Python operator ID card two element verification interface, ID card real name authentication interface
AliCloud web application

One click PDF to AutoCAD format

Online audio conversion tool - free

Convert multiple vectors and document formats online - free
See how I can make my mobile phone scan code in seconds
Can the formatted SD card photos be restored?
Procedures for installing Cockpit Podman on Ubuntu 24.04 LTS
What attacks can the US advanced anti DDoS ECS defend against- Lan Yiyun
How to select servers for foreign trade websites

Review what happened during the computer operation
The dilemma and current situation of Beidou Internet of Vehicles
Instructions, responses, synchronization primitives and precautions in asynchronous programming
Js uses the Date object to process time
How to solve the problem of false wake-up and wake-up of e-ink screen labels?
Lombok Notes
In the field of e-ink screen label, how to choose a good processor?
Short range wireless ad hoc network protocol stack: what is the meaning and value?
DC-3 Penetration Test Process Based on Vulnhub Range
How to select wireless communication scheme in the field of ink screen e-paper label/e-paper price tag?
Error: Connection refused: Not authorized
Sweden's national core data is being handled in one pot. Can enterprise digital security be good?
Hibernate L2 cache

Performance tool emqtt bench Benchmark test example
How LoadRunner monitors Linux system resources
How to do the pressure test of IoT system?
Interfaces and communication protocols commonly used in embedded development
How to do the pressure test of IoT system?
In the era when data and AI emerged, we need to pay more attention to safety and compliance issues by iterating on digital platforms
04 Deeply analyze the application of IoT architecture and technology to agricultural greenhouse system
Why is the data platform built at the cost of blood and money mediocre?

The ability to control data, like the use of ChatGPT, is a required course for modern workers
To continuously improve agility, you need to implement Sitecore DevOps
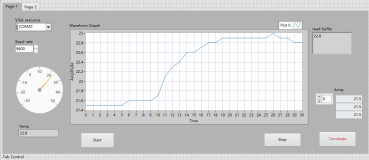
Temperature acquisition and LabVIEW upper computer display based on STC8H8K64U and DS18B20
NAPT features and configuration practice sharing
Upgrade "new play"? Sitecore OrderCloud has new functions
Logic circuit and logic operation notes sharing
Ruizhe Information: Did the website collapse again? Internet black swan incidents occur frequently, which enterprises have to prevent!
Program performance analysis
Java smart site supervision integrated cloud platform APP source code SaaS mode
Analyze several cases of index failure
Understand the difference between TCP and UDP
Rapid Design and Development of Phase shifted Full bridge DC-DC Converter

Internet of Things
