Point stone privacy calculation
-
Product Overview -
Product Matrix -
Product advantages -
Product Functions -
Application scenarios -
Customer Stories -
Related products
Product Overview
It supports multi-party data security "integration" and modeling, analysis and calculation, provides full process services from data analysis, model training, evaluation to application deployment, and has different cloud/end service deployment modes. Solve the business needs of multiple scenarios, such as risk control, precision marketing and cold start of new users, break the isolated island of data applications, effectively guarantee data security and user privacy, and achieve data availability, invisibility, security compliance, flow and sharing.
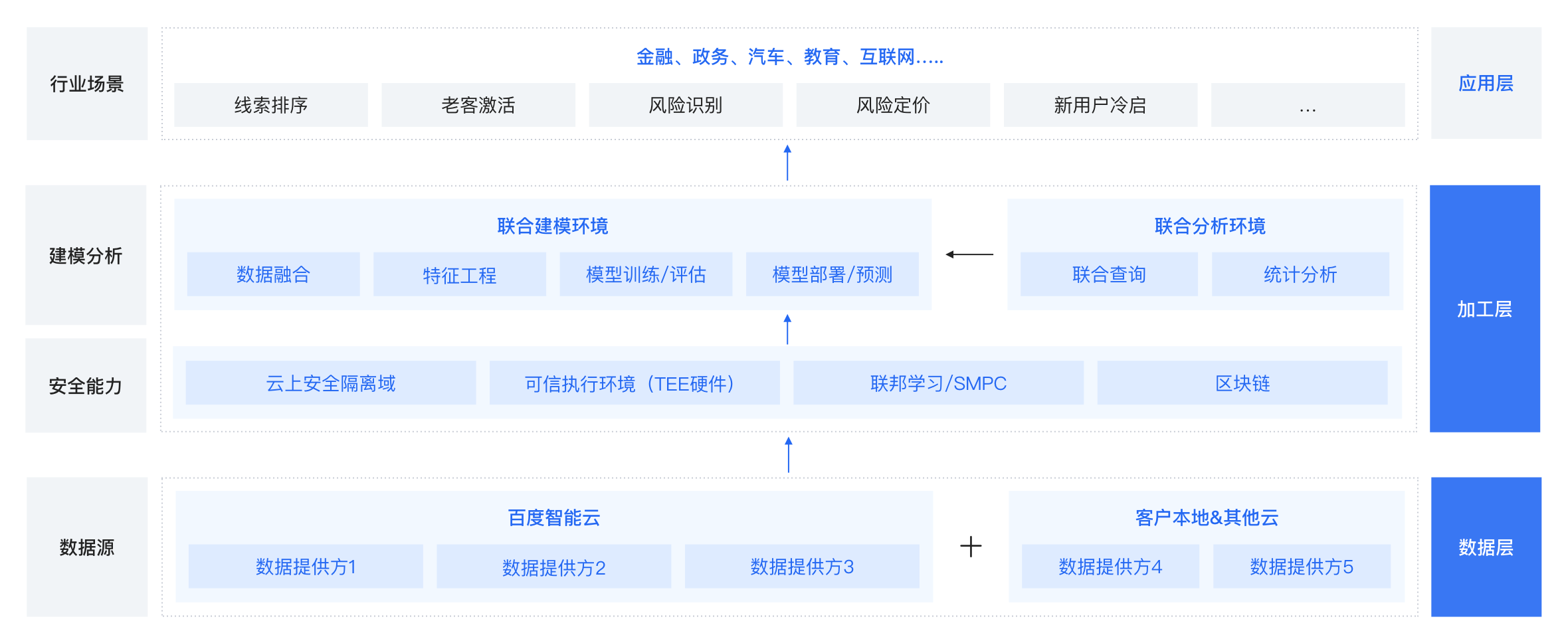
Product Matrix
Baidu Dianshi Union Learning The distributed architecture, based on MPC, FL, DP and other technologies, provides data security and privacy protection capabilities for the whole process of data joint analysis, joint computing and joint modeling. Baidu Dianshi Confidential Calculation A general secure computing platform based on trusted hardware provides high-performance data flow services and privacy computing services. Baidu Dianshi Data Security Sandbox A secure and controllable data security sharing platform to assist the government and institutions in solving data security issues and privacy protection issues in the process of data opening.
Product advantages
Technological advantages of independent research and development
Rich open forms
Mature industry experience
Product Functions
Security data fusion -
Multiple security guarantees -
Provide data security fusion solutions based on federated learning, secure multi-party computing, data security sandbox, trusted computing and other technologies.
-
Self developed technology -
The independently developed heterogeneous privacy computing solution ensures the security of data storage and computing while making data available and invisible.
-
Multiple modeling methods -
Form based interaction -
Users can easily complete model construction and iteration through form based interaction.
-
Personalized modeling -
The product also supports personalized modeling analysis and tuning in a secure computing environment.
-
Rapid service deployment -
Rapid deployment model -
It supports the rapid deployment and release of the trained model, and can be seamlessly connected to different business application systems of customers.
-
Service performance monitoring -
Provide service performance monitoring to ensure service stability; It also supports dynamic capacity expansion.
-
Application scenarios
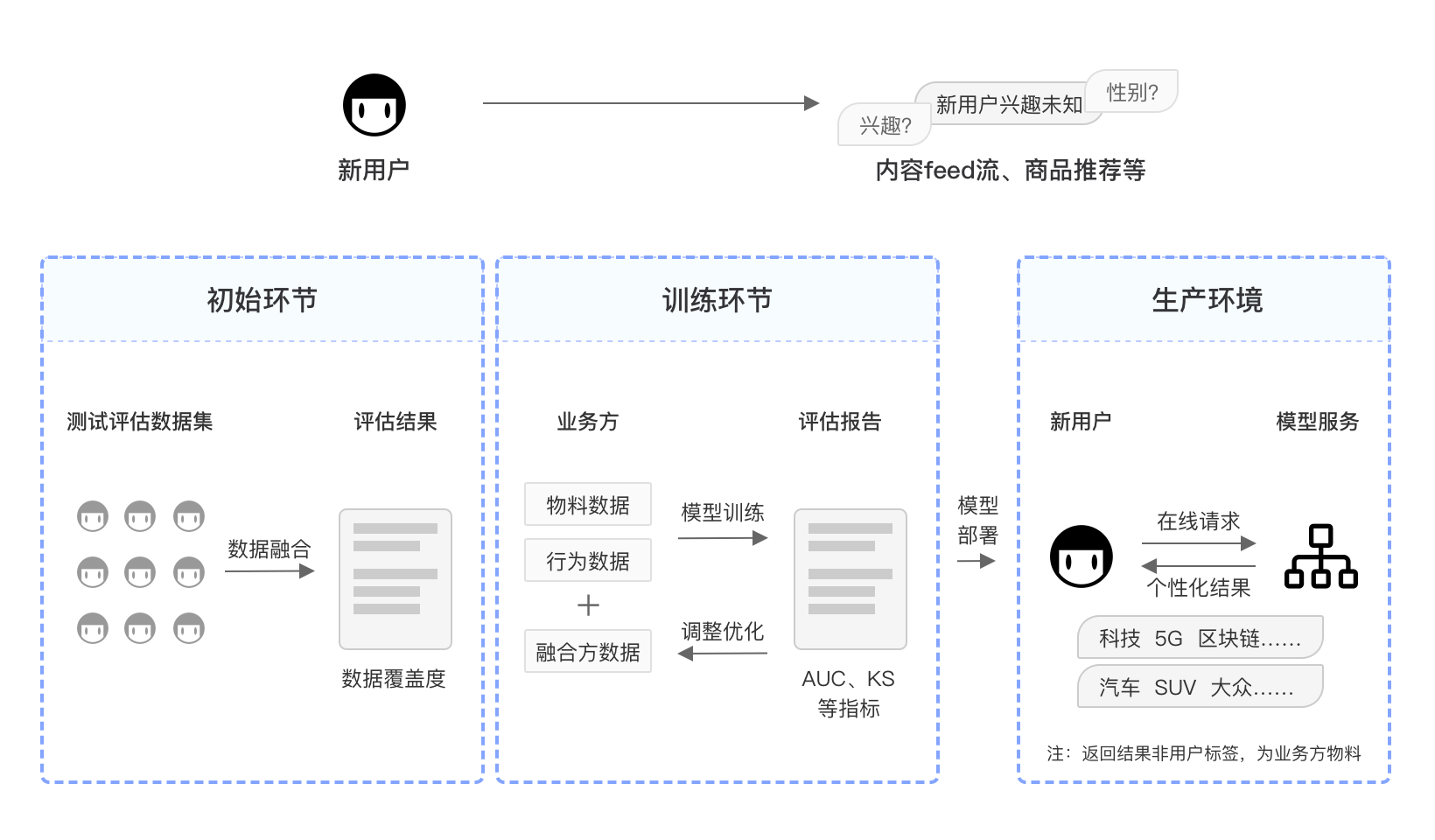
Scenario Overview
We can provide
Leading technology
Whole process service