RFID is a contactless radio-tag technology. It is quite common and you may see it in a lot of places: intercoms, bank cards, public transport passes, office passes, they are used to track domestic animals, for toll collection, etc. The two main RFID tag types are high frequency and low frequency.
RFID is a non-contact radio tag technology. It is very common. You may see it in many places: walkie talkies, bank cards, public transport passes, office passes, which are used to track livestock and collect fees. The two main types of RFID tags are high-frequency and low-frequency.
- Low-Frequency tags (125 kHz) — work at a higher range. Despite being insecure and dumb, they are still used in primitive access control systems: in building intercoms, offices, sports facilities, museums.
Low-frequency label (125 kHz) - operates in a higher range. Although unsafe and stupid, they are still used in the original access control system: building intercom, offices, sports facilities, museums.
- High-Frequency tags (13.56 MHz) — have a lower effective range when compared with the low-frequency ones but have more complex protocols. They support encryption, authentication, and cryptography. These tags are commonly used in contactless bank cards, to pay for public transport, and in high-security access control systems.
High frequency tag (13.56 MHz) - Compared with low-frequency tags, the effective range is lower, but the protocol is more complex. They support encryption, authentication, and cryptography. These tags are usually used for contactless bank cards, public transport payment and high security access control systems.
Here we will compare these two types of tags, take a look at the main protocols and learn to work with them using Flipper Zero — we will read, emulate, save and clone them. You will see how you will be able to save your office, sports, home whatever RFID keys you have and we'll take a glimpse at what Flipper can read from a bank card.
Here, we will compare these two types of tags, look at the main protocols and learn to use them with Flipper Zero - we will read, simulate, save, and clone them. You will see how you can save any RFID key in your office, sports and home, and we will know what Flipper can read from the bank card.
 RFID chip turns on when it receives power from the reader's RF field
RFID chip turns on when it receives power from the reader's RF field
The RFID chip turns on when it receives the power from the RF field of the reader
Most RFID tags are passive tags with no internal power source. The chip inside is completely turned off until the tag is exposed to a reader's electromagnetic field. As soon as it comes within range, the tag's antenna begins absorbing energy from the reader's EM field and the chip receives power. The chip then turns on and begins communicating with the reader. It's worth mentioning, that a tag's antenna is tuned to a specific frequency, so the tag can only activate when it is inside a suitable electromagnetic field.
Most RFID tags are passive tags without internal power supply. The internal chip is completely closed until the tag is exposed to the electromagnetic field of the reader. Once in range, the antenna of the tag begins to absorb energy from the electromagnetic field of the reader, and the chip receives power. Then the chip turns on and starts communicating with the card reader. It is worth mentioning that the antenna of the tag is tuned to a specific frequency, so the tag can only be activated in a suitable electromagnetic field.
RFID Tag Types
On the outside RFID tags can be quite different: cards both fat or thin, key fobs, bracelets, coins, rings, or even stickers. Judging by the visuals alone it's almost impossible to distinguish the frequency or protocol the tag operates on.
From the outside, RFID tags may be very different: thick or thin cards, key chains, bracelets, coins, rings, and even stickers. From the perspective of visual effects alone, it is almost impossible to distinguish the frequency or protocol of tag operation.
 On the outside RFID tags can be quite different
On the outside RFID tags can be quite different
From the outside, RFID tags may be very different
Quite often manufacturers use similar plastic cases for different types of RFID fobs operating on different frequencies. Two absolutely visually similar tags might be totally different inside. It is worth considering when you try to distinguish the type of tag you have. In this article, we will be looking at the two most popular types of RFID tags that are used in access control systems. Flipper Zero supports both their frequencies.
Manufacturers often use similar plastic housings to accommodate different types of RFID remote keys operating on different frequencies. The interior of two labels that are absolutely similar visually may be completely different. It is worth considering when you try to distinguish the types of tags you have. In this article, we will learn about the two most popular RFID tag types used in access control systems. Flipper Zero supports both frequencies.
There is a variety of RFID protocols working on other frequencies. UHF for example uses the 840-960 MHz range. They are used for tracking assets in warehouses, paying for toll roads, tracking wild animals during their migration and so forth. These tags may have a battery and work from a couple of meters to kilometers. They are quite rare though, And you may not include them unless you go looking for them specifically. We will omit them completely for the purpose of this article. For example, UHF uses the 840-960 MHz range. They are used to track assets in warehouses, pay toll roads, track wildlife migration, and so on. These labels may be equipped with batteries and can operate from several meters to several kilometers. But they are very rare. Unless you go to them specifically, you may not encounter them. For the purpose of this article, we will omit them completely.
125 kHz & 13.56 MHz – Which is Which?
125 kHz and 13.56 MHz – which is which?
The easiest way to understand what range of the RFID tag is operating on is to look at the antenna. Low-frequency tags (125 kHz) have an antenna made of a very thin wire, literally thinner than a hair. But such antennas have a large number of turns, therefore, such an antenna looks like a solid piece of metal. High-frequency cards (13.56 MHz) have a significantly smaller number of thicker turns, with visible gaps between them.
The easiest way to understand the working range of RFID tags is to look at the antenna. The antenna of the low-frequency tag (125 kHz) is made of very thin wires, actually thinner than hair. However, this kind of antenna has many turns, so it looks like a solid metal. The number of thick turns of high-frequency card (13.56 MHz) is obviously less, and there is obvious gap between turns.
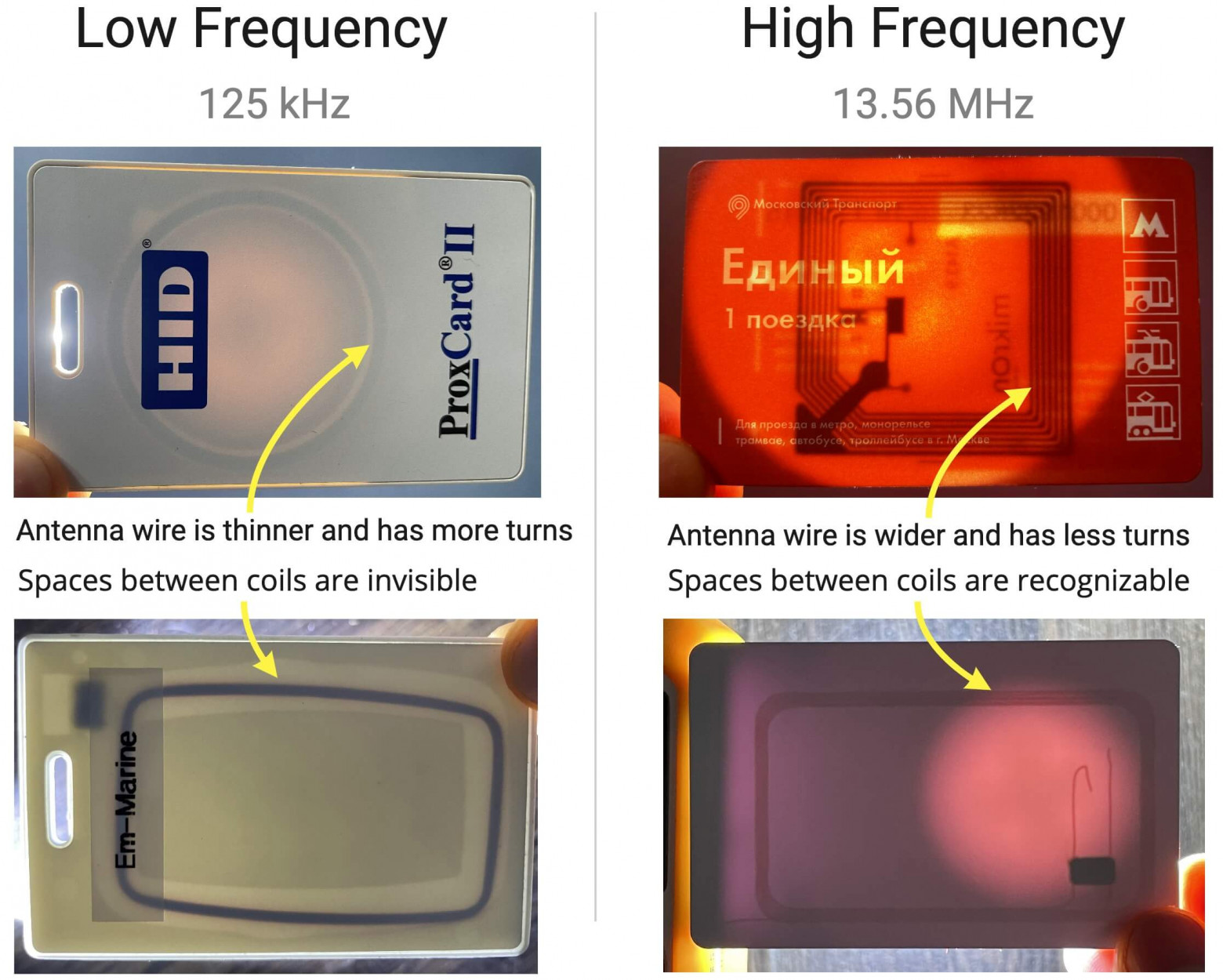 With enough backlight, you can guess the card's operating frequency
With enough backlight, you can guess the card's operating frequency
When the backlight is sufficient, you can guess the operating frequency of the card
You can shine some light through an RFID card to see an antenna inside. If the antenna has only a few large turns, it is most likely a high-frequency antenna. If the antenna looks like a solid piece of metal with no gaps between the turns, it is a low-frequency antenna.
You can shine some light through the RFID card to see the antenna inside. If the antenna has only a few large turns, it is likely to be a high-frequency antenna. If the antenna looks like a solid metal with no gap between turns, it is a low-frequency antenna.
 Low-frequency antennas have a thin wire for their turns, while high-frequency use a thicker one
Low-frequency antennas have a thin wire for their turns, while high-frequency use a thicker one
The turns of the low-frequency antenna are thin wires, while the high-frequency antenna uses thicker wires
Low-frequency tags are often used in systems that do not require high security: building access, intercom keys, gym membership cards, etc. Due to their higher range, they are convenient to use for paid car parking: the driver does not need to bring the card close to the reader, as it is triggered from further away. At the same time, low-frequency tags are very primitive, they have a low data transfer rate. For that reason, it's impossible to implement complex two-way data transfer for such things as keeping balance and cryptography. Low-frequency tags only transmit their short ID without any means of authentication.
Low-frequency label Commonly used in systems with low security requirements: building access control, intercom key, gym membership card, etc. Because of its high range, it is convenient for paying parking lots: drivers do not need to put the card near the card reader because it is triggered from a far place. At the same time, low-frequency tags are very primitive, and their data transmission rate is low. Therefore, it is impossible to realize complex two-way data transmission, such as balance and encryption. LF tags only transmit their short IDs without any authentication means.
High-frequency tags are used for a more complex reader-tag interaction when you need cryptography, a large two-way data transfer, authentication, etc.
When you need encryption, massive two-way data transmission, authentication, etc, High frequency tag It can be used for more complex reader and tag interaction.
It's usually found in bank cards, public transport, and other secure passes.
It usually exists in bank cards, public transport and other security passes.
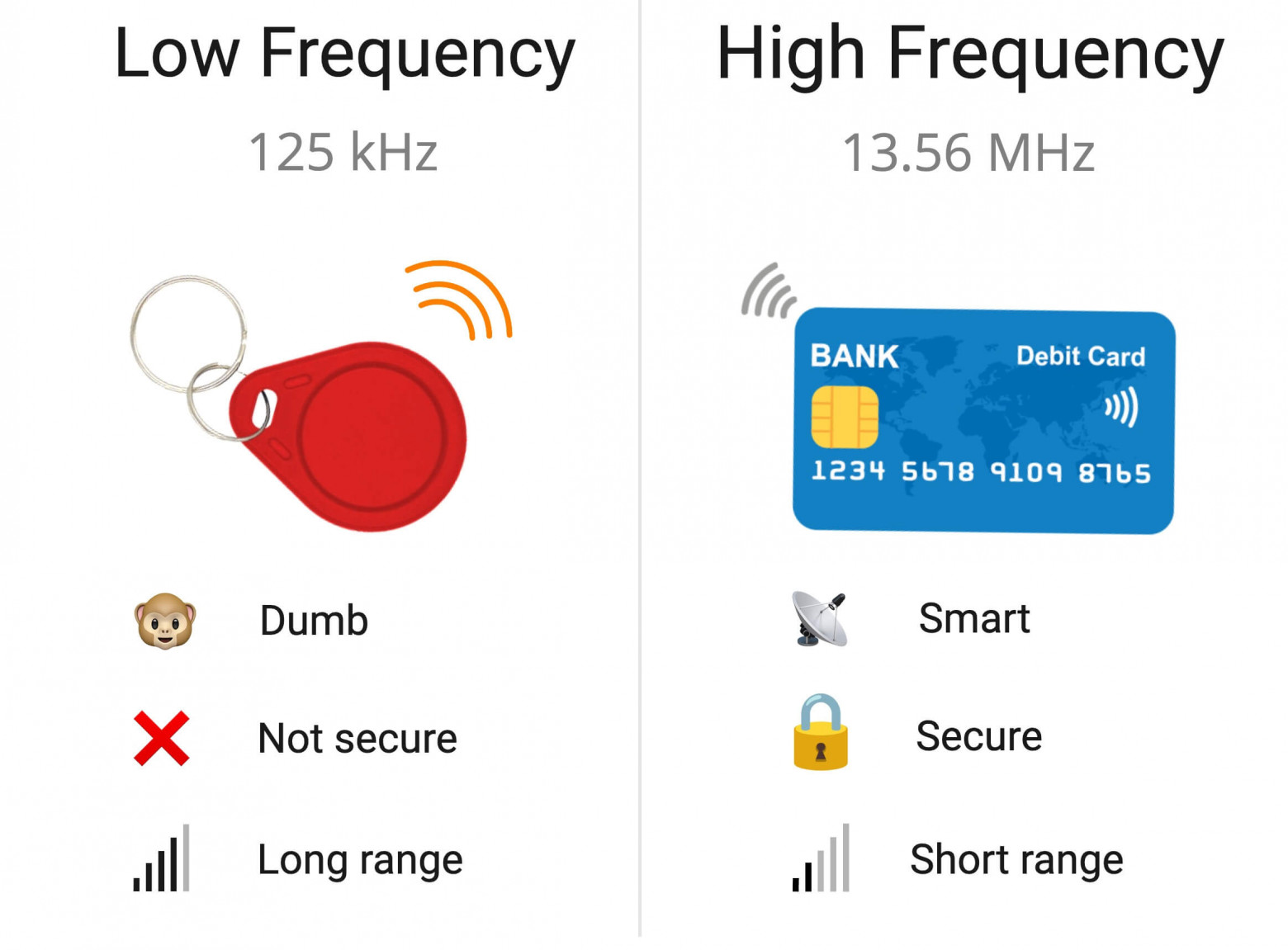 125 kHz & 13.56 MHz RFID tag comparison
125 kHz & 13.56 MHz RFID tag comparison
Comparison of 125 kHz and 13.56 MHz RFID tags
- Long Range — lower frequency translates to higher range. There are some EM-Marin and HID readers, which work from a distance of up to a meter. These are often used in car parking.
long distance - Lower frequencies can be translated into higher ranges. There are some EM Marin and HID card readers, and the working distance can reach one meter. These are usually used in parking lots.
- Primitive protocol — due to the low data transfer rate these tags can only transmit their short ID. In most cases, data is not authenticated and it's not protected in any way. As soon as the card is in the range of the reader it just starts transmitting its ID.
Original Agreement ——Due to the low data transfer rate, these tags can only transfer their short IDs. In most cases, data is not authenticated or protected in any way. Once the card is within the range of the reader, it will start to transfer its ID.
- Low security — These cards can be easily copied, or even read from somebody else's pocket due to the protocol's primitiveness.
Low security ——Due to the original nature of the protocol, these cards can be easily copied and even read from others' pockets.
- Low range — high-frequency cards are specifically designed so that they would have to be placed close to the reader. This also helps to protect the card from unauthorized interactions. The maximum read range that we managed to achieve was about 15 cm, and that was with custom-made high-range readers.
Low range -The HF card is specially designed, so it must be placed close to the card reader. This also helps protect the card from unauthorized interaction. The maximum reading range we have successfully achieved is about 15 cm, which is achieved using a customized high range reader.
- Advanced protocols — data transfer speeds up to 424 kbps allow complex protocols with full-fledged two-way data transfer. Which in turn allows cryptography, data transfer, etc.
Advanced Protocol - The data transmission speed is up to 424 kbps, supporting complex protocols and mature two-way data transmission. This in turn allows encryption, data transmission, etc.
- High security — high-frequency contactless cards are in no way inferior to smart cards. There are cards that support cryptographically strong algorithms like AES and implement asymmetrical cryptography.
High security ——High frequency non-contact card is no inferior to smart card. Some cards support algorithms with high encryption strength, such as AES, and achieve asymmetric encryption.
RFID in Flipper Zero
 How RFID antenna works in Flipper Zero
How RFID antenna works in Flipper Zero
How the RFID antenna in Flipper Zero works
Flipper supports both high-frequency and low-frequency tags. To support both frequencies we developed a dual-band RFID antenna that is situated on the bottom part of the device.
Flipper supports both high-frequency and low-frequency labels. To support these two frequencies, we have developed a dual band RFID antenna located at the bottom of the device.
A separate NFC controller (ST25R3916) is used for high-frequency protocols (NFC). It takes care of everything related to hardware interaction with the cards: reading and emulation. Low-frequency 125 kHz protocols are implemented programmatically via a custom analog frontend, that works in cooperation with MCU and also allows to read, write and emulate.
A separate NFC controller (ST25R3916) is used for High Frequency Protocol (NFC). It is responsible for all transactions related to the hardware interaction of the card: read and simulation. The low frequency 125 kHz protocol is programmed through a custom analog front-end, which works with MCU and also allows reading, writing and simulation. [Video] RFID antenna inside Flipper Zero
[Video] RFID antenna in Flipper Zero
The top part of the PCB is shielded with a ferromagnetic layer which isolates the rest of the electronic components from interference and extends the operating range by reflecting the high-frequency field.
The top of the PCB is shielded by a ferromagnetic layer, which can isolate other electronic components from interference, and expand the working range by reflecting high-frequency fields.
During assembly, the antennas are glued into Flipper's back panel. It connects to the PCB with pogo-pins. This greatly simplifies the assembly, as no cables are used and no UFL connectors are required.
During assembly, the antenna is glued to the backplane of Flipper. It is connected to the PCB through a spring pin. This greatly simplifies assembly because no cables are used and no UFL connectors are required.
Low-Frequency 125 kHz Protocols
Low frequency 125 kHz protocol
Low-frequency tags store a short ID, just a couple bytes long. The tag's ID is compared to IDs stored in the database of a controller or an intercom. However, the card will transmit its ID to anyone asking as soon as it receives power. Quite often the ID is inscribed on the card itself, so you can take a picture and input it into the Flipper manually.
Low frequency tags store a short ID, which is only a few bytes long. The ID of the tag is compared with the ID stored in the controller or walkie talkie database. However, once powered on, the card will send its ID to anyone who asks. Usually, the ID is engraved on the card body, so you can take a picture and manually enter it into Flipper.

Popular 125 kHz protocols:
Popular 125 kHz protocol:
- EM-Marin — EM4100, EM4102. The most popular protocol in CIS. Can be read from about a meter because of its simplicity and stability.
EM Malin - EM4100, EM4102. The most popular protocol in CIS. Due to its simplicity and stability, it can read about one meter.
- HID Prox II — low-frequency protocol introduced by HID Global. This protocol is more popular in the western countries. It is more complex and the cards and readers for this protocol are relatively expensive.
HID Prox II - Low frequency protocol introduced by HID Global. The agreement is more popular in western countries. It is complex, and the card and reader of the protocol are relatively expensive.
- Indala — very old low-frequency protocol that was introduced by Motorola, and later acquired by HID. You are less likely to encounter it in the wild compared to the previous two because it is falling out of use.
Indala - A very old low-frequency protocol, launched by Motorola and later acquired by HID. Compared with the first two, you are less likely to encounter it in the wild, because it is no longer used.
In reality, there are a lot more low-frequency protocols. But they all use the same modulation on the physical layer and may be considered, in one way or another, a variation of those listed above. At the time of writing Flipper can read, save, emulate and write all three protocols. There may be other ones, which are not supported in Flipper's firmware, but as the 125 kHz subsystem is implemented programmatically, we can add them in the future.
In fact, there are many low-frequency protocols. But they all use the same modulation on the physical layer, and can be considered as variants of those listed above in some way. At the time of writing, Flipper can read, save, simulate, and write all three protocols. There may be others. Flipper's firmware does not support them, but since the 125 kHz subsystem is programmed, we can add them in the future.
EM Marin EM Marin
[Video] Flipper reading an EM-Marin tag
[Video] Flipper reads EM Marin tags
EM-Marin is the most common format we have in CIS. It is simple and has no copy-protection. EM-Marin cards usually have EM4100 chips inside, but there are others as well. For example, you can have an EM4305 which can be re-written unlike the EM4100.
EM Marin is the most common format in CIS. It is simple and has no replication protection. The EM Marin card usually has a built-in EM4100 chip, but there are other chips. For example, you can have a rewritable EM4305, which is different from the EM4100.
To read a low-frequency card go into the Flipper menu 125 kHz RFID —> Read and place the tag on the back of the device. Flipper will attempt to determine the protocol and on success will display it alongside the card's ID. Since Flipper is trying all the protocols in one go it takes a bit of time. For example, you will need a couple of seconds to read an Indala card.
To read the low-frequency card, please enter the Flipper menu 125 kHz RFID —> Read Label and place it on the back of the device. Flipper will try to determine the protocol, which will be displayed next to the ID of the card after success. Since Flipper tries all the protocols at once, it takes some time. For example, it may take several seconds for you to read an Indala card.
 Unique EM-Marin ID on the card and on the Flipper
Unique EM-Marin ID on the card and on the Flipper
Unique EM Marin ID on card and fins
EM4100's unique code is 5 bytes long. Sometimes you can find it on the card itself. The unique code may be written both as a decimal or in hex. Flipper displays the code in hex, however, EM-Marin cards usually just have the 3 lower bytes written on them, and not the full 5-byte number. If there is no way to read them from the card, the other 2 bytes can be brute-forced.
The unique code length of EM4100 is 5 bytes. Sometimes you can find it on the card. The unique code can be written in decimal or hexadecimal. Flipper displays the code in hexadecimal, but the EM Marin card usually only writes three lower bytes instead of a complete five byte number. If they cannot be read from the card, the other 2 bytes can be brute force cracked. [Video] Emulating 125 kHz RFID to open an electric door lock
[Video] Simulate 125kHz RFID to open the electric door lock
To emulate an RFID tag we need to go into the menu 125 kHz RFID —> Saved , choose the necessary tag and then press Emulate .
To simulate RFID tags, we need to enter the menu 125 kHz RFID —> Saved , select the necessary labels and press Emulate 。
Some intercoms try to protect themselves from key duplication by sending a write command prior to reading. If the write succeeds, that tag is considered fake. When Flipper emulates RFID there is no way for the reader to distinguish it from the original one, so no such problems occur.
Some walkie talkies try to protect themselves from duplicate keys by sending a write command before reading. If the write is successful, the tag is considered false. When Flipper simulates RFID, the reader cannot distinguish it from the original RFID, so this problem will not occur.
HID Prox HID Proximitor
[Video] Flipper reading a HID26 tag
[Video] Flipper reads HID26 tags
HID Global — is the largest manufacturer of RFID devices in the world. They have several high and low-frequency RFID protocols. The most popular low-frequency HID protocol is the 26-bit H10301 (also known as HID26 or HID PROX II). The unique code is 3 bytes (24 bits) long, and 2 more bits are used for parity check (to ensure the integrity of data).
HID Global is the world's largest manufacturer of RFID equipment. They have a variety of high-frequency and low-frequency RFID protocols. The most popular low-frequency HID protocol is the 26 bit H10301 (also known as HID26 or HID PROX II). The unique code is 3 bytes long (24 bits), and the other 2 bits are used for parity check (to ensure data integrity).
Some HID26 cards have numbers written on them - they are the sales order number and the card's ID. You can't figure out the whole 3 bytes with that information alone, the card only has the 2 bytes printed on it in decimal format. That is the card's ID.
Some HID26 cards have numbers written on them - they are the sales order number and the ID of the card. All three bytes cannot be calculated based on this information alone, and only two bytes are printed on the card in decimal format. That is the ID of the card.
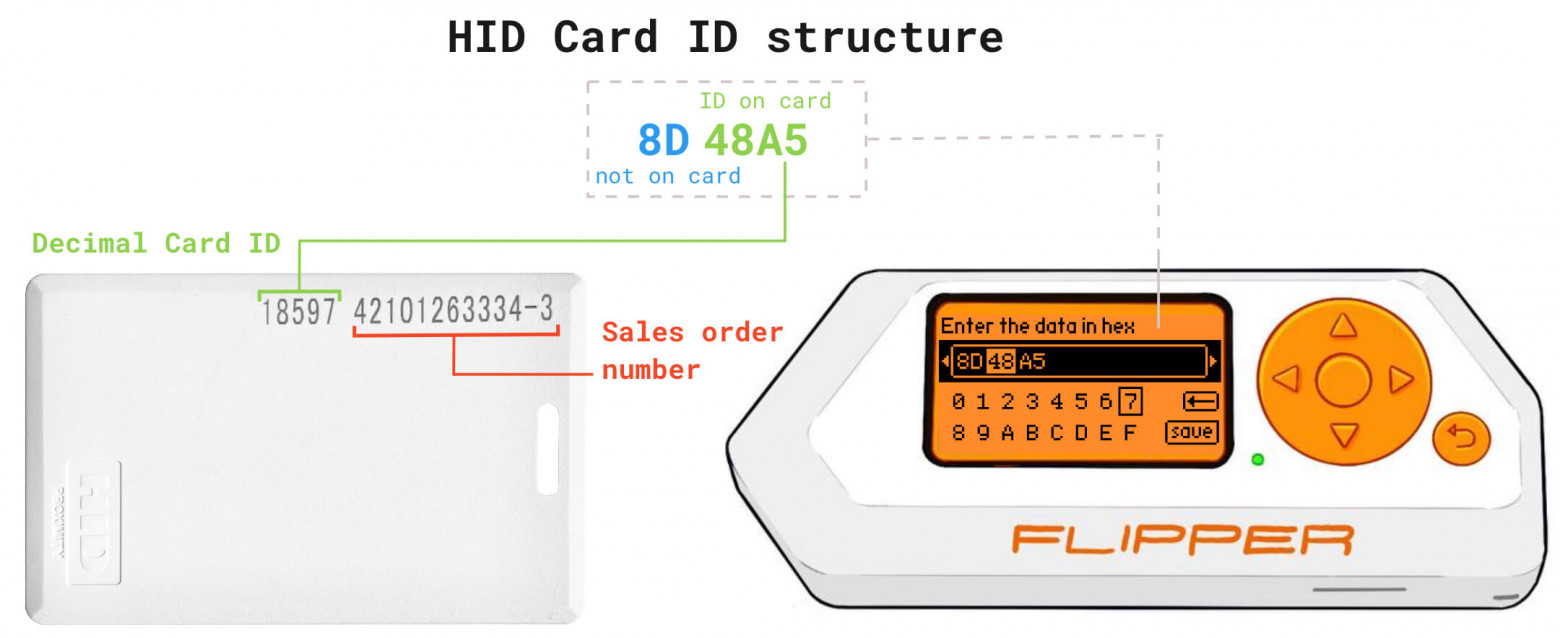 HID26 data structure on the card and when read using Flipper
HID26 data structure on the card and when read using Flipper
HID26 data structure on the card and data structure when using Flipper to read
Flipper can only work with the HID26 protocol of the HID family. In the future, we plan to extend this list. HID26 is the most popular one since it is compatible with most digital access control systems.
Flipper can only be used with HID 26 protocol of HID series. In the future, we plan to expand this list. HID26 is the most popular one because it is compatible with most digital access control systems. [Video] Flipper emulating a low-frequency card and opening the turnstile
[Video] Flipper simulates low-frequency card and opens the gate
Indala
Indala is an RFID protocol developed by Motorola and later acquired by HID. It's a very old protocol that you won't find in modern access control systems. Rare as it is, you may sometimes find it in the field. At the time of writing Flipper works with Indala I40134.
Indala is an RFID protocol developed by Motorola and later acquired by HID. This is a very old protocol, which cannot be found in modern access control systems. Although rare, sometimes you may find it in the wild. At the time of writing this article, Flipper uses Indala I40134. [Video] Flipper reading an Indala card
[Video] Flipper reads Indala card
Same as with HID26, cards using Indala I40134 have a unique code that is 3 byte long. Unfortunately, Indala's data structure is proprietary and everyone who wishes to support this protocol is forced to choose whichever byte order they want, and also how they interpret the signal on the hardware level.
Like HID26, the card using Indala I40134 has a unique code of 3 bytes long. Unfortunately, Indala's data structure is proprietary. Everyone who wants to support this protocol is forced to choose the byte order they want and how they interpret signals at the hardware level.
All these protocols are so simple that the card's ID may be entered manually without the original card. Having your card's ID in text format, anyone owning a Flipper could enter it manually.
All of these protocols are very simple, and the ID of the card can be entered manually without the original card. With the card ID in text format, anyone who owns Flipper can enter it manually.
Manually Entering the Card's ID
Enter the ID of the card manually
[Video] Entering an Indala card's ID without having the card itself
[Video] Enter the ID of the Indala card without the card itself
To add the card's ID go to the menu and choose 125 kHz RFID —> Add manually , then the protocol and enter the ID. The card added will be saved to the SD-card, and may then be emulated or written to a blank.
To add a card ID, go to the menu and select 125 kHz RFID —> Add manually , then select the protocol and enter the ID. The added card will be saved to the SD card, and then can be simulated or written blank.
Writing to a Blank Card
Write blank card
There are special blank cards that support any of the three protocols mentioned above (EM-Marin, HID Prox, Indala). T5577 is the most popular blank card type. To write an ID to a blank card go to the menu 125 kHz RFID —> Saved , then choose the key you want and press Write .
Some special blank cards support any of the above three protocols (EM Marin, HID Prox, Indala). T5577 is the most popular blank card type. To write the ID to a blank card, go to the menu 125 kHz RFID —> Saved , select the required key and press Write 。 [Video] Writing to a T5577 blank card
[Video] Write T5577 blank card
High-Frequency 13.56 MHz Protocols
High frequency 13.56 MHz protocol

High-frequency 13.56 MHz tags are a set of standards and protocols. They are usually referred to as NFC , but that's not always correct. The basic protocol set used on the physical and logical levels is ISO 14443. High-level protocols, as well as alternative standards (like ISO 19092), are based upon it.
The high-frequency 13.56 MHz label is a set of standards and protocols. They are often referred to as NFC , but this is not always true. The basic protocol set used at the physical and logical levels is ISO 14443. High level protocols and alternative standards such as ISO 19092 are based on it.
ISO 14443-A seems to be the most common implementation. Almost all of the public transport and office passes use it, and it's used in bank cards as well.
ISO 14443-A Seems to be the most common implementation. It is used by almost all public transport and office passes, as well as bank cards.
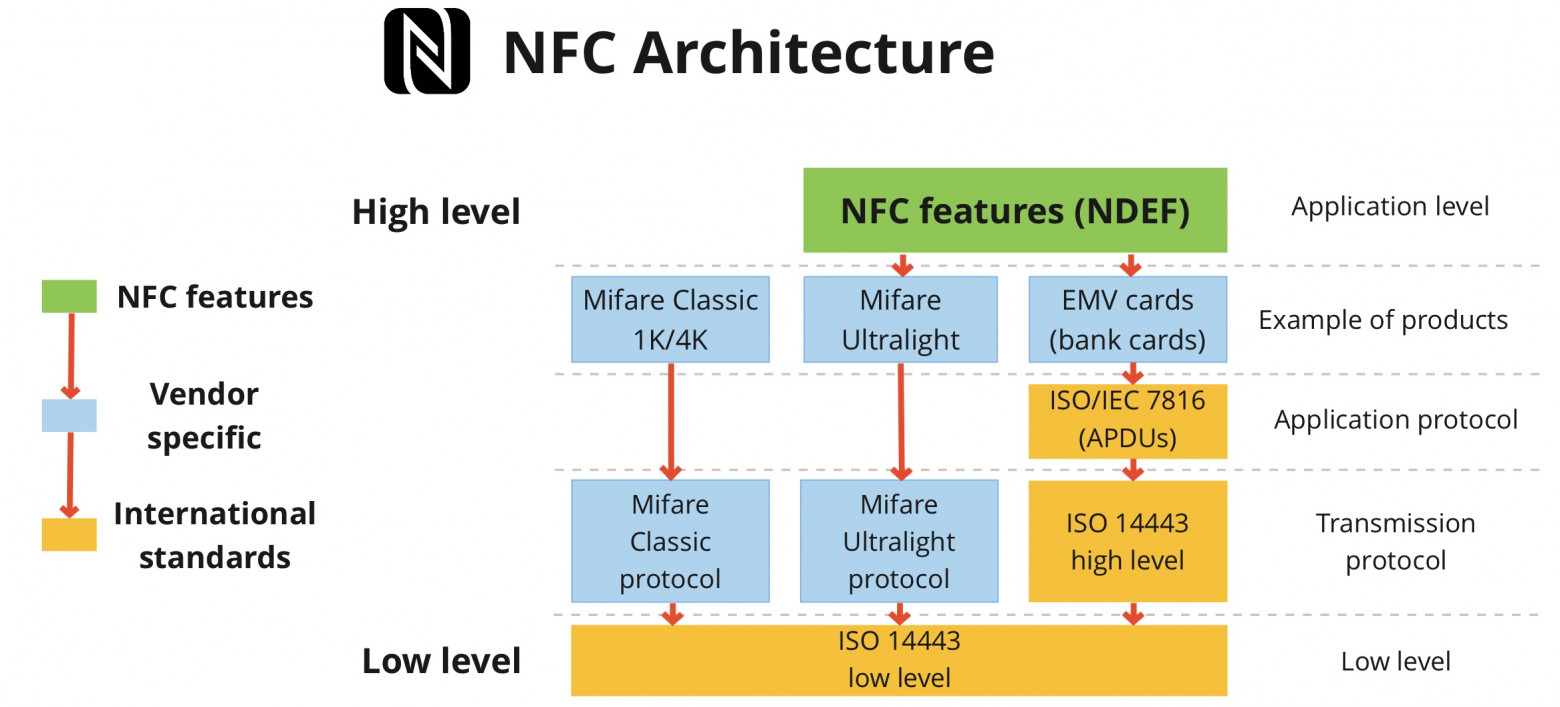 NFC's architecture simplified
NFC's architecture simplified
NFC architecture is simplified
To put it simply, NFC's architecture works like this: the transmission protocol is chosen by the company making the cards and implemented based on the low-level ISO 14443. For example, NXP invented its own high-level transmission protocol called Mifare. But on the lower level, Mifare cards are based on ISO 14443-A standard.
In brief, the architecture of NFC is as follows: the transmission protocol is selected by the card manufacturing company and implemented based on low-level ISO 14443. For example, NXP invented its own advanced transport protocol, called Mifare. At a lower level, however, Mifare cards are based on the ISO 14443-A standard.
Flipper can interact with both the low-level ISO 14443 protocol, as well as Mifare Ultralight data transfer protocol and EMV used in bank cards. We're working on adding support for Mifare Classic and NFC NDEF. A thorough look at the protocols and standards that make up NFC is worth a separate article which we plan to have up later.
Flipper can interact with low-level ISO 14443 protocol, Mifare Ultralight data transmission protocol and EMV used in bank cards. We are trying to add support for Mifare Classic and NFC NDEF. A comprehensive understanding of the protocols and standards that constitute NFC is worth writing a separate article, which we plan to publish later.
Plain UID of the ISO 14443-A Standard
Common UID of ISO 14443-A standard
[Video] Reading a UID from a High-frequency tag of an unknown type
[Video] Read UID from HF tag of unknown type
All high-frequency cards based on ISO 14443-A standard have a unique chip ID. It acts as the card's serial number, like a network card's MAC address. Usually, the UID is 4 or 7 bytes long, but can rarely go up to 10. UIDs are not a secret and they are easily readable, sometimes even printed on the card itself.
All HF cards based on ISO 14443-A standard have a unique chip ID. It acts as the serial number of the card, just like the MAC address of the network card. Generally, UIDs are 4 or 7 bytes long, but rarely reach 10 bytes. UIDs are not secret. They are easy to read and sometimes even printed on the card itself.
There are many access control systems that rely on UID to authenticate and grant access. Sometimes this happens even when RFID tags support cryptography. Such misuse brings them down to the level of the dumb 125 kHz cards in terms of security. Virtual cards (like Apple Pay) use a dynamic UID so that phone owners won't go opening doors with their p ayment app.
Many access control systems rely on UIDs to verify and grant access rights. Sometimes this happens even if RFID tags support encryption. This misuse has reduced their security to the level of a stupid 125 kHz card. Virtual cards (such as Apple Pay) use dynamic UIDs so that phone owners do not use their payment applications to open doors. [Video] iPhone generates a new UID for each time Apple Pay is read
[Video] iPhone will generate a new UID every time it reads Apple Pay
Since UID is a low-level attribute, you might find yourself in a situation when UID is already read, but the high-level data transfer protocol is still unknown. You can read, emulate and manually input UID using Flipper for the primitive readers that use UID for authorization.
Because UID is a low-level attribute, you may find yourself in a situation where the UID has been read but the advanced data transmission protocol is still unknown. For original readers authorized by UID, you can use Flipper to read, simulate, and manually enter UID.
Reading the UID VS Reading the Data Inside
Reading UID VS reading data inside
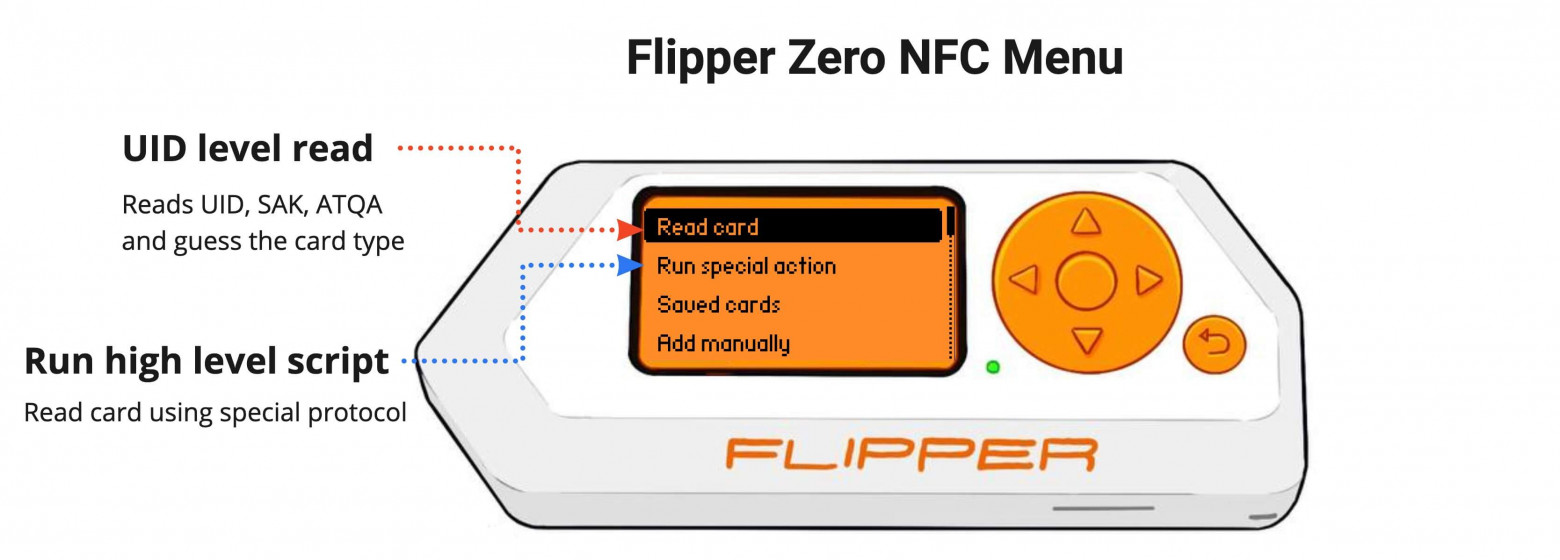 NFC read menu is divided into two parts, low-level read and high-level read
NFC read menu is divided into two parts, low-level read and high-level read
The NFC read menu is divided into two parts: low-level read and high-level read
In Flipper, reading 13.56 MHz tags can be divided into two parts:
In Flipper, reading the 13.56 MHz label can be divided into two parts:
- Low-level read — reads only the UID, SAK, and ATQA. Flipper tries to guess the high-level protocol based on this data read from the card. You can't be 100% certain with this, as it is just an assumption based on certain factors.
Low level read - Read only UID, SAK and ATQA. Flipper tries to guess the advanced protocol based on the data read from the card. You cannot be 100% sure of this because it is only an assumption based on certain factors.
- High-level read — reads the data from the card's memory using a specific high-level protocol. That would be reading the data on a Mifare Ultralight, reading the sectors from a Mifare Classic, or reading the card's attributes from PayPass/Apple Pay.
Advanced Read - Read data from the card's memory using a specific advanced protocol. This will be to read data on Mifare Ultralight, read sectors on Mifare Classic, or read card properties from PayPass/Apple Pay.
To use a specific high-level protocol when reading data go to NFC —> Run special action and choose the type of tag you want to read.
To use a specific advanced protocol when reading data, go to NFC —> Run special action And select the label type you want to read.
To try and guess the type of tag and to read the UID go to NFC -> Read card . So far Flipper can only detect Mifare Ultralight and EMV bank card.
To try to guess the tag type and read the UID, go to NFC -> Read card 。 Currently, Flipper can only detect Mifare Ultralight and EMV bank cards.
Mifare Ultralight
[Video] Reading data off a Mifare Ultralight
[Video] Reading data from Mifare Ultralight
Mifare is a family of contactless smart cards with several high-level protocols. The simplest of those is Mifare Ultralight. In its basic version, it has only 64 bytes of embedded flash memory and no cryptographic protection. Flipper can both read and emulate Mifare Ultralight cards. Such tags are often used as passes granting access to offices, houses and public transport. Moscow public transport tickets for example are using Mifare Ultralight.
Mifare is a non-contact smart card series with a variety of advanced protocols. The simplest one is Mifare Ultralight. In its basic version, it has only 64 bytes of embedded flash memory and no encryption protection. Flipper can read and simulate Mifare Ultralight cards. Such labels are often used as a pass to enter offices, houses and public transport. For example, public transport tickets in Moscow use Mifare Ultralight.
EMV Bank Cards (PayPass, payWave, Apple Pay, Google Pay)
EMV bank card (PayPass payWave、Apple Pay、Google Pay)
[Video] Reading data from a bank card
[Video] Read bank card data
EMV (Europay, Mastercard, and Visa) — is the international standard set for bank cards. Bank cards now are full-fledged smart cards with complex data exchange protocols and support for asymmetric encryption. Apart from simply reading the UID, you can extract a lot more data from a bank card. It's possible to get the full card number (the 16 digits on the front of the card), validity date, and in some cases even the owner's name along with a list of the most recent transactions.
EMV (Europay, Mastercard and Visa) is an international standard for bank cards. Bank cards are now mature smart cards, with complex data exchange protocols and support asymmetric encryption. In addition to simply reading the UID, you can also extract more data from your bank card. You can get the complete card number (16 digits on the front of the card), the effective date, and in some cases, even the owner's name and a list of recent transactions.
Since the EMV standard might be implemented differently, the data that can be extracted may vary from card to card. You can't read the CVV this way (the 3 digits on the back of the card).
Since the EMV standard may be implemented in different ways, the data that can be extracted may vary from card to card. You cannot read CVV (3 digits on the back of the card) in this way.
Bank cards are protected from replay attacks, so copying it with Flipper and then trying to emulate it to pay for something won't work.
The bank card is protected by replay attack, so it is not feasible to copy it with Flipper and try to imitate it to pay for some things.
Tokenized Apple Pay Card VS Physical Bank Card
Tokenized Apple Pay Card VS Physical Bank Card
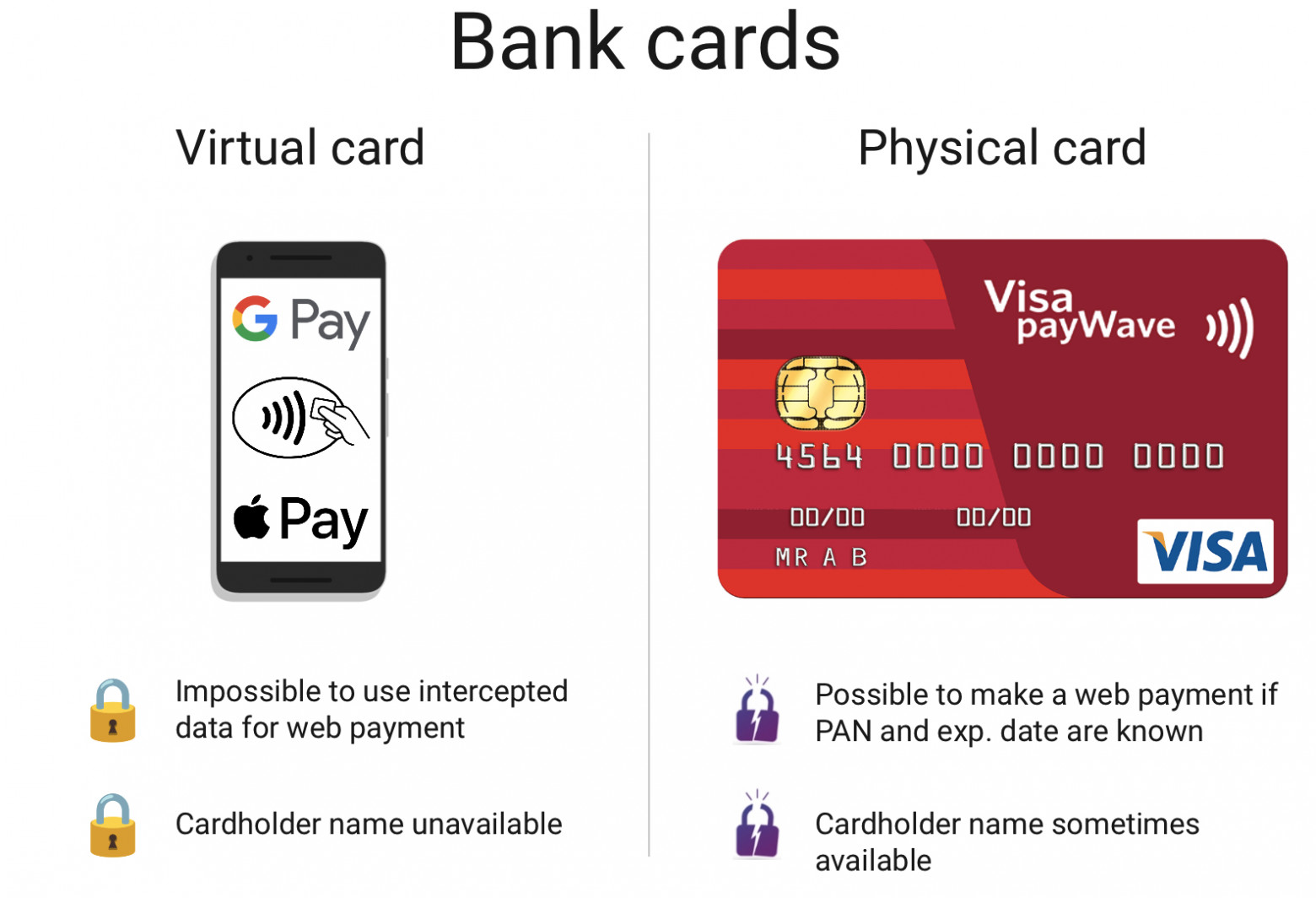 Comparing the security of a virtual bank card and its physical counterpart
Comparing the security of a virtual bank card and its physical counterpart
Security Comparison between Virtual Bank Card and Physical Bank Card
Compared to a plastic bank card, the virtual card you have in your phone provides less information and is safer for offline payments.
Compared with plastic bank cards, virtual cards in mobile phones provide less information, and offline payment is more secure.
Apple Pay and Google Pay have several advantages:
Apple Pay and Google Pay have several advantages:
- They don't allow using captured data for online payments – a normal card can be used for Card-Not-Present transactions (CNP), you can sometimes pay online or on the phone. Intercepted virtual card data can't be used in this manner. After registering a card with Apple Pay all payments go through the virtual token and all operations are cryptographically signed. Reading Apple Pay data results in a PAN and an expiration date of the virtual token, not the original physical card. Thus if someone tries to use the data intercepted from a virtual card to pay online such payment will be declined without a specific signature.
They do not allow online payment using captured data -Ordinary cards can be used for card free transactions (CNP), and you can sometimes pay online or by phone. The intercepted virtual card data cannot be used in this way. After registering the card on Apple Pay, all payments will be made through the virtual token, and all operations will be encrypted and signed. Reading Apple Pay data will generate the expiration date of PAN and virtual token (instead of the original physical card). Therefore, if someone tries to use the data intercepted from the virtual card for online payment, such payment will be rejected without a specific signature.
- They don't disclose the card owner's name — some contactless cards can transfer the cardholder name and recent transactions data. Virtual cards don't do that.
They won't reveal the name of the cardholder -Some contactless cards can transmit cardholder names and recent transaction data. Virtual cards cannot do this.
Bank card support in Flipper is implemented exclusively for high-level protocol demonstration purposes only. We do not plan to extend this function further. Contacts bank cards security is good enough not to word that devices such as Flipper can be used to attach bank cards. We do not intend to further extend this functionality. The security of the contactless bank card is good enough, so you don't have to worry that Flipper and other devices can be used to attack the bank card.
]]>