
Recently, CCTV 315 Evening Party exposed many enterprises' violations of laws and regulations, such as Burger King using expired bread to make hamburgers, and the difficulty of refunding fees on Hixue.com. The exposure of each problem is not only closely related to our life, but also makes people gape.
In particular, in terms of privacy security, the 315 party exposed more than 50 applications to steal users' personal privacy, causing hot debate, and users' privacy security once again became the focus of our attention. So, how can we effectively avoid privacy disclosure? The following uses mobile phone Software We must pay attention to the habits of.

01 It is impossible to prevent the thief plug-in hidden in the mobile phone
The SDK is a "software development kit", a collection of development tools, which can be used for specific software packages Application software , software framework, hardware platform, operating system and other products. In short, it can help the software to achieve certain functions, with the ability to read, store, and transmit data.
This time, CCTV exposed that some criminals used the SDK to read IMEI, IMSI, operator information, phone number, SMS record, address book, application installation list and sensor information of mobile devices, and transmit these private information to other servers in order to steal users' private information.
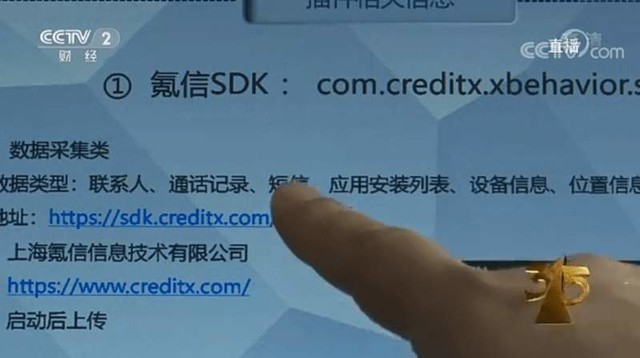
Source: CCTV Finance
Technicians have tested more than 50 mobile phone software, all of which are suspected of stealing users' privacy without their knowledge. Unconsciously, their information is transmitted to other places. If it involves the disclosure of transaction verification codes such as money transfer, it is frightening to think about it.
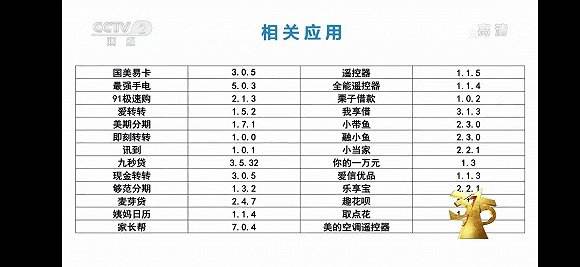
Some applications exposed by CCTV to steal user privacy
Then, in the face of these problems, we must develop the following habits to effectively avoid information leakage.
02 How to effectively prevent?
Application permission management
When we think about APP privacy, we will think of "permissions". Yes, APP permissions are like a lock. But most people download After a new APP is launched, it is generally allowed.
You may say that most applications can't be used without clicking "Allow", but it's obviously wrong to click "Allow" all the way. The permission of the application should be selectively opened, and it is not allowed to be lazy to agree with all applications, especially those that are unfamiliar or involve money.
For example, it is unnecessary to turn on the microphone, camera and location information for some APPs, so it is unnecessary to click Allow. If you didn't agree with all of them before, it is recommended that you check them carefully, especially those "unknown" APPs. Open [Application Permission] to view them.
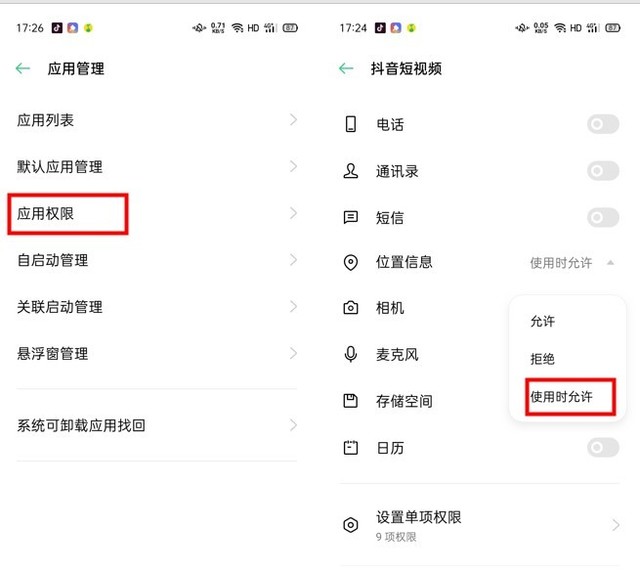
For example, you can select "Allow only during use" for location information, and prohibit microphone, phone, SMS, camera and other unnecessary items.
Download applications via official channels to avoid malware
Unlike in the past, mainstream mobile phone brands now have their own "software stores", which can only go home after the official security audit, so the security is guaranteed. We'd better choose official channels for downloading applications, and third-party platforms should also choose formal ones.
Mobile data cleaning
Many people will choose to recycle or resell their mobile phones after they have been used for a long time. At this time, personal privacy information stored in old mobile phones is very important. Although the formal third-party recycling agencies on the market will specifically clean up personal information, they are not afraid to do so in case of emergency. It is reassuring to clean up in advance.
The most effective method here is Storage Overrides 。 The old phone data is cleared, and then the factory settings are restored. Then download other videos, pictures and applications again until the phone's memory space is full. Here, continue the previous steps, clear and restore the factory settings, and repeat the operation several times.
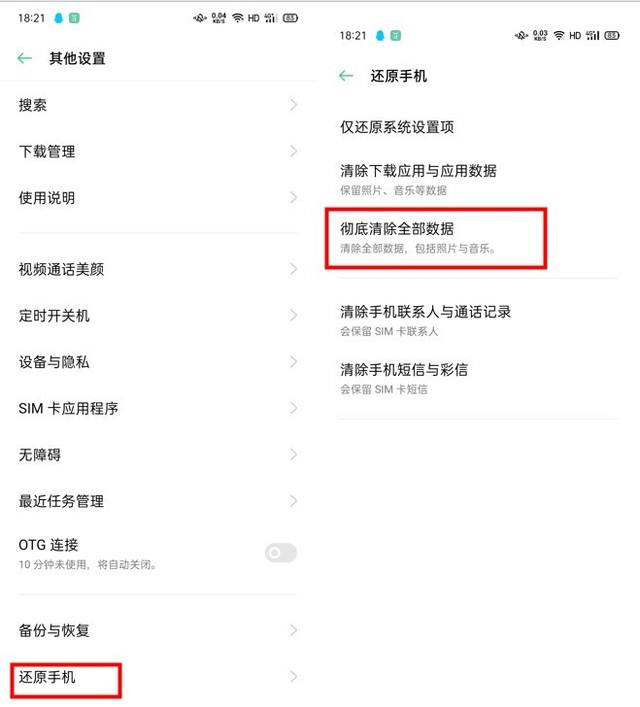
Although it seems troublesome, the direction of storage coverage can effectively avoid the disclosure of personal information, and third-party recycling agencies generally use this method to help users clean up personal data.
Write at the end
It has to be said that the risk of privacy leakage in personal mobile phones is ubiquitous in daily life, which reminds us to form the habit of using mobile APP correctly. What's your best way to prevent cell phone privacy leakage? Welcome to leave a message to share~
Recommended hot engine of Xiaomi today:
Redmi K20 Pro Snapdragon 855 mobile phone drops by 300 yuan, starting from 2099 yuan>>
A limited time discount of 200 yuan for Xiaomi 9 "Xiaolong 855", which is both good looking and can play, and the purchase price is 2599 yuan>>
48 million ultra wide angle three camera mobile phone Xiaomi CC9 new product comes into the market at 1799 yuan+6 interest free>>
At RMB1299, you can have a flagship photography experience, Xiaomi CC9e, buy now>>
Xiaomi CC9 Meitu customized version 32 million beauty selfie fairy exclusive mobile phone price 2599 yuan>>
48 million photo taking machine Red rice Note7 Pro, 6GB version down 200 yuan, only 1399 yuan>>
Xiaomi MIX 3 slide full screen mobile phone has a limited time direct drop of 600 yuan, and the 8GB version only sells for 2999 yuan>>
Xiaomi 9 SE 48 million ultra wide angle three shot, 128GB large capacity version received 1799 yuan>>
This article is an original article. If it is reproduced, please indicate the source: 315 Party Exposes More Than 50 Kinds of Software Stealing Users' Privacy How Should We Protect Yourself? //mobile.zol.com.cn/749/7491339.html
//mobile.zol.com.cn/749/7491339.html
mobile.zol.com.cn
true
Zhongguancun Online
//mobile.zol.com.cn/749/7491339.html
report
three thousand four hundred and twenty-seven
Recently, CCTV 315 Evening Party exposed many enterprises' violations of laws and regulations, such as Burger King using expired bread to make hamburgers, and the difficulty of refunding fees on Hixue.com. The exposure of every problem is not only closely related to our life, but also makes people gape. In particular, in terms of privacy security, the 315 party exposed more than 50 applications to steal users' personal privacy, which caused heated debate. Users



















