua decrypts the signature of the letter with Xiaoming's public key to get the abstract D1 of the letter
- Xiaohua uses the summary algorithm to calculate the letter and get the summary D2
- Whether floret contrast D1 is equal to D2
- If not, it indicates that the letter has been tampered with and is unsafe
- If equal, it means that the contents of the letter have not been tampered with
- In the same case, Xiaohua gets the contents of the letter
Summary:
All the above contents refer to the process of digital certificate, encryption and decryption, signature, and signature verification, which has not been officially explained https The process.
With the above knowledge, it is much easier for us to talk about https. Let's see a picture
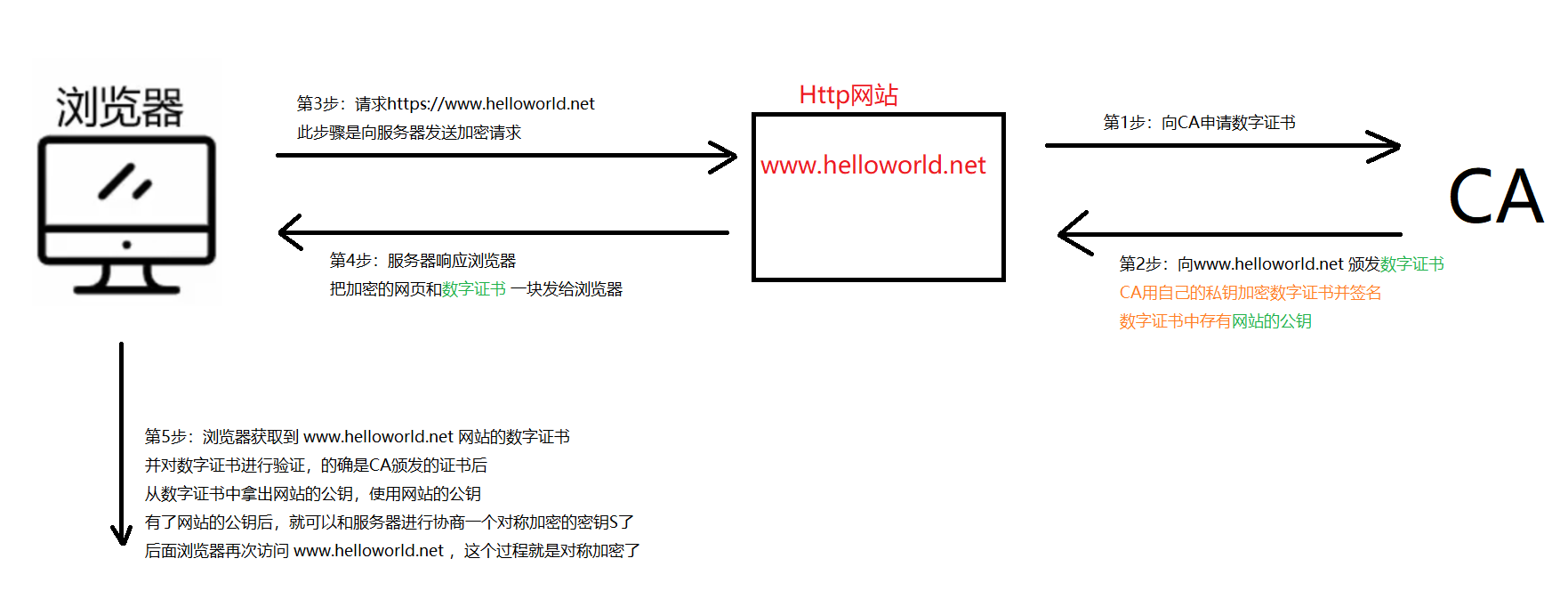
We visit www.helloworld.net Take the website as an example to explain the process of https
This process is divided into three stages, which are described below
visit www.helloworld.net Process of The stages are as follows
-
Website application certificate stage
- Website applies for digital certificate from CA organization (some materials, such as domain name, need to be submitted)
- CA writes important information such as digest algorithm, domain name and public key of website to the certificate
- CA calculates the certificate summary according to the summary algorithm written in the certificate
- CA encrypts the digest with its own private key and calculates the signature
- CA generates a digital certificate and issues it to
www.helloworld.net
- The administrator of the website puts the certificate on his own server
-
Browser Authentication Certificate Phase
- The browser enters in the address bar
https://www.helloworld.net , and enter
- The server sends the digital certificate to the browser
- The browser uses the digital certificate of the CA built in the operating system to obtain the public key of the CA
- The browser uses the CA public key to verify the signature of the digital certificate of www.helloworld.net
- Specifically, the browser decrypts the signature in helloworld's digital certificate with the CA public key, and gets the abstract D1
- The browser calculates the certificate digest D2 according to the digest algorithm in helloworld digital certificate
- Compare D1 and D2 for equality.
- If they are not equal, the certificate is swapped
- If they are equal, the certificate verification has passed.
-
Negotiation of symmetric encryption key phase
- After the browser validates the digital certificate
- The browser gets the public key in the digital certificate, that is
www.helloworld.net Public key of the website
- After the browser has the public key of the website, it uses the public key to
Key S Encrypt and send the encrypted ciphertext to the server
- After the server receives the ciphertext, it decrypts it with its own private key to get
Key S
- After that, the browser and server will use
Key S Symmetrical encrypted communication has been carried out.
It took a whole day to finish talking
With so many processes, it is very simple to grasp several key issues. In essence, it is two people. How to communicate safely and efficiently
Let's make a brief summary again. I think it's better to adopt a question and answer method
Question 1: How can Xiaoming and Xiaohua communicate safely?
Answer: Through encryption
Question 2: Which encryption method is more efficient for communication?
Answer: Symmetric encryption
Because one-way encryption can't decrypt
Asymmetrical encryption, too slow, not good
Only symmetric encryption, fast
Question 3: With symmetric encryption, how can the key S be transmitted safely?
Answer: Xiaohua uses Xiaoming's public key Key S Encrypt and send it to Xiao Ming
Xiao Ming decrypts with his private key
Question 4: How can Xiao Ming safely transfer his public key to Xiaohua?
Answer: Use digital certificates
Specifically, Xiao Ming applies to CA for a digital certificate of his own and puts his public key in the certificate
Xiaoming sends the digital certificate to Xiaohua
Question 5: How does Xiaohua verify the authenticity of digital certificates?
Answer: Xiaohua uses the CA's digital certificate built in the operating system to obtain the CA's public key, and uses the CA's public key to verify the signature of the digital certificate
If the signature is checked, the digital certificate is true.
I hope readers can ask themselves more about the above questions and how to solve them if they are themselves
This article is finished. The problem to be solved is how to communicate with each other in a safe and efficient way
It's really not easy to see the end. It's worth encouraging. If my article is useful to you
Please forward it to the people who need it, and also help pay attention to it. Originality is not easy. thank you